
When I started my career on the trade floor of a Canadian bank, I quickly learned what it meant to work in a fast-paced, highly regulated environment. Every identity had to be secured, justified and auditable. Later, when I moved to the security engineering team, I saw firsthand how compliance could consume entire teams. We weren’t just protecting accounts; we were constantly running manual processes to prove that the right controls were in place.
That experience taught me something I carry into every customer conversation: compliance is simply proving that you’re doing what you said you’d do. However, when identity security depends on manual, reactive checklists, it’s not simple at all. It becomes a burden on the entire organization.
I’ve also seen the opposite: identity security running like a well-oiled machine, automatically adjusting as people, machines, and AI agents change roles, access, and risk levels.
The turning point came when I realized that business context data is the missing link. It’s what binds identity security to efficiency. Without it, ownership, business justification, and risk become endless cycles of assembling evidence. With it, compliance can become continuous, automated and far less painful.

What engines taught me about identity security automation
Before I entered the tech industry, I worked as an auto mechanic. I tuned carburetors, fuel injection systems, and learned about air-fuel ratios. The goal of every engine is the same—fuel efficiency—the perfect air-to-fuel burn rate that delivers power with zero emissions.
This quest for efficiency has led the world from old-fashioned carburetors (think 1985 Honda Civic) to digitally controlled fuel injectors (think 2025 BMW 3 Series). Carburetors require constant manual tuning, whereas fuel injection systems use sensors and software to adjust automatically for peak performance.
I see many parallels in identity security. Here, efficiency is about maintaining the perfect balance of access and control—and keeping orphaned accounts as close to zero as possible.
Manual compliance processes are a lot like carburetors: Reactive, inefficient, and dependent on a human to make adjustments, verify controls, and chase down orphaned accounts—wasting time and leaving blind spots.
Automated enforcement is like modern fuel injection: it is orchestrated and plugged into sensor data, allowing it to use real-time information to fine-tune performance automatically.
How business context data keeps the identity engine in tune
But what actually powers this shift from manual to automated compliance? The answer lies in business context data.
In identity security, business context data acts like a sensor system in a modern engine—constantly sending feedback to keep the organization’s engine running at peak performance. It provides an extra layer of intelligence that explains why an identity exists, who owns it, and how risky its access is—turning static identity systems into responsive, data-driven ones.
Auditors, for example, typically want answers to a familiar checklist:
- Who owns this account?
- What business purpose does it serve?
- What systems or data can it access?
- How sensitive is that access?
Fair questions. But most organizations can’t answer them easily because identity data ends up scattered across HR systems, application inventories, ticketing systems, and security logs that rarely connect. Each audit becomes a scramble to validate business justification, ownership, permissions and risk. This manual process burns out staff and keeps organizations stuck in reactive compliance.
Business context data closes that loop. It connects every system and monitors these key data points across all identity types—human, machine, and AI agents—to automatically maintain a balance of access, ownership, and risk:
- Business justification: Why the identity or access exists (role, app, or service)
- Business ownership: Who’s accountable and who maintains it
- Technical ownership: Who maintains and administers it
- Risk rating and risk flags: How sensitive or controlled the access must be
When identity systems have this context, the right privilege controls are applied automatically—much like a self-tuning engine adjusting for efficiency. They can:
- Automate lifecycle decisions (revoke or adjust access when roles change)
- Prioritize risk (apply stricter controls to high-value systems)
- Prove compliance automatically (because they always know who, why, and how every account is used
When all of this comes together, identity security runs like a finely tuned engine that adapts effortlessly as people, machines, and AI agents change roles, access, and risk levels.
Transforming identity data into continuous compliance
By integrating business context into identity workflows, organizations can transform compliance from a periodic scramble into an ongoing, seamless process.
