
Maybe your security team is facing an upcoming audit. Maybe you’ve failed one and need to address the audit findings. Or maybe you’re working to improve cyber readiness in the face of ransomware and other advanced attacks. No matter your reason for rolling out Identity Security solutions to secure human and machine identities across your organization, you need to move fast to address your most urgent Privileged Access Management (PAM) requirements in the shortest amount of time possible.
To get up and running quickly, selecting a SaaS-delivered Privileged Access Management solution is a no-brainer for protecting the attack path to your organization’s most valuable assets. But, as with any technology deployment, you still need a solid plan in place to streamline implementation and realize rapid time to value. Based on learnings from global customer deployments, our CyberArk Security Services team has identified repeatable, scalable practices to help organizations fast-track their Privileged Access Management deployments, reduce risk quickly and lay the foundation for a comprehensive Zero Trust security approach.
But before we dig in, here’s a refresher on why preventing the compromise of privileged credentials is so crucial to strengthening overall cybersecurity posture.
The Leading Role of Privileged Access in Identity-Based Attacks
With the adoption of modern infrastructure, cloud services and hybrid work models, privileged accounts and credentials are everywhere — from critical applications and IoT devices to robotic process automation (RPA) and DevOps tools. And while every organization’s IT environment is different, adversaries understand they can attack virtually any business by:
- Acquiring a valid set of credentials for an identity (human or machine) and using them to gain unauthorized access to sensitive data and systems.
- Moving laterally through the network/IT estate to uncover new levels of privileged access and find high-value assets
- Using elevated privileges to steal confidential information or disrupt services
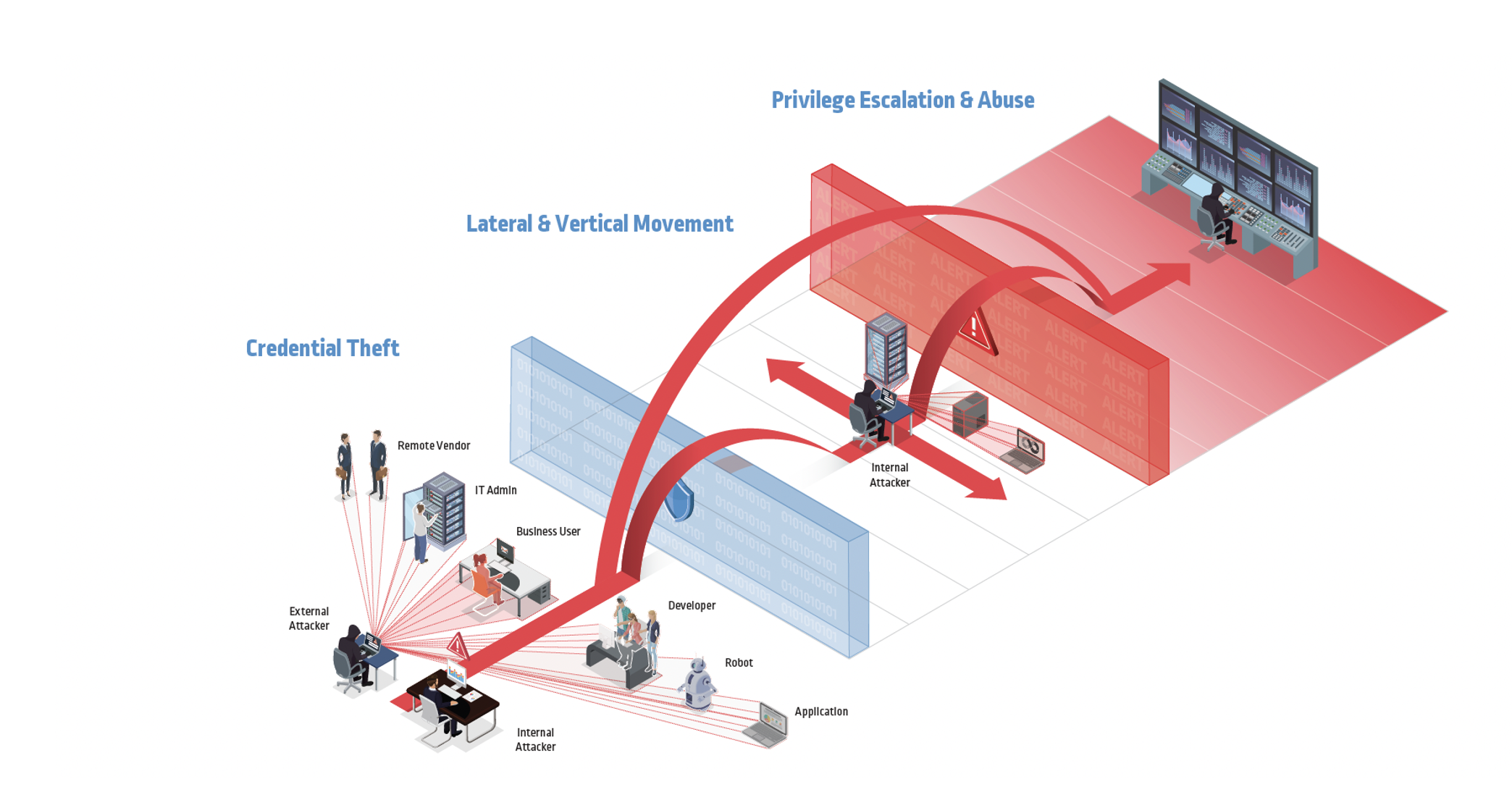
With elevated privileged access and permissions to sensitive data and resources, attackers can begin to exfiltrate customer information, financial data or intellectual property. Or they can threaten to shut down systems or leak sensitive data unless a ransom is received. Either way, the outcome is the same: expensive and painful remediation that consumes security teams’ cycles and resources — which were already stretched to the limit.
