
In this blog post, we will introduce a new open-source tool we developed, named Kubesploit, for testing Kubernetes environments. This is a full framework, dedicated to Kubernetes, to assist penetration testers and Red Teamers in performing a comprehensive and in-depth test to mimic real-world attack scenarios that threaten many organizations worldwide.
As more and more organizations use microservice and container architectures, Kubernetes continues to become more popular. According to a Cloud Native Computing Foundation (CNCF) survey, more than 84% of organizations run containers in production, and more than 78% rely on Kubernetes as their container orchestration platform. The widespread popularity of this technology requires attackers to hone their Kubernetes skills.
To help protect Kubernetes clusters from attacks, we need to face the technology and the organizations being targeted. Yet, most of the tools available today are aimed at passive scanning for vulnerabilities in the cluster, and there is a lack of more complex attack vector coverage. These tools might allow you to see the problem but not exploit it. It is important to run the exploit to simulate a real-world attack in order to determine corporate resilience across the network. When running an exploit, it will practice the organization’s cyber event management, which doesn’t happen when scanning for cluster issues. This can help the organization learn how to operate when real attacks happen, see if its other detection systems work as expected and understand what changes should be made. We wanted to create an offensive tool that would meet these requirements.
But we had another reason to create such a tool. The CyberArk Labs team already has two open-source tools (KubiScan and kubeletctl) related to Kubernetes, and we wanted to create additional tools for these environments. Instead of creating a project for each one, we thought it would be better to create a single, centralized tool, which was the genesis for Kubesploit.
Kubesploit is a framework written in Golang and builds on top of the Merlin project (by Russel Van Tuyl), a cross-platform post-exploitation HTTP/2 Command & Control server and agent. Merlin also has a way to add new modules dynamically that allow us to create relevant modules for Kubernetes.
What’s New
We wanted to dynamically load new modules to run in the agent and keep the agent lightweight and flexible, so we added a Go Interpreter named “Yaegi” to Kubesploit. With this capability, it is possible to write new Golang modules on the fly and run them while the agent is still running. Supporting the run of Golang code can allow complex code writing and integrate exploits already written in Go. It also makes it easier for the open-source community to contribute new modules, and the fact that Kubernetes was also written in Golang could allow easier integration of related pieces of code.