I’ve seen customers transform their programs by linking identity data to authoritative sources, such as HR systems, ITSM, CMDBs, and application inventories. Suddenly, audits that once took months of preparation can be completed in days. Orphan accounts become easier to manage and slowly disappear. Permission creep fades. Teams can focus on risk reduction rather than chasing spreadsheets.
The lesson is simple: when you enrich identity security with business context data, you unlock efficiency, resilience and trust. Instead of dreading the next audit, your organization can be better prepared, more continuously compliant, proactively secure, and aligned to business goals. But understanding why business context data matters is only half the story—the real shift happens when that data is synchronized and used automatically across identity workflows.
The process takes tuning, iteration and data-driven adjustments. Let’s consider what it takes to get there.
In most organizations, business context data already exists—but it lives in disconnected systems like HR directories, CMDBs, ticketing tools, and application inventories. Historically, security teams had to manually retrieve and merge this data during audits and access reviews, keeping a human permanently “in the loop.”
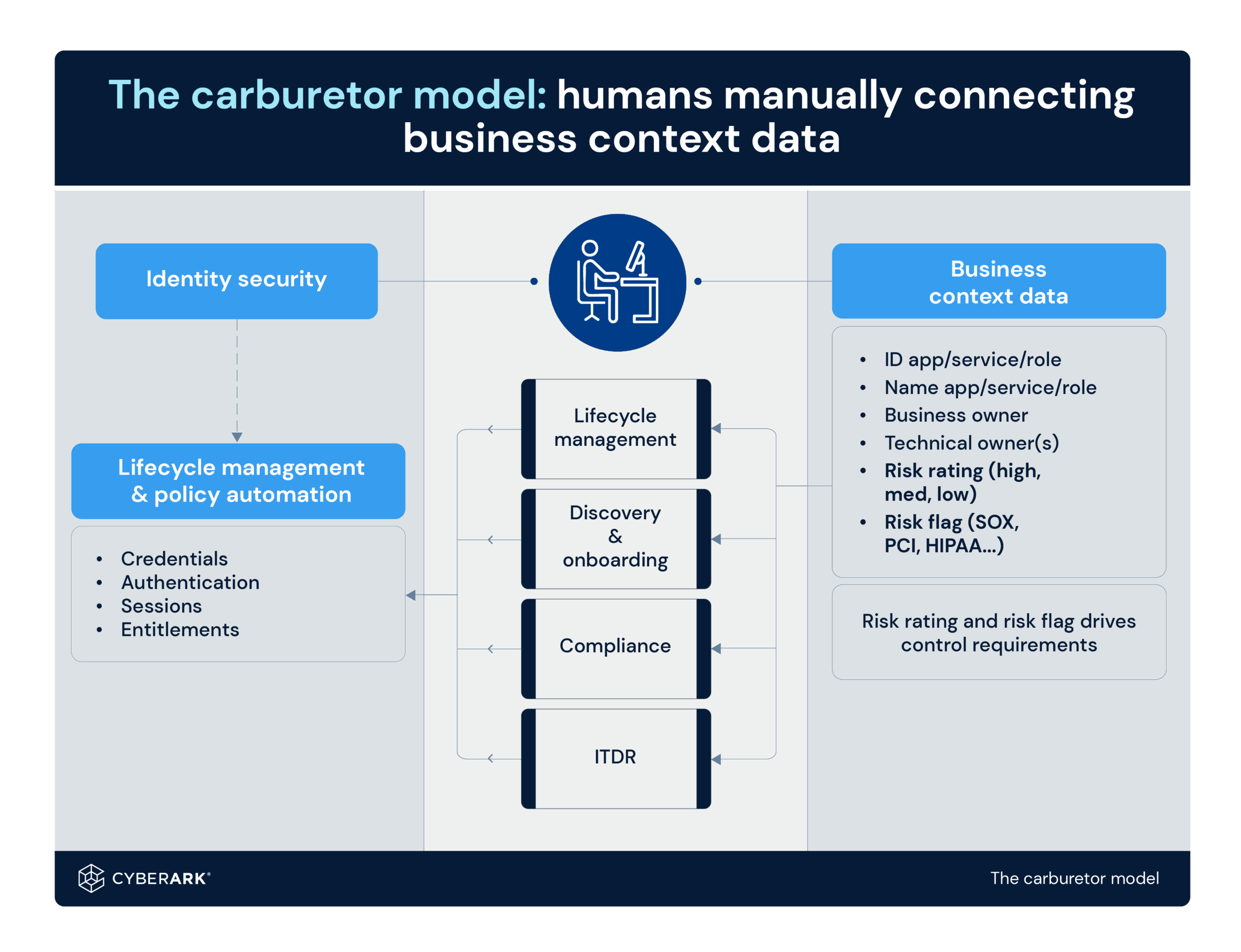
Today, platforms like CyberArk can automatically sync, enrich, and orchestrate this business context data across identity workflows. In other words, the engine has its sensors wired in and can apply the right controls, at the right time, without waiting on manual intervention.
