
Many of us took ChatGPT for a first-time spin just 12 months ago. Then someone hit the speed multiplier button, and just like that, we’re exiting 2023 with whiplash. Generative artificial intelligence’s (GenAI) breakout year was both exciting and unnerving for cybersecurity professionals who understand that technological change and cyber risk are inextricable. Meanwhile, dramatic shifts in the physical world reshaped the threat landscape, redirected cybersecurity strategies and sparked regulatory reforms. Yet some things didn’t change, like attackers’ relentless pursuit of identities and proven ways to steal and use them.
Our team came together to discuss how 2023 trends will impact 2024 and beyond. Here’s a look at our year-by-year predictions based on CyberArk research, customer and partner interactions and industry collaborations.
In 2024 …
Session hijacking will take on an increasingly prominent attack role …
Even more organizations will shift to passwordless access management, from passkeys to MFA, to help thwart attacks. Threat actors will evolve their tactics in lockstep to dupe enterprise and third-party users, steal session cookies and bypass strong authentication mechanisms. Their creativity will pay dividends; by 2024, session hijacking will account for 40% of all cyberattacks. Continued vigilance in securing, monitoring and responding to user sessions and cookies abuse/compromise is critical – especially with Google’s encouraging promise to wipe out cookies for good, never underestimate innovative attackers who will find another way.
… but 30% of organizations will pay for lax password protections.
Traditional credential theft will be less prevalent when passwordless takes hold and is used correctly. Yet, credential theft isn’t going away. Why? Organizations implementing passwordless authentication may require a backup factor, and many companies will fall back on insecure options – passwords. As security teams fight new fires, attackers will take advantage of lax password protections, and 30% of organizations will experience an increase in data breaches linked to credential theft.
55% of enterprises will expedite tech consolidation to simplify security.
Most organizations’ IT and security environments are already too expansive, complicated and difficult to manage. Teams are rarely skilled in every tool they must cobble together with other ones, forcing them to hire or bring in outside experts. And since each platform focuses on specific things and overlap with others, teams struggle to see – let alone understand – every potential vulnerability and threat in their cloud-centric environments. Missed SLAs, spiraling overheads and dangerous security drift will push 55% of enterprises to accelerate tech consolidation. They’ll aim to simplify operations and maximize existing resources by working with fewer vendors and systems.
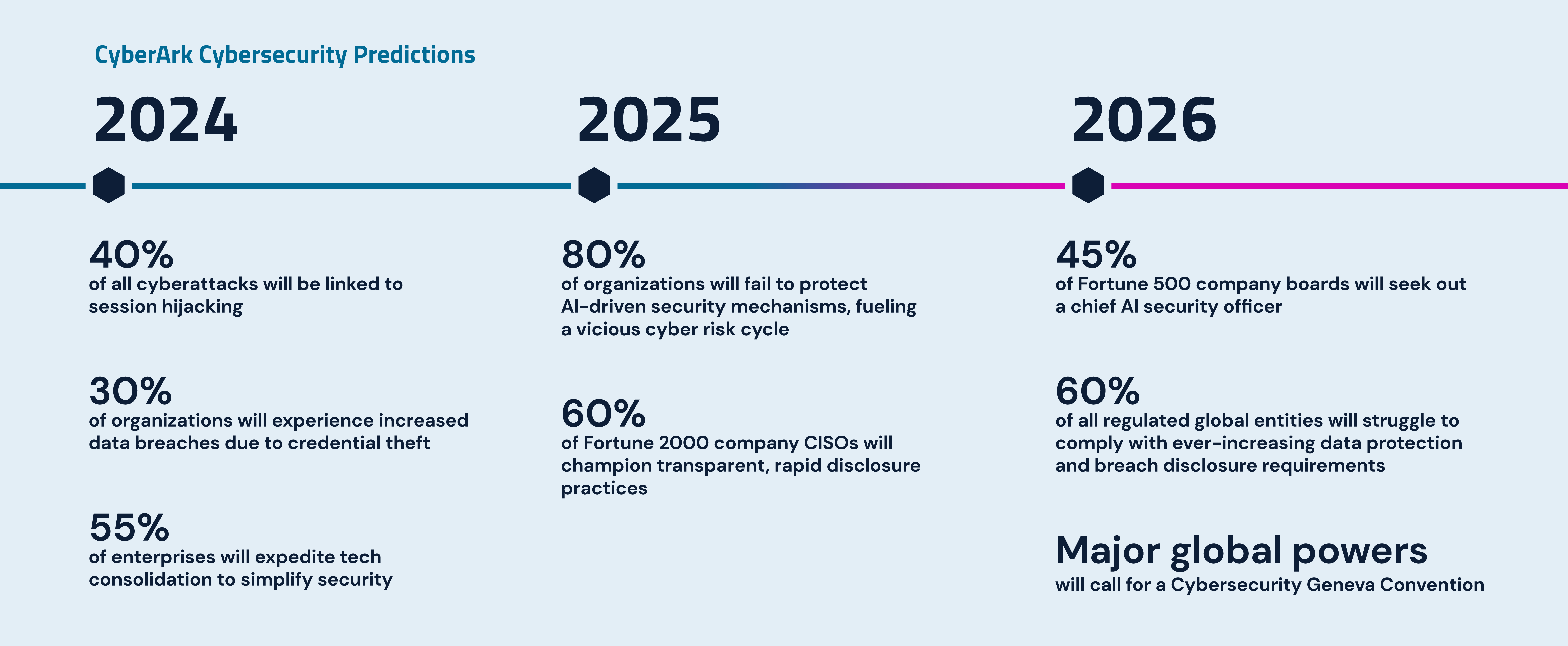
By 2025 …
Unprotected AI-driven security mechanisms will fuel a vicious cyber risk cycle.
Though organizations are embracing GenAI to bolster cyber defenses, 80% will fail to protect these same AI-based security models – fueling a vicious cyber risk cycle. Gaining an edge on attackers will require an adversarial mindset, from training GenAI models with both offensive and defensive samples to adopting model assurance and regular stress testing (including red teaming and pen testing). Hosting these AI models in highly secure environments with highly secure access protections will be equally critical. Governments will issue forward-thinking guidelines on this front, yet organizations can’t wait for codified standards that may quickly become outdated. Embedding GenAI in product security must happen now.
