
It’s 2 a.m. when your CISO gets a call from the security operations center (SOC) saying they’ve spotted signs of lateral movement with stolen credentials. The SIEM system flagged it. Your EDR tools confirmed it. You’ve got a security breach.
As attackers advance, the team scrambles across a range of different tools: access management dashboards, privileged access management consoles, cloud logs and more, just to piece the story together.
This is not a drill. It’s our new reality: strong identity and access management (IAM) policies and multi-factor authentication (MFA) alone can’t stop an active attacker who’s already inside using stolen credentials. The real danger lies in the silent, undetected misuse of identities and privileges over time.
What if you could automatically detect and contain that misuse — before it spreads? That late-night call might never have happened. Prevention is vital, but it isn’t enough. Organizations need a layered defense model that prevents first, detects continuously, and responds instantly. That’s the power of identity threat detection and response (ITDR).
What is identity threat detection and response (ITDR)?
ITDR has become a critical defense layer. Organizations now face a proliferation of identities, a diverse workforce, remote work, DevOps practices , and constantly changing infrastructure. As a result, identity systems have become both the entry point to critical resources and a favorite target for attackers. Nearly three-quarters of breaches involve human error, where a person simply makes a mistake or falls prey to a social engineering attack. Foundational identity and preventative controls alone are no longer enough.
Once attackers get inside with valid credentials, they don’t break authentication; they abuse privileges. ITDR addresses this by continuously monitoring identity activity and behavior, privilege escalations, lateral movement, and anomalous sessions, then responding in near real time to contain threats before they can escalate into major incidents.
At its core, ITDR applies advanced analytics to identity activity and context, focusing on behaviors like privilege escalation, lateral movement, and anomalous session activity. Many access management and identity tools monitor risk only during an authentication request. ITDR continuously monitoring every action that happens after access is granted: detecting misuse threats in near real time and responding with automated session termination or credential rotation.
ITDR doesn’t replace access provisioning, it responds to threats where privileges are escalated. For example, CyberArk leverages its intelligent privilege controls such as zero standing privileges (ZSP) and just-in-time (JIT) access to ensure users only receive elevated privileges when needed and automatically revoke them when the task is complete.
This visibility and rapid response capability make ITDR a critical complement to existing access management (AM), privileged access management (PAM), and overall identity security controls.
Identity-driven breaches: Why organizations need ITDR
What began with the infamous SolarWinds supply‑chain attack has since evolved into a steady stream of identity-driven attacks. Just last year, the BlackCat ransomware group infiltrated Change Healthcare by using stolen credentials, then moved laterally, escalated privileges and deployed ransomware that disrupted healthcare services nationwide. Just months before that, MGM Resorts suffered a 10-day outage after attackers socially engineered access and then abused valid credentials to move through critical systems, crippling operations.
Controls managed by identity providers such as single sign-on, MFA, and least privilege policies still remain essential, but they can’t detect or stop attackers once they’re already operating with valid credentials. That’s where ITDR makes the difference.
ITDR complements IdPs by continuously monitoring identity behavior across the privileged workforce, detecting misuse and responding instantly to contain it.
How CyberArk embeds ITDR in identity security
By detecting anomalies close to where identities are active, CyberArk can act before incidents escalate, automatically terminating risky sessions, rotating credentials, isolating accounts, or enforcing step-up authentication and more as needed.
CyberArk also supports bidirectional integration with your broader security tools. Alerts from CyberArk ITDR can flow into your existing SIEM or XDR systems using industry-standard connectors, ensuring analysts get identity context without disrupting existing workflows.
The importance of post-authentication visibility
CyberArk ITDR doesn’t stop at the login. In addition to monitoring authentication signals (e.g. failed logins, anomalous auth patterns, device posture), it continuously inspects what happens after access is granted: privilege elevation, access to high-value resources, and suspicious API calls. By correlating auth events with post-auth activity, the platform detects misuse that would evade purely authentication-focused controls, and triggers targeted containment actions that protect sensitive resources, giving you end-to-end detection and response.
Why ITDR should be built-in, not bolted-on
Rather than offering some level of ITDR capability scattered across identity tools, CyberArk integrates it directly into its Identity Security Platform, providing a unified approach that delivers:
- End-to-end detection and response: Tracks identities from authentication through the entire session, correlating auth signals with PAM events, credential use, and privileged access to detect misuse and automate containment.
- AI-powered detection with CyberArk CORA AI: Behavioral models continuously adapt using the CyberArk CORA AI engine, spotting subtle anomalies and privilege misuse patterns that static rules often miss.
- Built-in response workflows: Out-of-the-box playbooks enable session termination, credential rotation, and account isolation, while flexible APIs let teams customize response actions.
How CyberArk differs from other ITDR approaches
Many ITDR offerings are designed as standalone, vendor-agnostic products that ingest identity signals from multiple IdPs and then feed alerts into a broader security stack. CyberArk’s approach is different: our ITDR is purpose-built and deeply integrated into the CyberArk Identity Security Platform and natively aware of user behavior, PAM sessions, secrets management, access orchestration, and entitlement context.
Because detection and enforcement live in the same platform that issues and governs access, CyberArk can close the loop faster: detect misuse, act immediately (rotate credentials, kill sessions, enforce JIT), and produce auditable evidence, all without stitching together separate tools. That tighter coupling delivers more immediate value to existing customers and simplifies response for teams already invested in CyberArk.
- Direct identity context: CyberArk captures events natively within its unified platform across privileged sessions, credentials, and workforce access so teams can see identity activity at the source.
