
82 gallons: that’s how much water the average American uses each day. While we should all attempt to minimize our consumption, it’s easy to take the availability of clean, safe water for granted — from brewing that first pot of coffee in the morning to ending the day with a shower. Yet just like the other critical systems that make modern life possible, the IT infrastructure that water treatment plants and related systems rely on is not only aging, but is also under pressure to become more connected, reliant on automation and maintained through remote connections. For these reasons, as the past several years have demonstrated, this infrastructure is also an attractive target in cyber attacks.
Last week, the Biden administration unveiled a 100-day cybersecurity plan for U.S. water utility operators and extended its Industrial Control Systems (ICS) Cybersecurity Initiative to the sector in response to a spate of recent attacks. The plan focuses on establishing a task force of water sector leaders, bolstering security incident monitoring capabilities, improving information sharing and data analysis, and providing technical support for water systems.
Global Water Systems Under Attack
In February 2021, attackers breached a Florida water treatment plant, gained control of its SCADA system and successfully raised the sodium hydroxide in the water by 100-fold to a poisonous level. Later in the year, U.S. federal agencies issued a joint advisory warning of ongoing threats to water and wastewater systems, citing several phishing and ransomware attacks on facilities in California, Maine and Nevada, among others.
Vulnerable water systems are a global issue: in 2020, Israel experienced a major attempted attack on its water infrastructure, and the U.K. has warned of “credible threats” to its critical infrastructure, including the water sector. A 2021 SANS Institute study paints a troubling picture: one in 10 wastewater plants has a critical security vulnerability today.
As operational technology (OT) assets are increasingly connected to IT networks, remote access to these critical systems is now the norm. Since the pandemic began, critical infrastructure operators — from water treatment plants to oil pipelines — must focus on protecting privileged access to the applications and systems that are responsible for keeping this infrastructure up and running.
Operational Technology: Connected, But Not Adequately Protected
Traditionally, industrial control systems and process and production equipment were not connected to a network. Modifications to OT environments could only be performed through in-person physical interaction with system controls (pulling levers, flipping switches and turning dials). So, security risks were limited to the people who had direct access to the facility. But as digitalization and IoT adoption accelerated, many OT environments, full of decades-old technology, were brought online. Today, OT and IT networks are becoming increasingly interconnected. This increases the attack surface for industrial organizations by increasing the number of sensitive systems online. All access to these systems must be treated as privileged access, something attackers consistently seek out to execute their plans.
Meanwhile, business requirements and pandemic-driven safety concerns have forced many organizations to adapt jobs that traditionally required physical presence at the facility to a remote model. As a result, internal and third-party personnel responsible for operating, troubleshooting, upgrading and maintaining OT equipment often do so remotely.
The U.S. Department of Homeland Security (DHS) provides examples of identities that may legitimately require remote access to control systems. These include, but are not limited to, internal employees — such as systems operators, maintenance engineers and field technicians — and external parties — such as vendors, business partners, systems integrators, MSPs and regulatory entities. To help ensure safe, continuous operation of water, wastewater and other OT facilities, all such identities need secure remote access to systems. However, provisioning standing (or ‘always on’) privileged access to critical devices and systems in OT environments can heighten the risk of credential theft.
The SANS 2021 Survey: OT/ICS Cybersecurity identified external remote services as the most frequent attack vector involved in OT/control systems incidents. Similarly, the U.S. Cyber and Infrastructure Security Agency (CISA) cites access as one of the most prevalent IT and OT weaknesses and risks.
Insecure Remote Access Puts OT Systems at Risk
Considering how disruptive a cyber intrusion can be in OT environments like water facilities, the importance of treating all vendors and employees with remote access as privileged identities — and protecting their access accordingly — cannot be overestimated. Unfortunately, risky security practices are far too common, such as:
- Sharing administrator credentials for SCADA and other critical systems
- Provisioning third parties with standing access rights in corporate directories
- Failing to securely store, manage and distribute credentials — including those for air-gapped systems
- Using the same passwords for multiple accounts
- Giving operators and maintenance personnel administrator-level access to critical systems they do not regularly access
- Providing unrestricted, anytime access to sensitive resources
- Improperly air-gapping systems, exposing systems to the internet unnecessarily or using an unsecured local area network
- Running outdated, unpatched operating systems and software
The 2021 Florida water plant attack highlighted several of these issues, specifically around weaknesses in remote access. According to reports, all computers used by plant personnel to access the SCADA system for water treatment had remote access and a shared password, despite the sensitivity of the required operations.
Many OT environments and water facilities disconnect — or “air-gap” — systems from the internet for security purposes. Even in air-gapped OT environments, securing remote access remains vital. Plant equipment, HMI, DCS, PLC and other OT systems still require maintenance and upgrades performed by internal staff and, oftentimes, external contractors. In these situations, privileged credentials used to access critical systems must be provisioned securely and carefully monitored. Yet too many organizations share passwords in antiquated systems like Excel files with shared systems.
