
When creating a new password, you know the drill – it must be at least eight characters long, contain special characters and avoid sequential characters or be based on dictionary words. Although these requirements can be a pain in the neck and seriously hamper end user experience, they are not a sign of officious IT security teams. Instead, they are a necessary evil in modern enterprises because password cracking remains a viable vector for threat actors, and passwords are some of the most vulnerable targets for attackers.
By obtaining valid password credentials, attackers can stealthily infiltrate systems, escalate their privileges to an administrator or superuser level and wreak havoc on an organization’s security, reputation and bottom line.
To counter this, enterprises have increasingly adopted multi-factor authentication (MFA) to prevent users from logging into applications, corporate networks and resources without entering an additional form of verification. For instance, users may be asked to verify their login attempts by supplying a code via email, approving their login request in the authenticator app or tapping a smart card.
Unfortunately, threat actors have numerous tools in their arsenal to bypass MFA protections, including stealing cookies, employing social engineering or using MFA fatigue-based attacks. This brings us to square one: exposing passwords as the weakest security link.
But what if there was no password to start with? This would mean no infuriating password complexity requirements to adhere to, no periodic password updates, no password rests and, most importantly, no passwords for attackers to steal.
Passwordless Authentication Gains Traction
While the concept of passwordless authentication has been around for a long time, the market has just recently pivoted to actively using the technology. Passwordless authentication can use any means of validating the user except for a memorized secret. It could be a QR code displayed at login, an SMS message with a one-time code or a physical USB key, among other examples.
In the back-end, passwordless authentication relies on the same principle as digital certificates that use public and private keys. Think of the public key as the door and the private key as the key that unlocks it. With passwordless authentication, there is only one key for the door and only one door for the key. In one scenario, a user wants to create a secure account and uses a mobile authenticator app to generate a public-private key pair. The public key is provided to the system, and the private key is accessed from the user’s local device using an authentication factor such as a QR code.
Passwordless authentication offers a better user experience and improved productivity by providing a more seamless sign-in experience. It also increases security by eliminating password-related risks. As a side benefit, it also reduces IT overhead by freeing up resources used to assist end users with account unlocks and password resets.
While passwordless technology promises significant benefits, it’s important to understand that the journey to passwordless authentication is unique to the requirements of every business.
Why Going Passwordless is a Marathon
The hard reality is that no organization can go passwordless from day one. Most enterprises won’t ever be able to go completely passwordless. There are just too many legacy systems deeply entrenched in IT infrastructure that require passwords. So, it’s about finding the balance of what makes sense from a security, effort and cost point of view.
Going passwordless is no small task, especially when organizations deal with thousands of users, countless applications, hybrid and multi-cloud environments and complex login flows. Achieving an entirely passwordless environment involves a phased approach as technology continues to evolve and user adoption increases.
The following graphic encapsulates CyberArk’s view of a typical trajectory from passwords to passwordless while delivering a frictionless user experience.
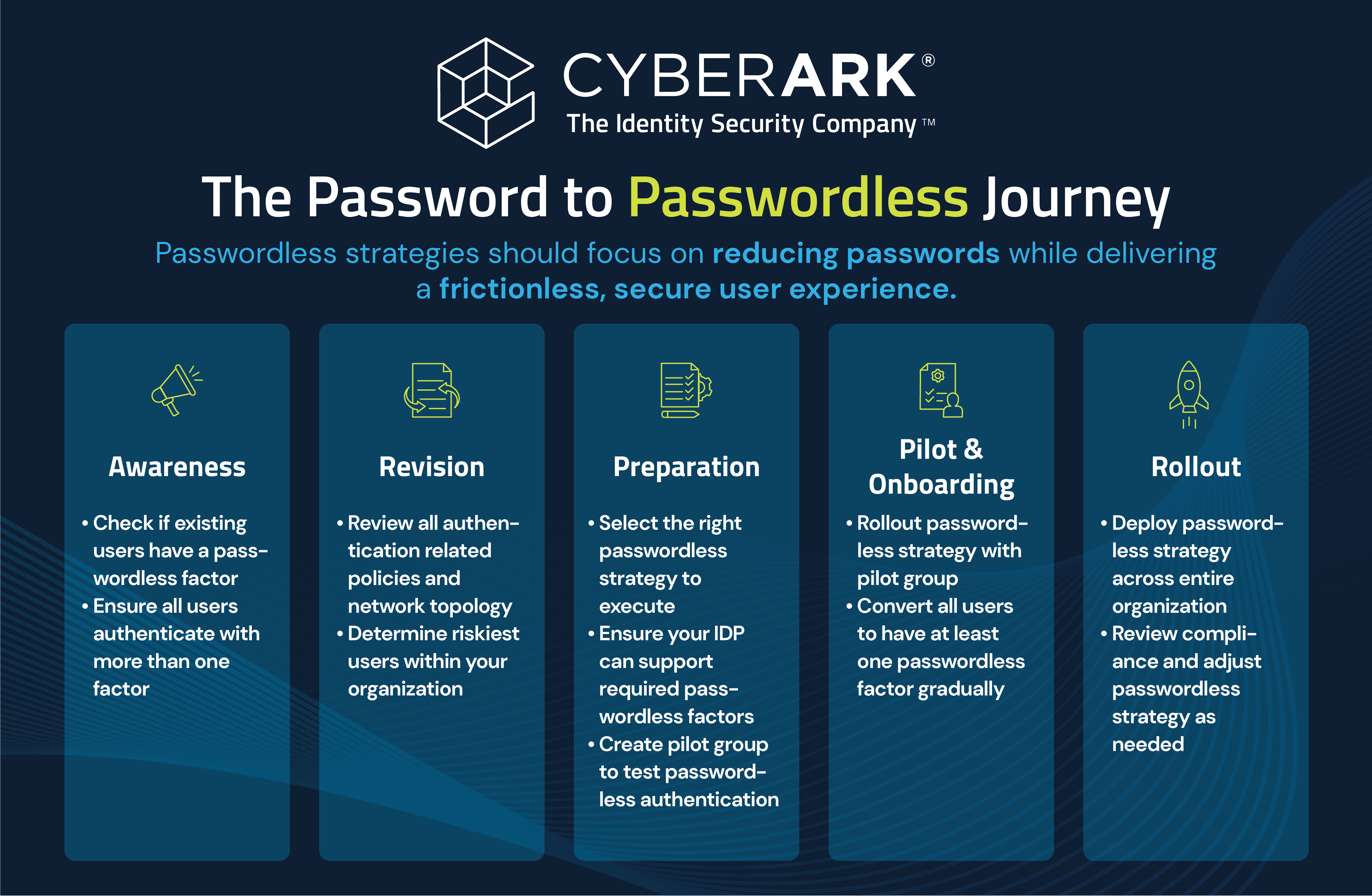