Under pressure, CISOs will advocate for timely, transparent breach disclosures.
Cybersecurity accountability is getting personal. First, Uber’s security chief was charged with failing to disclose a 2016 data breach to federal regulators. This fall, the SEC charged SolarWinds and its CISO with fraud and internal controls failure in a landmark that comes on the heels of the agency’s ruling on tighter cybersecurity disclosure requirements. Security leaders around the world are watching closely. By 2025, 60% of Fortune 2000 company CISOs will champion transparent, rapid disclosure practices – not just because of policy but because their careers and reputations are on the line.
By 2026 …
Nearly half of Fortune 500 company boards will seek out a chief AI security officer.
Cybersecurity isn’t an IT issue; it’s the fulcrum of business resilience and stakeholder trust. Most Fortune 500 organizations recognize the high stakes and are beefing up cybersecurity aptitude at the corporate director level. Emerging AI risks are driving an even greater sense of urgency. By 2026, 45% of these enterprises will recruit and work to appoint a chief AI security officer to the board. This leader will possess both technical expertise and business acumen, playing an influential role in advancing AI innovation, managing resulting risks and safeguarding the AI-based security models. They will be deeply entrenched in cybersecurity strategy and expand oversight and reporting mechanisms to better measure and improve security initiatives, risk assessments and incident response plans.
Multinational organizations will face a regulatory reckoning.
Sixty percent of all regulated global entities will struggle mightily to comply with ever-increasing data protection and breach disclosure requirements, especially as GenAI use cases expand. More organizations will face non-compliance penalties as regulators’ bite catches up to their bark. Consider that today, failure to comply with the European Union’s GDPR alone can cost organizations as much as €20 million or 4% of annual global turnover, whichever is higher. Already hefty fines will continue to climb with potentially crippling impact.
Major global powers will call for a Cybersecurity Geneva Convention.
Sophisticated nation-state attacks, particularly those targeting critical infrastructure, can result in widespread disruptions, life-threatening outages and rippling damage across software supply chains. Growing concerns of escalation to conventional warfare will prompt major global powers to take dramatic steps to enhance cyber resilience, legal frameworks and international cooperation. As part of this, these countries will push to establish a Cybersecurity Geneva Convention to deter nation-state attacks and hold perpetrators responsible.
2023 threw some major curveballs. But it also reminds us that strong cybersecurity programs don’t swerve or stall in reaction. They’re agile enough to stay in the game, continuously refining practices, making strategic, risk-based investments and proactively preparing for whatever comes next.