Protect Privileged Access to Address Most Prevalent OT Weaknesses
Fortunately, Identity Security solutions, centered on privileged access management, can provide offline privileged access, eliminating the issue of credential sprawl, no matter the environment. Internal admins and third-party contractors can retrieve privileged credentials and maintain session audit via mobile apps, helping organizations defend against attacks targeting credential theft while satisfying audit and compliance.
By enabling secure third-party access as part of a Zero Trust approach to security, industrial control organizations can help address the most prevalent identity-related weaknesses and risks identified by CISA:
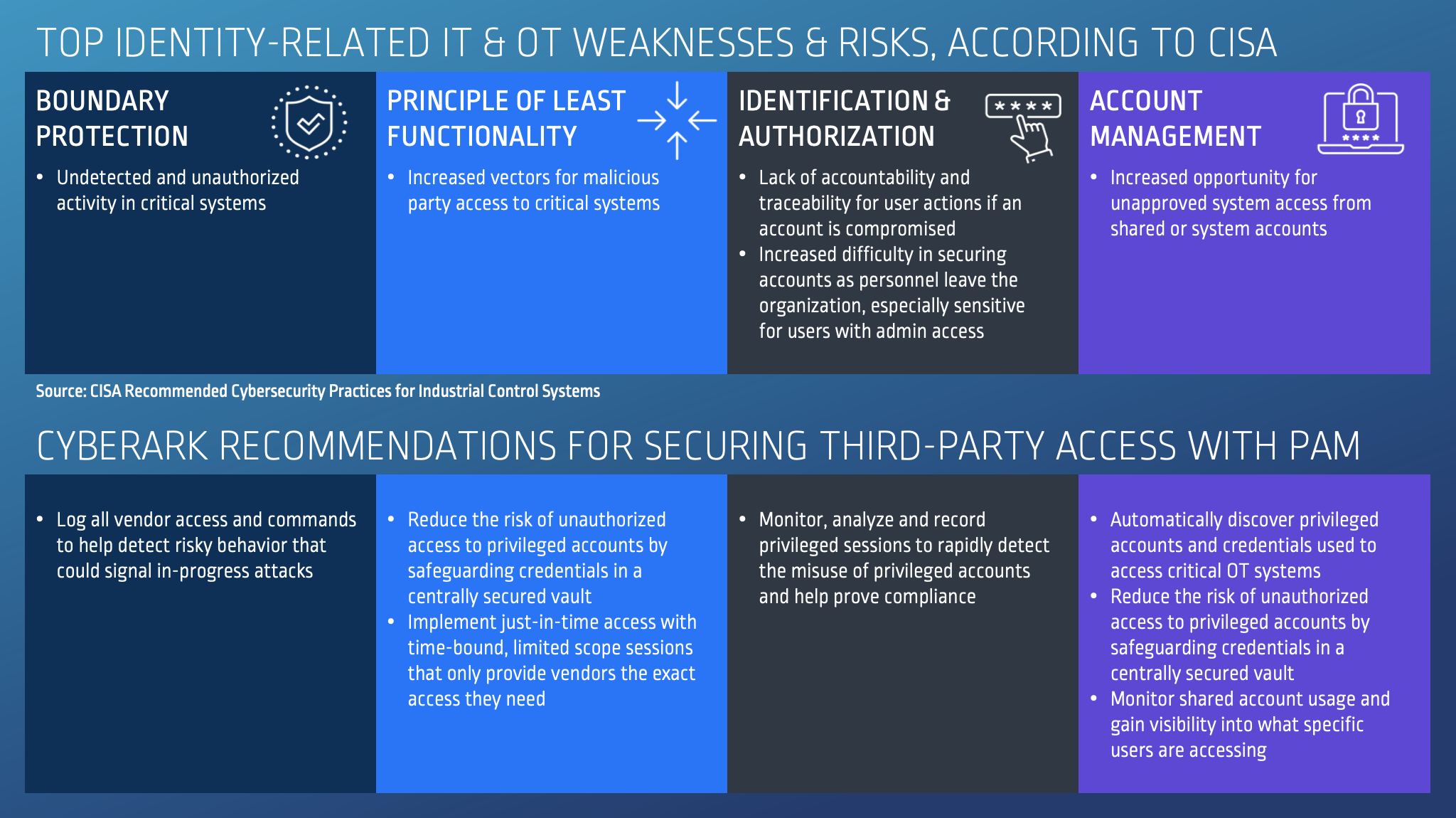
Of course, strengthening controls on remote access is one of many critical steps toward greater cyber resilience. Today’s utility organizations are often under-resourced. OT systems are aging and straining from decades of use. Skilled cybersecurity practitioners are increasingly hard to find. And industry regulations remain inconsistent (at best). It’s encouraging to see our water systems and other critical infrastructure getting the increased cybersecurity attention they so desperately need — but we still have a long way to go.
Learn more about secure remote access and Privileged Access Management for OT and IT environments in the CyberArk resources library, and take the first step to secure remote vendor access in an interactive tour of CyberArk Vendor Privileged Access Manager.

















