I’m sure your network’s security is top-notch.
You must have already taken care of micro-segmentations, strict firewall policies, and have some kind of EDR solution on the different endpoints. And of course, you’re only allowing secure connections that rely on encrypted protocols.
If you are one of those who take security seriously, you might even run a regular security update routine. And if that’s not enough, you probably also have a qualified SOC team that monitors all of those systems 24/7. Your SOC team submits a report each week that shows several security events that appeared in the different systems but were all examined and characterized as false-positives.
Having said all that — do you feel secure?
In this post, you’re going to learn three stealthy attack techniques you should anticipate and work to avoid. More than that, it’s important that you learn how to expand this knowledge in a way that allows you to protect your network. In order to do that, we will first dive into the mind of a hacker and understand their strategy.
Hacker’s Perspective
As a white-hat hacker and former red teamer, I can tell you that one of my main goals in an operation is to stay secretive. Staying secretive is an important ingredient of an APT (Advanced Persistent Threat) attack, which features a stealthy threat actor.
The Art of Cyber Warfare
If I had to highlight one key feature of a skilled attacker, it would be patience.
“If it is to your advantage, make a forward move. If not, stay where you are.” – Sun Tzu, The Art of War
An attacker who succeeded in passing your first line of defense and gained initial access will strive to evade existing defense systems. They will not make a move until they are certain about it. And more than that, when they do make a move — they will make sure that you are unaware of it.
“Make your way by unexpected routes and attack unguarded spots.” – Sun Tzu, The Art of War
Strolling in the Dark
It all depends on the attacker’s intelligence data.
The easy scenario is when the attacker has enough information to make a decision about their moves and plans ahead.
The more problematic scenario is when there’s not enough intelligence data. In this situation, the best way for an attacker to remain under-the-radar is to utilize the “must-have” features of an organizational network, such as shared folders, ping messages, and DNS queries.
Why would an attacker use those? Because these are protocols that are very frequently used, so it doesn’t require pre-operation intelligence. They shed light on unknown paths.
Even if one of your defense systems catches something unusual, chances are your SOC team will have a hard time investigating exactly what happened. Searching for an unusual pattern in the network traffic of these protocols is like looking for a needle in a haystack.
In the upcoming section, I’ll explain 3 examples of common protocols used by an attacker to their advantage:
1. SMB protocol — enables the shared network folder
2. DNS protocol — enables the translation of domain names to IP addresses
3. ICMP protocol — enables, inter alia, sending ‘ping’ messages
Let’s Talk Business
SMB and Shared Network Folders
It’s a common feature of most networks to have some kind of a shared drive, to allow users to share files with each other and to have a backup of a locally saved file.
This service will be open, most of the time, to a wide range of users and systems. It can, therefore, be used as a tool for breaking down your micro-segmentation and firewall rules.
The way a hacker would use a shared drive is by creating a file in a shared folder that will act as a “pipeline” between a Command & Control (C&C) server and an agent. Even if the agent is running on a machine that isn’t allowed to speak with the C&C, it’s more than likely that the two of them can find a shared folder where they can share such a “pipeline” file with each other.
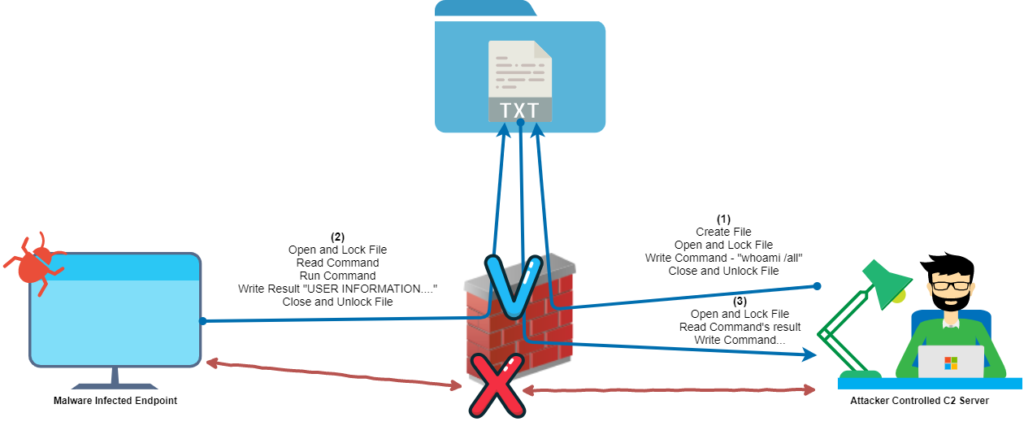
Figure 1. Breaking network segmentation using shared network folders
DNS Beacons
DNS beacons are a well-known technique used to hide the payloads of a session between a C&C server and its agents.
It uses the DNS protocol to bypass firewall rules and relies on the massive amount of DNS queries to “blend into the crowd”.