Organizations must understand that not all passwordless experiences are created equal and its success depends upon selecting the best authentication factors that align with the business and user needs. Although eliminating passwords entirely is far off, reducing reliance on them is feasible by implementing the right IAM solutions that support passwordless use cases.
When considering IAM solutions, look for the following capabilities:
- Zero sign-on (ZSO). The first pillar of a true passwordless solution, ZSO, uses strong cryptographic standards such as certificates and combines user identities with contextual information such as device fingerprints and security posture. The key benefit of ZSO is that it enables users to seamlessly log in to their assigned applications and services without additional authentication once their devices are verified and meet security posture requirements. Remember to combine ZSO with other passwordless authentication factors best suited to your business requirements to enhance usability and security.
- FIDO2 integration and support. Almost every identity vendor supports FIDO2 Web Authentication (WebAuthN) and this standard is critical to enabling passwordless authentication for typical end users. Along with FIDO2, FIDO’s passkeys are a new multi-device passwordless factor that uses your devices’ security capabilities, further improving user experience. In addition, passkeys are highly phishing-proof and eliminate attack vectors possible with factors like MFA that require human interaction.
- Passwordless endpoint authentication. In a multi-device world, it’s essential to approach authentication to endpoints in the same way as applications and internal resources. Passwordless endpoint authentication can provide a better user experience and stronger security without negatively impacting user productivity.
- Secure VPN access for remote and hybrid users. As a critical security control to enable secure remote and hybrid user authentication, it’s recommended that users use adaptive MFA when accessing a corporate network through a VPN. Enforcing MFA for VPNs secures remote access to your corporate network, on-premises applications and resources while delivering a frictionless-yet-secure login experience that continuously evaluates and steps up with passwordless factors – as needed – based on contextual and risk analytics.
- Self-service passwordless authenticator replacement. For a true passwordless experience, it’s crucial to implement a solution that offers users the ability to self-enroll, replace and delete passwordless authenticators with the appropriate security controls, along with a wide variety of alternative passwordless authenticators to choose from. For instance, suppose a user were to lose their YubiKey or misplace their mobile phone. In that case, the user should be able to replace the passwordless authenticator factor from various factors with the appropriate security controls.
Planning For Passwordless
As with any security-related undertaking, going passwordless requires strategy, planning, partnership with trusted vendors and a disciplined move toward organizational adoption and continued education. Leadership backing is an absolute must to drive this initiative, as is the choice of an experienced and well-established vendor that supports the journey to passwordless.
As you think of taking your organization passwordless, consider the following:
- What use cases are most suited for passwordless authentication?
- Who are the riskiest users in the organization?
- What passwordless factors offer the right level of security and convenience?
- What’s the best way to pilot and scale the elimination of passwords without business disruptions or introducing additional risk?
When you engage with an IAM provider, do not hesitate to ask them about their idea of a true, holistic passwordless solution — and what innovation and intellectual property they have invested in to make that a reality. Finally, remember that passwordless authentication is just a piece of the enterprise security puzzle. Make sure your IAM partner can support your current and future identity security needs.
Amita Potnis leads thought leadership marketing at CyberArk.