We developed new modules related to containerized environment attack vectors such as breakout from a container to the host, kubelet attack, scanning for known vulnerabilities in the cluster, and services and port scanning. We plan to add more modules in the future and support contributions for new modules related to Kubernetes and containerized environments in general.
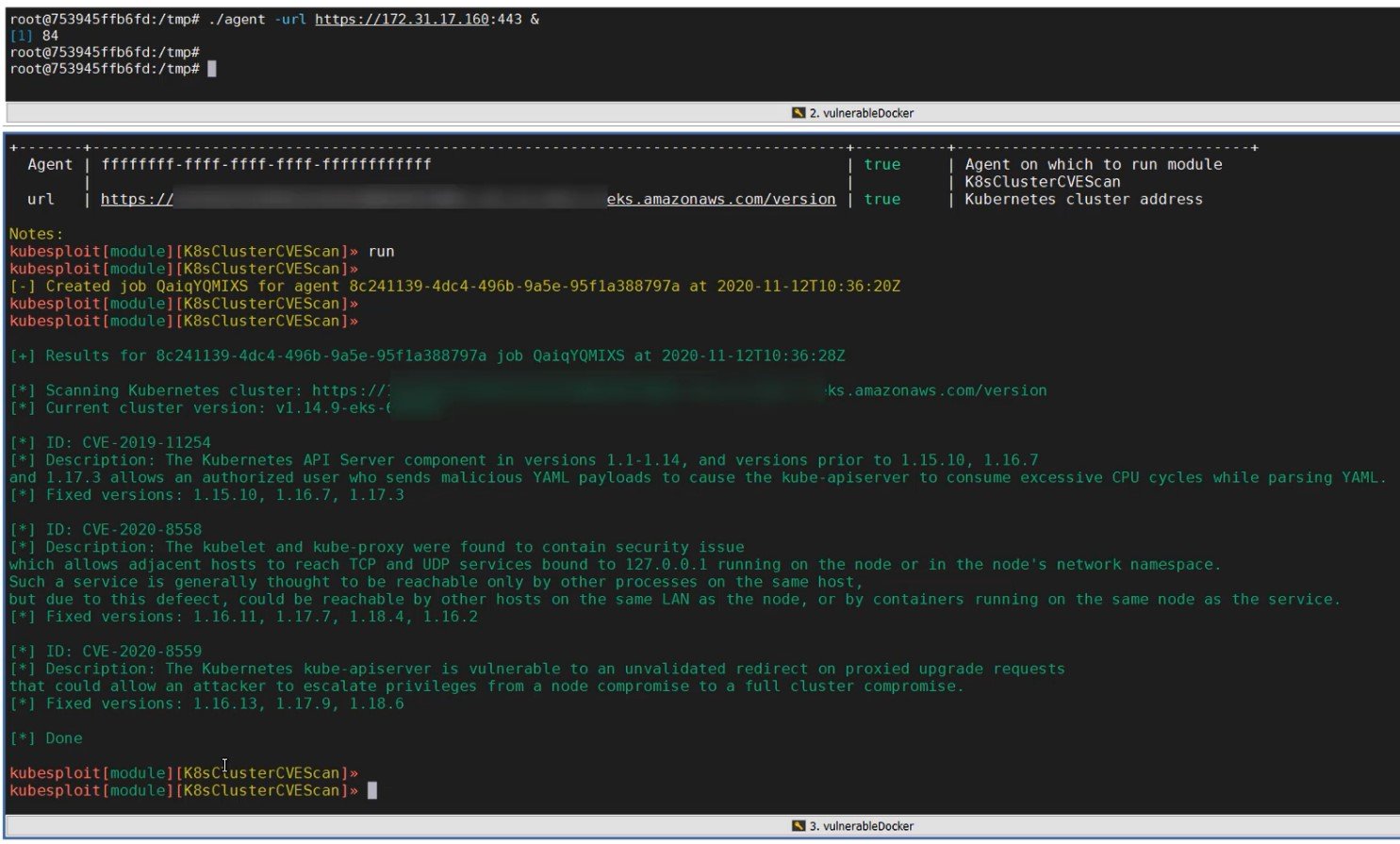
Figure 1. CVE scan module output
Keeping it Safe
Our main goal, our “Why,” is to contribute to raising awareness of the security of containerized environments and improve the mitigations implemented in the various networks. We aim to achieve all this through a framework that provides the appropriate tools for penetration testing teams and Red Teamers during their activities in these environments. Our “How” is by taking a very clear and responsible point of view on using such tools in the security community. This is why it was important for us to keep it safe to the furthest extent possible. This is why we published a tool with three-step protection rings to help ensure legitimate use of Kubesploit. The first one is mitigation techniques and tips attached to each module to protect against the attack vector we are demonstrating.
The second step is YARA rules to catch binaries that are related to Kubesploit. This should help to find any use of Kubesploit binaries in a real attack and not as part of legitimate penetration testing.
Our third step is the integration of IoCs (indicators of compromise) within the code that records the activity. The agent writes its activity to the machine it runs from. Any instructions sent by the server are being recorded by the agent and are saved locally, which should assist in future investigation.
Quick Start
We hope you’re as excited as we are! And, there’s no better way to learn something new than to try and play with it a bit.
We created a dedicated Kubernetes environment in Katacoda where you can experiment with Kubesploit. It’s a full simulation with a complete set of automated instructions on how to use Kubesploit. We encourage you to explore it.
For more information, please visit the Kubesploit GitHub page.
How to Contribute and Give Feedback
Your feedback and questions about Kubesploit and other CyberArk open-source projects are welcome in our community forum, CyberArk Commons. As we mentioned before, it is now even easier to contribute your own exploit modules to Kubesploit with our new dynamic exploit support. If you are interested in contributing, open your pull requests on the Kubesploit GitHub page.























