
Cybersecurity is no longer just a technical concern; it’s a business-critical investment. Yet, gaining the C-suite’s backing often hinges on one essential question: “What’s the ROI?”
Proving the value of your identity security program goes beyond talking about threats—it involves showcasing measurable outcomes. From reducing cyber risks and simplifying compliance to boosting efficiency and fortifying business resilience, strong programs deliver tangible results that matter to executives—not just the “we didn’t get breached” statement. Better yet, by tying cybersecurity directly to the organization’s bottom line, you can bridge the gap between technical priorities and business goals, securing the buy-in you need to drive long-term protection and growth.
When it comes to securing identities, the stakes are high, and so are the expectations from the C-suite. Company leaders look for clear proof that investments in security programs aren’t just necessary but truly deliver measurable value—whether it’s the material reduction of risk or operational excellence. All good stuff, but how do you persuasively demonstrate this return on investment (ROI)?
It’s important to examine how identity security programs reduce cyber risks by protecting your organization from costly breaches, streamline audit and compliance efforts to keep regulatory pressures in check and boost operational efficiency by simplifying processes. Beyond those immediate benefits, identity security also plays a critical role in strengthening business resilience in the face of evolving threats and disruptions.
It begins with an examination and alignment of the common values that likely spawned your identity security journey. Perhaps it started as a desire to protect that organization from costly breaches, or maybe it was to streamline audit and compliance to keep regulatory pressures in check. It could have been because you wanted to streamline user workflows or simplify processes. Once you have that inventory, the next (often forgotten) step is to tie these benefits to measurable outcomes. That’s the key to being better equipped to show your C-suite why identity security matters, how it drives long-term value for the organization and how it can help prepare them for these board-level conversations.

What Types of Measurements Should You Care About?
You’ve gotta have metrics to demonstrate the value of current and future efforts and to align expectations across operational teams and leadership. Metrics are not just numbers; they tell stories that help stakeholders, from program managers to CISOs, understand, measure and enhance their organization’s security posture.
Effective cybersecurity programs categorize metrics and KPIs in a hierarchical structure to meet the needs of various audiences within the organization. For example, program managers need detailed, granular metrics, while directors and vice presidents require metrics that provide broader insights into overall performance and risks. This includes ROI data to communicate the effectiveness of security programs and the business value. On this point, enabling IT and security teams to be more efficient and improving productivity are significant outcomes for an identity security program.
What are the most important areas to evaluate? Obviously, these are the ones that impact your unique business the most. For each identity security area, like access management, lifecycle management, privileged access management (PAM), secrets management, endpoint identity security and Identity Threat Detection and Response (ITDR), organizations should define success metrics that align with specific KPIs and milestones in their identity security program.
These metrics help organizations answer the question, “How am I doing compared to my target?” and should align with specific objective key results (OKRs) defined with security team leadership and mapped to the program roadmap.
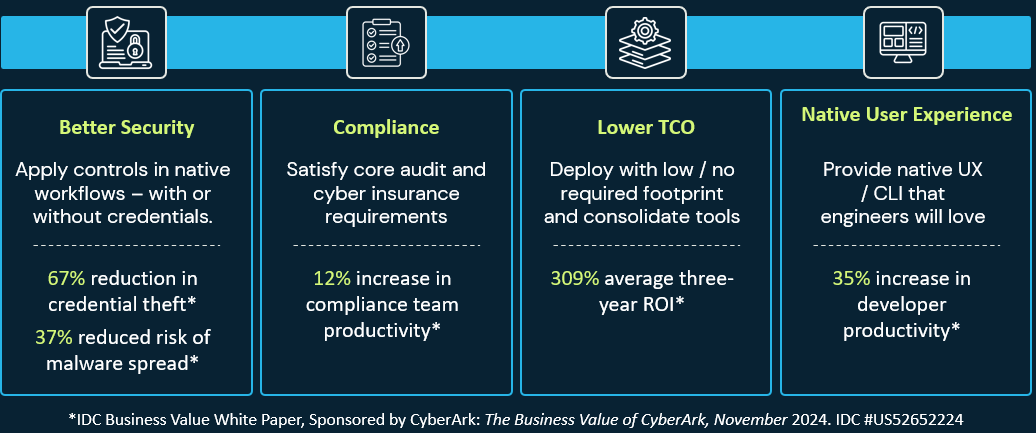
What Fantastic Looks Like: 309% ROI
In the past, using ROI and security controls in the same sentence was aspirational at best, but things have changed! Achieving a high ROI from identity security investments can be done with a strategic approach enriched by advanced capabilities. To support meaningful adoption, organizations should select an identity security platform offering comprehensive capabilities, such as secure access to resources with both vaulted credentials and zero standing privileges (ZSP), in addition to native user experience and session isolation/brokering. Scalability is another key concern, as organizations must ensure their technology can scale without incurring extra costs. And automating the management of a rapidly growing population of machine identities is another great way to realize efficiency gains in productivity.
