
In a big, highly anticipated move, last week the White House introduced new cybersecurity guidance to harden federal networks and advance key priorities outlined in President Biden’s May 2021 executive order. While this particular order was aimed at enhancing the security of the software supply chain, the new and any other upcoming guidance seeks to affect the ability of the federal agencies to protect its sensitive data accessed across various resources and environments by its employees, partners and contractors.
The new guidance comes at a time when 10 out of the 24 federal agencies are scoring “F” on their overall cybersecurity practices, according to the FITARA Scorecard. These dismal scores are a reflection of the complexity faced by the federal agencies of over 4.2 million full time employees as well as countless contractors and valid contracts that allow external business to access sensitive information
How the FITARA Scorecard grades U.S. federal agency performance
The FITARA Scorecard grades U.S. federal agencies based on their performance of FITARA-related reform and improvement activities and serves as a tool for Congress, chief information officers, agency heads, and outside stakeholders to better understand how agencies across the government are managing and securing their information technology (IT). The Scorecard is also a way for Congress to hold federal agencies accountable for implementing basic and fundamental IT practices that improve the operation of the federal government.
This score tracks the agencies’ ability to continuously monitor their networks using tools to mitigate and remediate cyber threats. Grades are an average of two assessments: Scores from their Inspectors General (IG) assessments – which looks at agencies’ ability to identify, protect, detect, respond, and recover – and progress on cross-agency priority (CAP) cybersecurity goals.
Currently 10 of the 24 Federal Agencies are scored an F on cybersecurity practices.
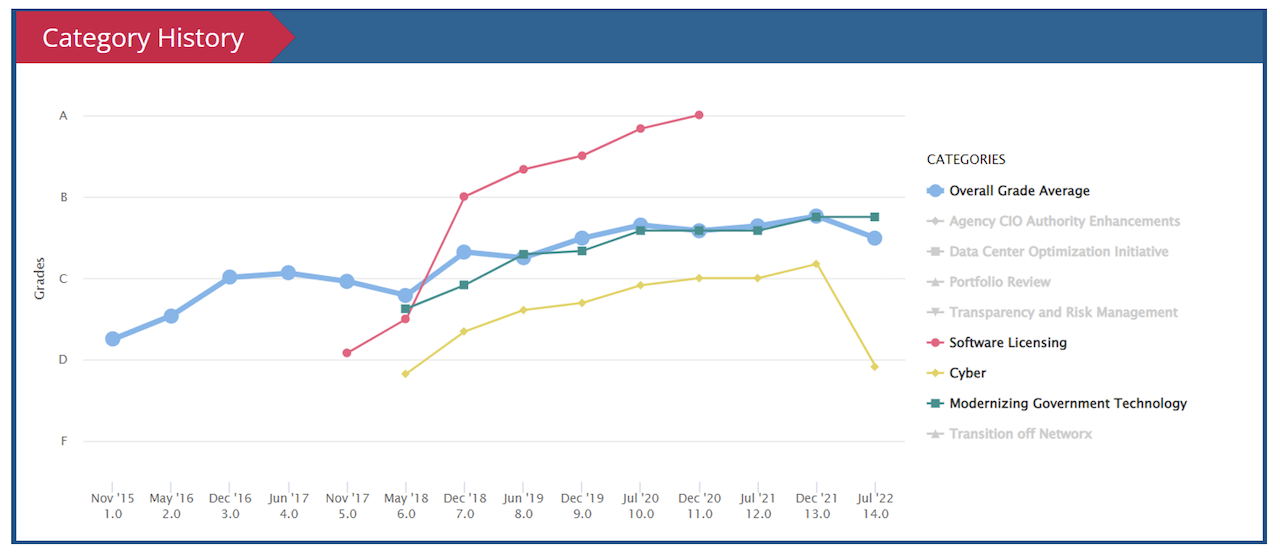
Here’s why.
4,284,777 is not a random number.
In 2022, the federal government reported a total of 4,284,777 full time employees working across its three branches (executive, judiciary and legislative). Over 64% of these employees belong to the executive branch of civilians vs. 34% belong to uniformed military. These employees have varying responsibilities across the federal government. Many of them are granted different levels of security clearance that permit access to the most sensitive classified information. It is no easy feat to continuously manage the digital identities of over 4.2 million employees throughout their government service while protecting critical governmental assets related to national security and other public, sensitive priorities.
