
Ask a cybersecurity professional what keeps them up at night and you’ll get answers about insufficient staffing, IT complexity or constant attacks on their business. Quantum computing isn’t likely to make the list. Yet as technological change accelerates, real quantum risks are coming into view. Now is the time to prepare corporate IT systems for the “death” of classic cryptography to safeguard data and privacy in the future.
What is Quantum Computing?

Quantum computing isn’t just the stuff of science fiction. Physicists and engineers around the world have dedicated their life’s work to building a completely new type of computer. Once operational, quantum computers promise to unleash a new wave of innovation to solve some of the world’s greatest problems – from eradicating diseases with lifesaving drugs to safeguarding citizens through enhanced weather and traffic modeling.
Small-scale quantum applications, heavy investment activity and heightened government attention all signal progress on the quantum computing front. But building a large-scale general purpose quantum computer – the holy grail – remains an elusive engineering feat. It’s difficult to gauge exactly where things stand since most quantum research remains under wraps. However, many experts agree commercialized quantum computing will be here within the next two decades. Five manufacturers have even put stakes in the ground by promising fault-tolerant quantum-computing hardware by 2030.
Reimagining Public-Key Cryptography for the Post-Quantum World

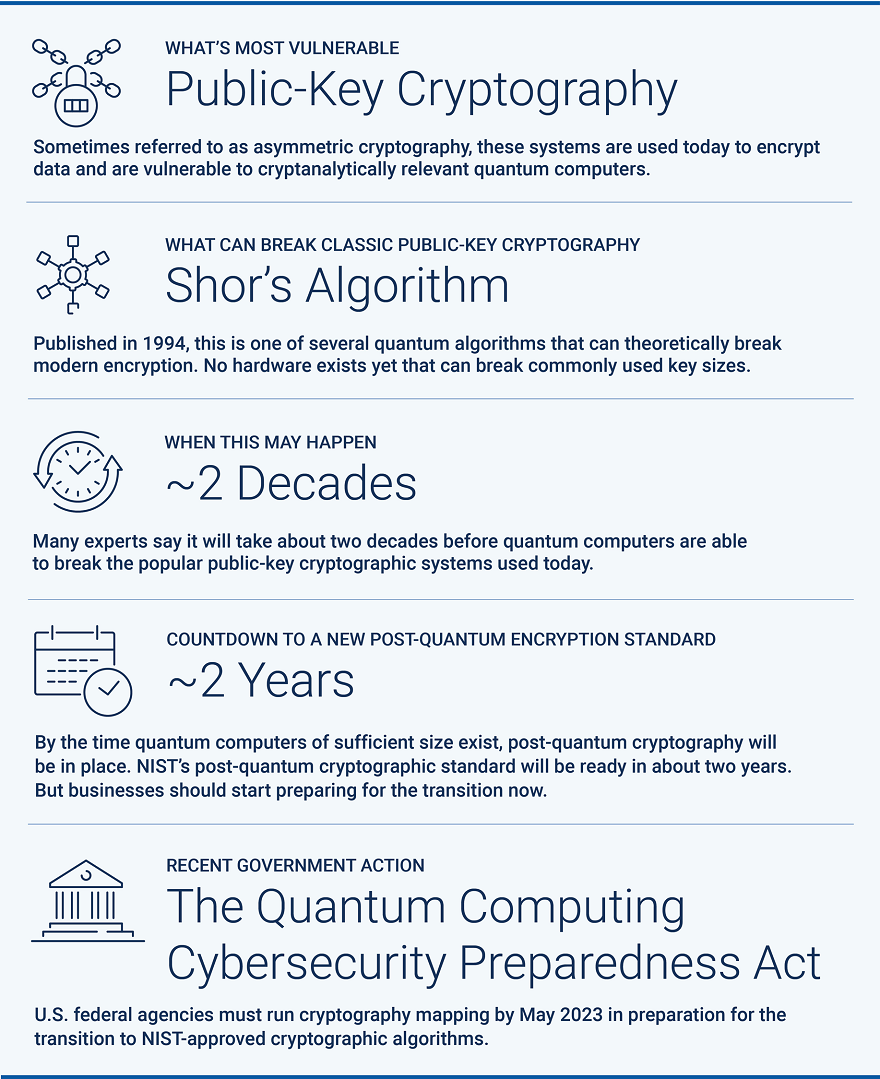
Today, though we don’t give it much thought, we rely heavily on the TLS protocol to secure our digital connections as we access email, bank accounts, mobile apps and virtually everything else on the internet. These protocols use various cryptographic building blocks to securely transmit information. This process, known as cryptography, relies on hardness assumptions that prevent anyone without knowledge of the decryption keys from decrypting our data. But these assumptions will only hold until the first large-scale quantum computer arrives, powerful enough to run algorithms that break these assumptions within hours – something all of today’s computers combined couldn’t do in a billion years. When this happens, all the digital information transmitted over the internet – today and in the future – could become vulnerable.