To test the true value of identity security (and to help offset our own biases), we commissioned IDC to conduct a study interviewing CyberArk customers and analyzing the results of their deployments to assess the ROI. The research published in the IDC White Paper, “The Business Value of CyberArk,”* highlights how identity security can effectively secure human and machine identities and access to workloads in hybrid and multi-cloud environments.
Here’s what the IDC White Paper found:
- Average ROI of 309% over three years.
- Annual productivity and cost savings benefits worth $3.1 million.
- An average of recovered initial investment within 10 months.
These financial gains are driven by the organization’s ability to streamline processes, enhance security and improve overall business resilience. It helps organizations detect, respond to, remediate and recover from identity-based threats and enables proactive, right-sized privilege controls for human and machine identities.
When discussing the tangible benefits of identity security programs, it’s important to consider real-world experiences from organizations that have successfully implemented these solutions (unless you’d just like to take our word for it!). For instance, in the IDC White Paper one financial services company highlighted the efficiency and regulatory advantages of using a standardized, centralized tool:
“Having a standardized, centralized tool creates a lot less overhead and allows my organization to demonstrate to regulatory bodies that we are effectively layering information security. Importantly, CyberArk ensures that we are doing this cost-effectively.“
Similarly, in the IDC White Paper an insurance provider emphasized the consistency and ease of extending privileged access management during their cloud migration:
“The most significant benefit of CyberArk is the consistency it gives my organization in terms of privileged access management. We are going through a cloud migration, and extending CyberArk to the cloud and not changing the process has been extremely helpful.”
How to Achieve 37% Lower Malware Spread with 67% Fewer Account Takeovers
Organizations can better protect themselves against cyberthreats and ensure business continuity by regularly reviewing and updating access controls, implementing the principle of least privilege (PoLP) and using advanced analytics to detect and respond to threats in real time.
Visibility is important, but visibility without remediation is only admiring the problem. After discovering accounts and roles and analyzing the associated risk, organizations should secure them by applying privilege controls in line with their risk. Consistent session isolation and access policies should be applied without sacrificing the native user experience to maintain security and visibility.
A key finding of the IDC White Paper was the significant improvement in security and business resilience that CyberArk customers have achieved. The platform, along with the right changes in process and the implementation of better hygiene, has helped organizations reduce account takeover attacks by 67% and over-privileged accounts by 60%. Additionally, there has been a 37% reduction in malware spread from native session management—allowing end users to leverage their existing clients and workflows while reaping the isolation benefits.
Tracking Efficiency Gains: 49% for IT and 30% for Machine Identity Management
Organizations should focus on streamlining operations and reducing complexity to ensure that both security and productivity grow equally. This effort includes automating routine security tasks, integrating your identity security solution with other IT systems and providing employees with the tools, training and documentation needed to work securely and efficiently.
When searching for an identity security solution, security leaders should focus on platforms offering seamless integration with existing systems and providing comprehensive support for human and machine identities. No single platform can do it all, and the goal should be to multiply the value of other solutions and vendors in your ecosystem. Their chosen platform should enable them to automate workflows, reduce manual intervention and enhance team collaboration while maintaining strong security standards.
Real-World Success Stories
Key ingredients for identity security success are learning from others’ experiences, continuously evaluating and improving security measures and sharing internal success stories to promote a security culture. Security leaders should build strong partnerships with their providers and collaborate with vendors to tailor solutions to their needs. They can also benefit from participating in user communities to share knowledge and best practices and leveraging vendor expertise to stay ahead of emerging threats.
Organizations must modernize their identity security programs as security threats evolve to maintain a competitive edge. They should look for a trusted partner with a proven solution to help them achieve their security and business goals.
The IDC White Paper is based on these real-world success stories and highlights the tangible benefits organizations can achieve by partnering with CyberArk. From financial savings to enhanced security and improved productivity, we believe the white paper underscores the comprehensive value that CyberArk brings to the table. The platform’s improved security, business resilience and efficiency for IT, developers and security teams are the primary source of ROI for organizations.
Tap into insights from IDC’s research on the business value of identity security by taking this IDC assessment.
Brandon Traffanstedt is a senior director in CyberArk’s Field Technology Office.
*IDC #US52652224, November 2024.