The threat is real.
Cybersecurity & Infrastructure Security Agency (CISA)’s Risk and Vulnerability Assessment (RVA) is available to both private and public organizations and specifically focuses on identifying network, system and application vulnerabilities by using a repeatable methodology to deliver actionable findings and recommendations.
Results from CISA’s RVAs conducted in FY2021 indicate that valid accounts were used to gain initial access in 51.5% percent of the FY21 RVAs. The same study indicates that privilege escalation for valid accounts occurred in 47.4% RVAs. Adversaries may obtain and abuse credentials of existing accounts as a means of gaining Initial Access, Persistence, Privilege Escalation, or Defense Evasion. Compromised credentials may be used to bypass access controls placed on various resources on systems within the network and may even be used for persistent access to remote systems and externally available services, such as VPNs, Outlook Web Access, and remote desktop.
The vulnerabilities are multi-fold.
No digital organization can function on its own. Certainly not federal agencies, which operate in conjunction with over hundreds of thousands of small, medium and large-sized vendors to whom over 358,204+ contracts were awarded to in 2021. In many cases, large-sized vendors are expected to sub-contract with small and mid-sized businesses when working for the federal agencies.
For example, in the summer of 2019, the Department of Defense (DoD) assessed the security controls implemented by 10 contractors to whom federal contacts of at least $1 million were awarded. The audits reveal that security controls were not consistently implemented in accordance with Federal and DoD requirements for safeguarding Defense CUI. The common shortcomings were:
- User access was not granted on the user’s assigned duties and did not apply the principle of least privilege when granting access;
- Use of weak passwords;
- Lack of multi-factor authentication;
- Failure to mitigate vulnerabilities identified on networks and systems;
- Placement of CUI on unprotected removable media; and
- Lack of limiting unsuccessful logon attempts to reduce the risk of malicious activities
These sub-optimal cybersecurity practices are further compounded when many of these large vendors have the ability to sub-contract Federal agency contract work to small and medium businesses that may not have adequate resources to maintain necessary security hygiene.
193 million machine identities are a problem.
The CyberArk 2022 Identity Security Threat Landscape Report indicates that for every human identity, there are 45 machine identities. Which means, for the 4,284,777 employee identities, it is possible that the federal agencies are managing over 193 million machine identities. Machine identities need to be protected to secure machine-to-machine communications and authentication, keep communications safe and private, and establish trust between connecting systems. Cyber criminals, malicious insiders and nation-state hackers unfortunately know that most agencies have limited visibility, policy enforcement and remediation of machine identities. This makes certificates and keys easy, high-value targets.
Identity Security with intelligent privileged controls is essential.
Securing identities by implementing a Zero Trust strategy as required by Executive Order 14028 is paramount in the face of such complexity and the increasing number of sophisticated cybersecurity attacks. By enforcing least privilege and enabling just-in-time and standing access for ALL identities – human and machine – federal agencies can easily automate and orchestrate Identity Security processes for holistic protections without security being in impediment to productivity.
Identity Security brings privileged controls by integrating identity management, access management and more importantly privileged access management. This not just enables Zero Trust but to also delivers measurable cyber risk reduction with an integrated approach to securing access for all identities to protect an organization’s applications, infrastructure, and data across a variety of environments.
Federal agencies must seriously consider an Identity Security strategy, especially because of the scale at which they operate and the sensitivity of data they gather for national security.
Improve your FITARA score with the CyberArk Identity Security Platform.
CyberArk’s mission is to provide a modern holistic, risk-based approach to Identity Security which is centered on intelligent privilege controls to secure access for any identity to any resource or environment from anywhere, using any device.
Built for the dynamic and evolving needs of federal agencies, the CyberArk Identity Security Platform enables secure access for any identity to various resources or environments from anywhere using a variety of devices. CyberArk’s deep security expertise and leadership in privileged access management for over 20 years allows us to expand intelligent privilege controls to a broader range of human and machine identities.
The CyberArk Identity Security Platform enables operational efficiencies with a single admin portal, streamlines meeting compliance requirements with unified audit capabilities, and delivers Identity Security Intelligence for continuous identity threat detection and protection.




