Proactively Protect Your Digital Business — Fast
Based on recommendations from NIST and other leading authorities, along with learnings from work with organizations around the globe, here’s a framework for accelerated, high-impact Privileged Access Management deployments. Following these best practices can help you break the cyber attack chain and achieve rapid risk and audit mitigation.
Phase 1: Discovery and Planning
- Know where you are. Use automation to quickly inventory sensitive or compliance-tagged assets within your environment and the privileged accounts used to support them. Define your critical assets — those that, if brought down or breached, could seriously impact your company’s ability to support its mission — and evaluate the strength of existing controls.
- Define where you want to go. With a solid baseline of your environment, outline your goals (both long- and short-term) and key use cases. Hold architecture workshops to review enterprise integrations (i.e., directory, authentication and monitoring tools). These sessions should identify operational considerations like staffing dependencies, technical status of related projects and timelines for executing key use cases. In these sessions, map out the personnel and access control processes necessary for a smooth implementation — and clearly define metrics and success criteria.
- Remove barriers by getting stakeholders on board. Implementing a Privileged Access Management program is as much about people as it is about the technology. Speed your deployment —and help ensure your program’s long-term success — by securing buy-in and support from executive leadership and establishing a change management strategy for staffing and end user adoption from the start.
Phase 2: Deployment
- Test first to save time later. As the saying goes, measure twice, cut once. For example, when organizations deploy the CyberArk Privileged Access Management SaaS solution, a lightweight server or virtual machine is deployed alongside the customer’s environment. This allows teams to walk through common workflows and use cases before integrating them into production.
- Create repeatable workflows. When incorporating learnings from the discovery and testing phases, begin onboarding critical assets while documenting processes so they can be easily repeated as the program expands to new areas.
- Focus on high-risk targets. Many organizations will conduct an intensive “sprint” to quickly mitigate their greatest areas of risk. This often starts by securing identities and associated privileged accounts that can be exploited to control an entire environment, such as domain admin and cloud admin accounts. From there, it’s wise to lock down accounts used to service your most widely used technology platforms. This is often followed by implementing OS-level least-privileged access controls across workstations, laptops, desktops and virtual desktop instances (VDIs) to help block endpoint attacks such as ransomware from progressing.
Phase 3: Expansion
- Demonstrate successes to mature your program. Report time-to-value wins from the initial “sprint” to business leaders, relaying efforts in meaningful, relatable terms like reduced risk of downtime, revenue loss or regulatory penalties. Describe additional steps and investments required to further bolster security and unlock operational efficiencies.
- Codify fundamental practices. As you extend Identity Security controls to strengthen your defenses, formalize and scale these recurring Privileged Access Management practices: account onboarding, testing onboarded accounts, eliminating excess privileges and permissions, and collecting end-user feedback to continuously improve processes.
- Tackle advanced Identity Security use cases. Set finite goals for what comes next. This may include protecting and monitoring sessions for all identities accessing sensitive servers, applications or cloud consoles. Other key use cases include removing local admin rights on servers and workstations, eliminating excessive cloud permissions or securing application credentials and continuous integration/development (CI/CD) pipelines. Continuously assess the effectiveness of your plan, adjusting as needed.
Whether stemming from audit findings, compliance needs or response to heightened risk of attack, protecting identities and their associated privileged credentials is a top priority for many organizations today. Fortunately, significant risk reduction does not have to take long. By following proven recommendations from the CyberArk Identity Security Blueprint across people, process and technology domains, your organization can fast-track your Privileged Access Management deployment to strengthen your defenses and build a long-term roadmap for achieving the highest levels of protection.

















