
Most companies now recognize the serious and insidious nature of cybersecurity threats. But many fail to grasp that the digital transformation, remote work, automation and cloud migration activities of the last few years have turbocharged the number of identities seeking access to data and critical business systems. This surge in identities has exponentially increased the likelihood of cyberattacks, undercutting the effectiveness of traditional identity and access management (IAM) paradigms.
In the modern enterprise, nearly every employee has multiple identities on the network and uses several devices to access business systems. According to the CyberArk 2022 Identity Security Threat Landscape Report, the average staff member accesses more than 30 applications and accounts, requiring them to remember and manage countless passwords and repeatedly authenticate themselves to systems and applications. These employees often collaborate with third-party partners who also access sensitive company data and assets to do their jobs. At the same time, machine identities outnumber human identities by a factor of 45:1, the CyberArk report found.
According to the latest Verizon Data Breach Investigations Report, 80% of Basic Web Application Attacks (BWAA) start with compromised credentials. Identity has become the latest high-value target in the cybersecurity battleground. Yet the proliferation of identities has made it difficult for security professionals to strike the right balance between safeguards and speed to do what’s necessary to protect the complex web of endpoints, devices, cloud workflows and SaaS solutions. And that’s without making it overly difficult for the enterprise or leaving gaps that bad actors can easily exploit.
Most traditional IAM tools were not built with a security-first approach, nor were they designed to manage the broad number of human, application and machine identities that exist across on-premises data centers, SaaS environments and hybrid, multi-cloud infrastructure. This identity challenge is compounded by using multiple siloed tools that create management headaches due to a lack of automation and poor visibility. Given the stakes, it’s time for organizations to recalibrate and make identity the centerpiece of their security strategies.
A New Vision for Identity Management
So what’s the best way to secure all these types of identities within an organization? It starts with a risk-aligned Identity Security approach that embraces the core concepts of Zero Trust. This includes acknowledging that attacks will occur and enforcing intelligent privilege controls consistently to secure access for all identities – human and machine – and flexibly automate the identity lifecycle. By layering these with continuous threat detection and prevention capabilities, organizations are empowered to spot threats earlier and stop identity-driven attacks in motion. The ultimate goal is to enable users with quick and secure access to necessary resources, while trusting nothing and verifying everything behind the scenes.
The modern version of Identity Security rests on four pillars:
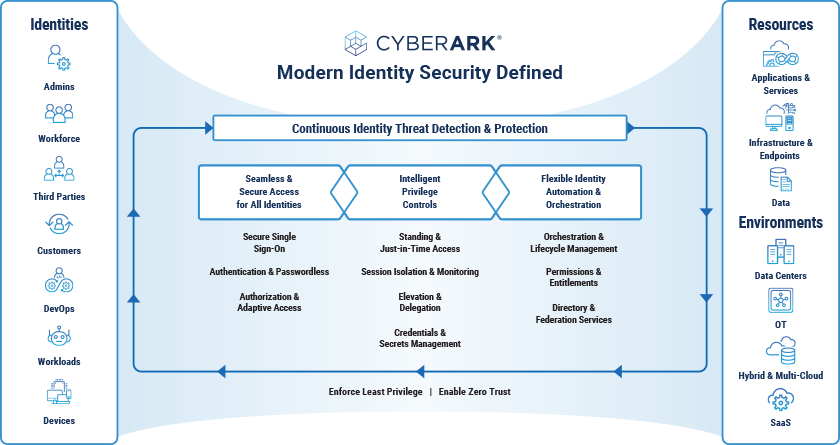
To get a picture of how Identity Security might work in the real world, consider a DevOps specialist who is regularly accessing highly sensitive CI/CD resources and tools with the help of a bot that takes care of some of the more mundane housekeeping work. With an Identity Security approach, both the DevOps specialist and the bot (a machine identity) are covered by intelligent privilege controls, allowing them entry to the necessary cloud workspace, but within the context of minimal required access for the least amount of time necessary. Say that developer eventually leaves the position. A modern Identity Security platform with flexible automation and orchestration will automatically shut off access and permissions at just the right time, while the bot retains access and can be redeployed to a new team member.
Identity Security Best Practices
With the basics in place, there are several Identity Security best practices to consider. Among them:
- Security starts at the front door. Different types of users need access to various resources, so Identity Security must start at the endpoint. Embrace enabling controls like adaptive multifactor authentication (MFA) for endpoints and continuous authentication so if a user decides to elevate access to launch an application, the proper security controls will do their thing. Beyond least privilege and application control, look for solutions that support policy-based, audited just-in-time elevation sessions, credential defense, workforce password management and ransomware protection, among other capabilities.
- Don’t overlook the cloud. The cloud ushers in many Identity Security challenges, including misconfigurations and over-permissioned accounts. Look for platforms that can detect and remove excessive permissions, provide actionable remediation and promote just-in-time privileged access.
- Remember the machine challenge. Centralized secrets management can help remove embedded API keys and secrets from applications and automation tools and help drive authentication across a hybrid, multi-cloud environment.
Centered on intelligent privilege controls, Identity Security is the next evolution of protection, providing a holistic and flexible framework that keeps companies focused on business outcomes and a step ahead of adversaries.
Chris Maroun is a senior director in the CyberArk Field Technology Office.

