How does it work?
The agent sends a DNS query to the local DNS server. The query looks like a machine asking for a domain name translation, when in fact, the name server that answers those queries is controlled by the attacker.
In this way, the attacker can respond with any desired payload, in the DNS TXT type record for example, and that will reach the agent.
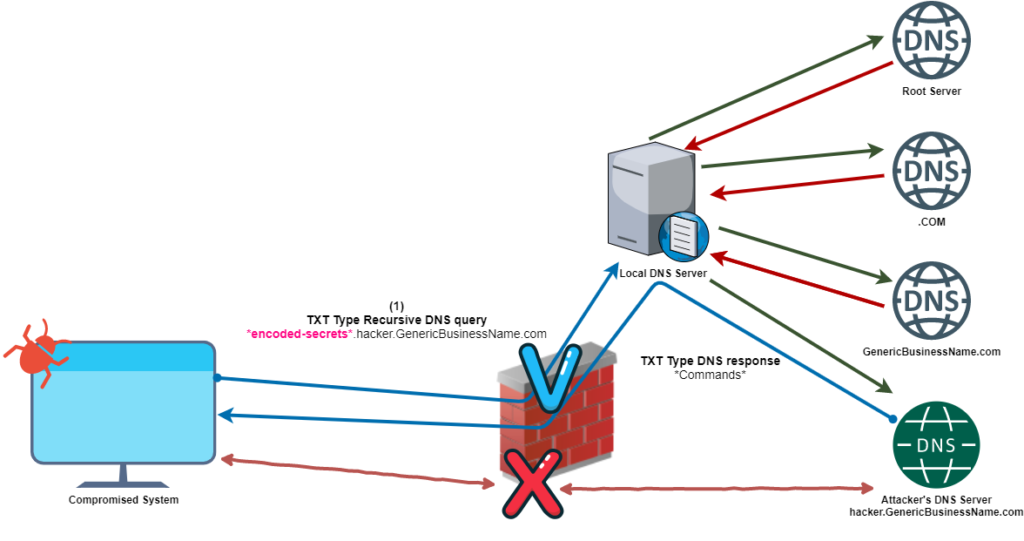
Figure 2. Bypassing firewall rules using DNS queries
Just imagine your crown jewel DB server, leaking the most valuable information, drop by drop, one DNS query after another.
ICMP Tunneling
Last but not least is a simple technique in which a hacker uses the payload section of the ICMP ping packet in order to pass whatever payload they would like.
Regular Linux ping echo message:
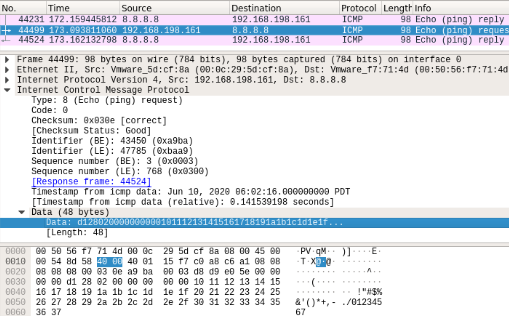
Figure 3. Ping echo message
Manipulated ping echo message:
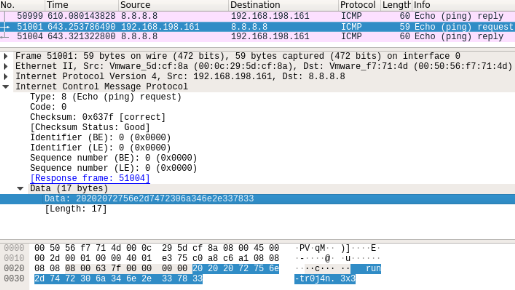
Figure 4. Manipulated ping echo message
Ping packets are mostly allowed to pass between different endpoints on the network. It’s an everyday tool that IT teams use to troubleshoot network faults — that’s exactly why it’s a great way to bypass network policies.
Similar to SMB and DNS, the amount of ICMP packets sent on the network is huge, making this method hard to detect.
Now What?
So, what can you do against these types of attacks?
Keep your enemies close, but your friends closer — using a firewall to filter the types of traffic that you don’t use is the easy part. But what are you going to do with the traffic you allowed to pass?
Two main methods worth pointing out that can help address these challenges are:
1. Deep Packet Inspection (DPI) — as a security feature in your network can go a long way to detecting the malicious use of packets to transfer payloads, such as DNS beacons and ICMP tunneling
2. Behavioral-based security — an automated proactive approach, in which you can detect behavioral anomalies in your network, such as 2 machines going back and forth from the same file on a shared folder (sound familiar?)
The most important issue here is that you need to embrace the perspective of an attacker on your network.
Look for the properties on the network that are “obvious,” the trivial types of traffic, and those that are difficult to filter out the unusual patterns.
Good luck!