Extending identity security across every identity type
This shift requires a holistic approach—one that addresses the distinct challenges of every identity type across your organization. Each identity type introduces specific access challenges and control requirements. To keep the entire system running efficiently, every identity must be continuously monitored, justified, and adjusted.
Identity security must address a range of identity types, each with unique requirements. Here’s how business context data applies to each:
1. Human identities:
Example: Employee with access to payroll or HR systems
Key data elements: Business justification, business ownership
2. Machine identities:
Example: Service account used for automated cloud backups
Key data elements: Technical ownership, risk rating
3. AI agents:
Example: AI assistant accessing financial data for report generation
Key data elements: Business justification, risk flags
When every identity type operates within the correct context, access remains appropriate, privileges are kept in check, and compliance remains in sync.
Just like an engine needs clean fuel and live sensors, identity security depends on a single source of truth for all identities: human, machine, and AI.
Building continuous compliance from a single source of truth
With the right business context data in place, the path to continuous compliance becomes clear. Discovery is where the tune-up begins. You can’t protect what you don’t know. By syncing HR, ITSM, CMDB, and cloud systems, you maintain constant visibility and control— eliminating blind spots before they become compliance risks.
Once identities are onboarded into your governance or privileged access systems and enriched with context, predictable patterns emerge. High-value assets need stricter controls. Medium- and low-value assets can be governed proportionally. By aligning policies to risk, teams reduce noise and enforce least privilege more effectively.
