
“My goal is no longer to get more done, but rather to have less to do,” writes author Francine Jay. It’s a sentiment that resonates with many of us juggling work, life, and everything in between. There’s no shortage of self-help books and time management tools out there promising to help you master the art of productivity. Unfortunately, attackers have also embraced this notion and their search for ways to work smarter, not harder, has led them straight to the cloud because:
- (Nearly) everyone is there. A vast majority of enterprises are currently engaged with one or more cloud service providers, and many are running mission-critical applications or storing sensitive data there.
- There are so many ways to access valuable data. Cloud computing requires the creation and use of numerous Identity and Access Management (IAM) permissions and entitlements to access cloud infrastructure and services. Each of these identities can become privileged under certain conditions, opening a path to an organization’s most valuable data and assets.
- There are fewer steps to take. Attacks against on-premises infrastructure and applications typically take multiple steps: compromise an initial system, escalate privileges and move laterally to compromise another, then another, then another, until the attacker “owns” a domain. But in the cloud, attackers can fast-track their efforts. By compromising one user’s privileged credentials or API keys, they’re well on their way to achieving their goal in fewer steps, taking less time and with significantly less effort.
- There’s a gap between cloud adoption and security. IT security teams have been forced to learn and protect brand-new environments quickly and in parallel. Their familiar ways of working and traditional network perimeter security approaches simply don’t work in modern cloud environments. Lacking technical cloud security knowledge and cloud-centric tools – while often being tasked with securing multiple cloud environments at once – they’re struggling to defend their organizations. And attackers know they have an advantage.
This is the first in a three-part series on real-world cloud attacks, illustrating how cyber criminals and malicious insiders are scaling their efforts and getting more done by exploiting vulnerabilities in the cloud. Use these deconstructions to start thinking like an attacker and mapping out your own proactive security strategies.
Are You a Cloud Misconfiguration Away from a Data Breach?
The dynamic nature of the cloud often leads to the misconfiguration of permissions and entitlements associated with identities or users. In fact, the Ponemon Institute 2020 Cost of a Data Breach Report identifies cloud identity misconfigurations as “attackers’ entry point of choice.” Combined with stolen or compromised credentials, cloud identity misconfigurations represent nearly 40% of malicious incidents today.
When you consider that each of the major cloud platforms has more than 5,000 possible permissions and actions that can be assigned, it’s easy to see how misconfigurations happen – and add up fast. Given the scale of deployments, speed of change, and limited visibility from cloud-native tools, a common challenge is the accumulation of unnecessary or unused permissions, which is often not visible to overburdened security teams.
Here is a brief deconstruction of a real-world cloud attack chain that utilized misconfigured cloud identities to fast-track attacker efforts and breach a victim organization’s environment:
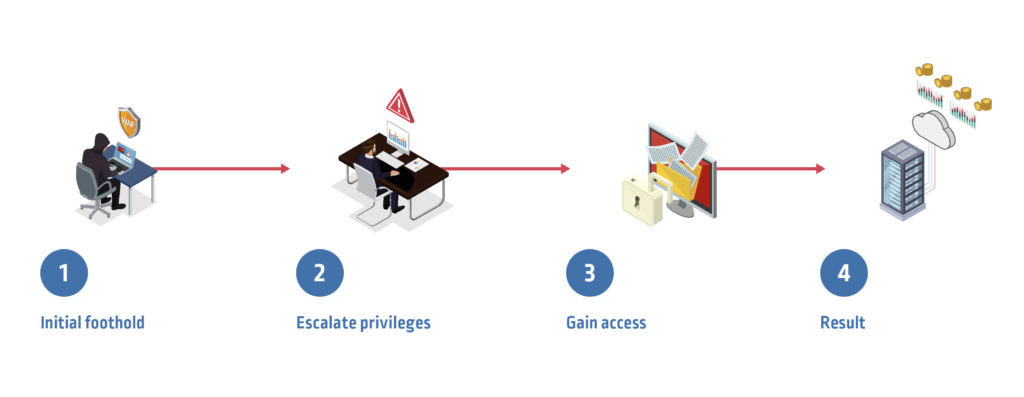
Step 1. Establish an initial foothold: A misconfigured firewall provides the attacker entry into the company’s cloud provider network and allows privileged access to a virtual server. The attacker exploits a common cloud vulnerability in the webserver that runs on the virtual server and compromises access keys.
Step 2. Escalate privileges: The attacker assumes an over-permissioned role and obtains temporary security credentials to the company’s cloud provider storage bucket.
Step 3. Gain access: The attacker accesses sensitive customer information, including individuals’ social security numbers and personal data, in the storage bucket.
The Result: The attacker exfiltrates millions of individuals’ personal data and can now sell it for profit in underground markets. As a result of the breach, the victim organization is forced to pay millions of dollars in regulatory fines. What’s more, the attacker also used the company’s cloud processing power to cryptojack and mine cryptocurrency.
Explore 11 Ways to Reverse the Attacker’s Cloud Advantage
Reversing the attacker advantage and protecting against cloud attacks on identity requires a proactive, identity-centric approach to security. Here are 11 foundational safeguards you can take now to get started. And if you’re looking for help along the way, The CyberArk Blueprint for Identity Security Success (or CyberArk Blueprint for short) is a vendor-agnostic framework for assessing your current strategy and strengthening security across your people, processes, and technology to drive resiliency in the cloud-first world.
Next up, we’ll explore how attackers hijack cloud credentials embedded in code.






