- Automated containment: Instead of sending alerts alone, CyberArk ITDR can act immediately through the same platform that granted access for example, terminating a risky session, rotating a credential, or requiring step-up authentication.
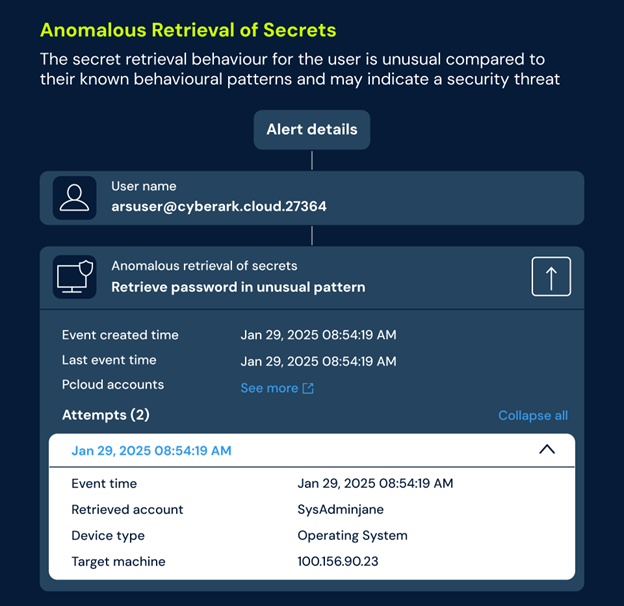
Expanding ITDR to AI agents and machine identities
Today, CyberArk supports several use cases for workforce and high-risk users such as IT, and developer identities, but the trajectory is clear: ITDR must extend to AI-driven and machine identities as they proliferate. The roadmap includes modeling agent behaviors, securing ephemeral machine credentials, and enabling automated remediation for AI agents and service identities so the same identity-aware detection and rapid enforcement that protects humans will also govern autonomous systems. In short: you can detect and act for every identity type now, with more alert signals to be added, and scale that posture as machines and AI increasingly act on behalf of the business.
Staying one step ahead of adversaries with CyberArk Labs
Bad actors are always innovating. CyberArk Labs is our dedicated research arm that tracks emerging attacker techniques, threat campaigns, and novel attack vectors across modern enterprise environments. The team synthesizes data and telemetry from product deployments, open-source intelligence, and partner threat feeds to produce timely, actionable intelligence. That insight flows straight into our ITDR detections, risk models, and automated playbooks so detection rules and remediation steps evolve as adversaries change. In short, CyberArk Labs helps us stay a step ahead of attackers, translating research into practical protections our customers can rely on.
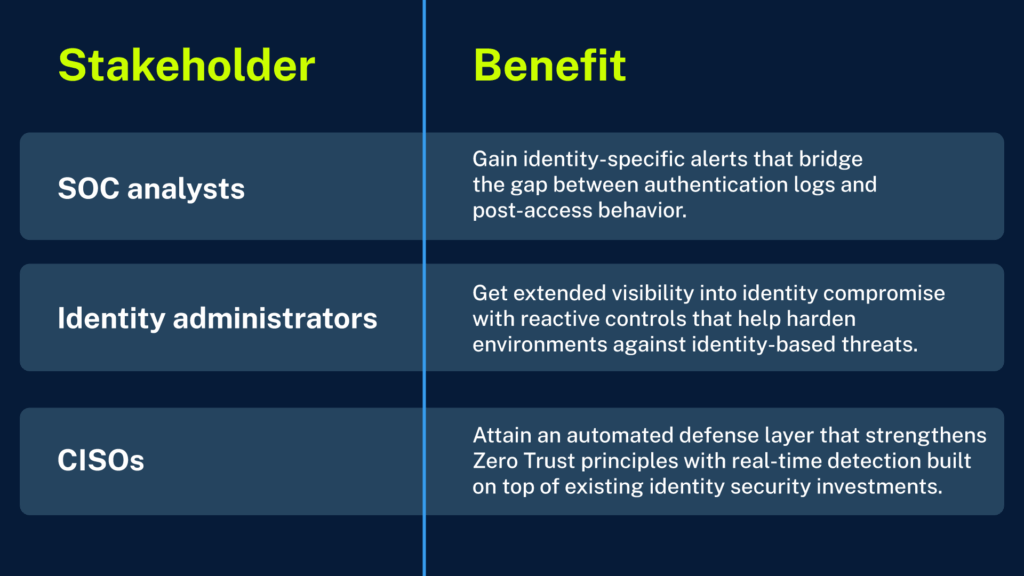
The business value of identity threat detection and response
Identity-driven attacks cut across operations, risk, and governance. Embedding threat detection and response into the platform helps each team see and stop identity misuse in near real time:
ITDR: a core identity defense layer
What keeps CISOs up at night isn’t just malware but it’s the risk of attackers abusing valid credentials and moving unchecked through critical systems.
CyberArk Identity Security Platform is powered by CORA AI, behavioral analytics, and deep identity context so organizations can spot misuse as it happens and shut it down automatically. The difference is simple: instead of scrambling at 2 a.m. across multiple consoles, teams can contain identity-driven attacks from a single, integrated platform.
For security leaders looking to strengthen defenses without adding complexity, CyberArk ITDR provides integrated detection and response without more tools or overhead.
Ready to turn the nightmare into a non-event? Learn more about CyberArk Identity Threat Detection and Response or schedule a personalized demo today.
Yev Koup is a senior product marketing manager at CyberArk





