Algorithms published back in the mid-1990s, including Shor’s Algorithm and Grover’s Algorithm, signaled quantum computers’ potential to break modern encryption. These quantum algorithms are just waiting on hardware that’s built with enough processing power to run them.
Recognizing these risks, the U.S. National Institute of Standards and Technology (NIST) initiated a process in 2016 to “solicit, evaluate and standardize one or more quantum-resistant public-key cryptographic algorithms” and ultimately deliver an accessible, secure post-quantum communications method. In July 2022, NIST unveiled the first four quantum-resistant encryption algorithms. But as with every standardization push, the process takes rigor and time – about two more years until the standard is finalized, according to NIST’s estimate.
Meanwhile, the Biden administration is one of many governments that’s taking quantum computing risks seriously. In December 2022, the president signed the Quantum Computing Cybersecurity Preparedness Act, calling for federal agencies to run cryptography mapping by May 2023 in preparation for the transition to NIST-approved cryptographic algorithms. Just a few months prior in September 2022, the U.S. National Security Agency (NSA) outlined requirements for owners, operators and vendors of national security systems (NSS) to start using post-quantum algorithms by 2035.
Four Steps to Get Quantum Ready
While these efforts mark important progress, we still face a long, winding road to post-quantum cryptography adoption. Just consider that it’s taken almost 20 years to deploy modern public key cryptography infrastructure.
Whether your organization ultimately chooses to use an existing quantum-resistant algorithm or wait for a definitive standard to be published, replacing today’s methods be challenging. While it may seem like quantum computing is lightyears away, the time to start preparing for a transition – along with many other post-quantum business realities – is now. As you keep an eye on emerging government requirements and standardization milestones, here are four steps you can take:
1. Know your crypto. This may sound obvious, but cryptography is so engrained in our systems, applications and devices that many organizations don’t even know which algorithms they’re running. Step one is to find out.
2. Inventory your data. Focus on your most critical assets first – especially sensitive datasets with a long shelf life. Ask yourself: What are the consequences of someone getting their hands on this encrypted data today and decrypting it in ten years? The answer to this question will significantly affect the migration plan in terms of priority and timetables.
3. Map your crypto connections. Create a map of each corporate system using cryptography, and what data exists within each system. This will help you identify the riskiest areas of post-quantum vulnerability. As previously mentioned, switching cryptography algorithms will be a process. Fortunately, most organizations won’t have to make a massive switch all at once. Many datasets will not require quantum-safe security methods right off the bat.
4. Make a plan. Use your learnings from steps 1-3 to start developing a cryptographic transition plan that encompasses other cybersecurity and data privacy standards that may need to be updated, along with steps for hardening existing security systems and processes. It’s important to note that prioritizing one system over another for cryptographic transition highly depends on organizational functions, goals and needs. The European Telecommunications Standards Institute (ETSI) and U.S. Department of Homeland Security offer detailed guidance and prioritization considerations for this.
If your organization has the cryptographic expertise, it can get involved with NIST or other entities working to develop post-quantum cryptography standards and raise awareness. For example, my fellow cryptographers may be interested to know that NIST is currently accepting additional post-quantum cryptography digital signature scheme proposals until June 1, 2023.
Changing our cryptographic infrastructure won’t happen overnight but with enough lead time, collaboration and a pragmatic approach, we can move confidently and securely into the quantum computing era.
Dr. Erez Waisbard is a Technology and Research Lead at CyberArk
Editor’s note: To learn more about quantum computing’s impact on classic cryptography, read Dr. Waisbard’s Medium post, “Quantum Computing is Going to Kill Classic Cryptography. But We Can Still Save It” and tune in to our podcast conversation on this topic on the Trust Issues podcast.