Next, automating onboarding at the point of creation (for example, during server builds or application deployments) closes gaps before they appear and ensures new credentials are secured immediately.
Over time, automation turns identity management from a reactive process into a continuous one that adjusts as roles change, automatically revoking unnecessary privileges, and logging every change as evidence.
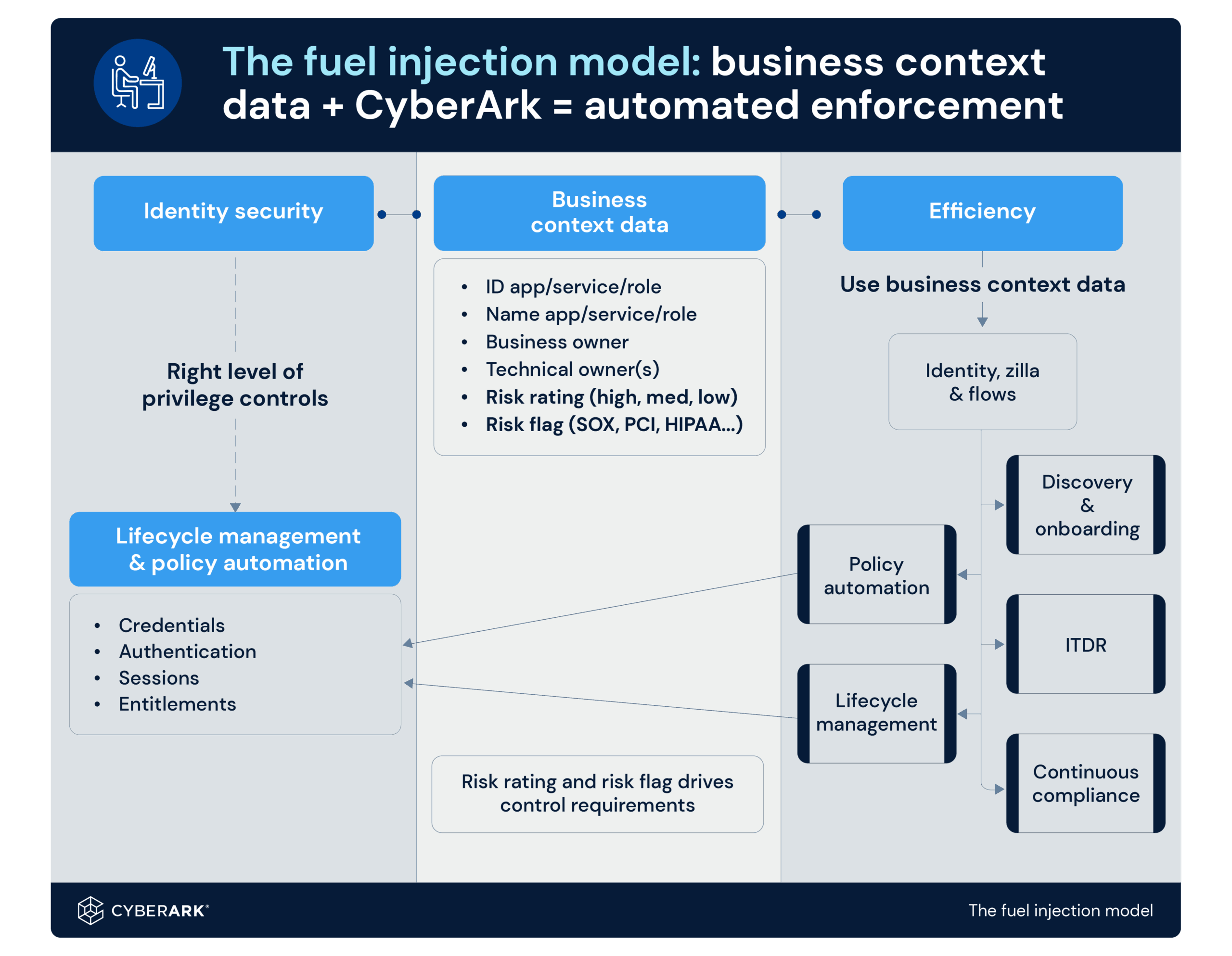
Continuous compliance comes to life when:
- Identity workflows capture business justification at the request stage.
- Self-service and automation replace manual ticketing.
- Metrics track efficiency (orphan account reduction, mean time to rotation, audit hours saved).
- Compliance flows are embedded directly into operations.
When this engine runs well, security teams are no longer burdened by prep work. They’re empowered to focus on reducing risk.
The payoff: A self-proving compliance system
When these practices are put into place, the benefits can be both immediate and measurable. Organizations that tune their identity security with business context data often see measurable results:
- Audit preparation time is reduced from weeks to a ready-now state.
- Orphan and zombie accounts can be eliminated
- Policies applied more consistently across humans, machines, and AI agents.
- Compliance is more closely aligned with SOX, PCI DSS, and HIPAA.
I’ve seen organizations make a transformational shift from reactive checklists to proactive, data-driven, and orchestrated compliance. The common thread is business context data. It’s sensor data that drives efficiency, resilience and trust.
When identity security runs this smoothly, audits can become a non-burdensome process. They help demonstrate that the organization is doing what it set out to do: protecting its people, applications and future.
Lorie Papple is a solutions engineer at CyberArk.























