
The omnipresent ransomware threat is changing how healthcare organizations approach cybersecurity — from formalizing practices in an effort to obtain cyber insurance coverage to improving their ability to restore encrypted data after attacks. But as cyber attackers lean heavily on third-party vendors and suppliers to extort ransoms, remaining gaps across healthcare security frameworks are coming into focus, including a lack of Identity Security controls for securing and managing privileged accounts and third-party access.
Healthcare is Ransomware Attackers’ No. 1 Target
The average healthcare organization faced two or more ransomware attacks over the past year, found the CyberArk 2022 Identity Security Threat Landscape Report — and according to the FBI, healthcare is still the most targeted industry. While ransomware is far from new to the sector, attacks continue to grow in sophistication and scale.
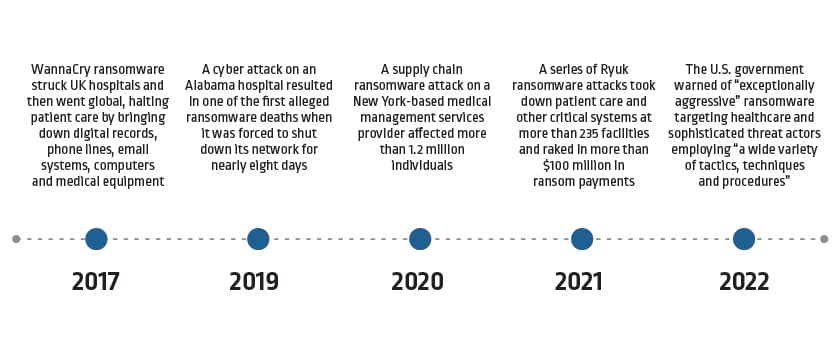
Examples of recent ransomware attacks on healthcare organizations
Taking a Broader View Across the Healthcare Supply Chain
In the healthcare field, it’s common to view ransomware and other cyber threats as they relate to the electronic health record (EHR). Lisa Pino, director of the Office for Civil Rights (OCR) at the U.S. Department of Health & Human Services (HSS), recently urged covered entities and business associates to expand their thinking and approaches, writing in an HSS blog post, “Risk management strategies need to be comprehensive in scope … from software, to connected devices, legacy systems, and elsewhere across your network.”
Part of this expanded approach involves better assessing and managing cybersecurity risks associated with third-party vendors across vast healthcare supply chains. To that end, the Cloud Security Alliance (CSA) recently published agnostic guidance to help healthcare delivery organizations (HDOs) overcome pervasive challenges associated with third-party vendor evaluations and cyber risk management. In the new paper “Healthcare Supply Chain Cybersecurity Risk Management,” CSA authors outline several best practices, including:
1. Systematically inventory all third-party vendors and suppliers. Evaluations must include both direct suppliers and suppliers of suppliers, as well as non-traditional connected systems and IoT devices — all of which have information system components that could introduce cybersecurity risk, such as providing remote, third-party privileged access to critical internal resources. Report authors note that any cloud-based application or service provided must also be evaluated — including those purchased with a credit card outside of IT’s or finance’s formal procurement and approval processes.
2. Tier suppliers based on risk, using a third-party risk rating service if possible. Part two of this inventory process is categorizing vendors based on mission priority or impact to the organization, as well as level of risk. For any third-party vendor utilizing cloud services (essentially every organization today), assessments should evaluate cloud security practices across each stage of the cloud data lifecycle: create, store, use, share, archive and destroy. CSA authors offer an initial framework to follow, while encouraging organizations to also reference ISO, NIST, HITRUST and other industry standards. They note that using third-party risk rating services and qualified vendor lists can be helpful in achieving more consistent ratings.
3. Identify and define key risk areas. Privilege escalation is the No. 1 attack vector of risk for healthcare organizations today. Using stolen credentials, attackers can begin moving through systems looking for opportunities to escalate privileges and exploit powerful privileged accounts to install ransomware. Despite this reality, many healthcare organizations and their suppliers fall short in securing and monitoring privileged accounts as they focus on HIPAA-specific safeguards for securing ePHI.
4. Provide supply chain vendors with risk-prioritized action plans — and make following them a mandatory part of doing business. Extending critical Identity Security practices to include privileged access management should top healthcare organizations’ action list. Doing so can help protect against ransomware and dramatically drive down risk across the supply chain by enhancing visibility and control over privileged accounts, isolating and monitoring privileged activity, removing direct access to tier 0 systems, and minimizing credential exposure and privilege escalation opportunities.
Secure the Care Continuum With Identity Security
Properly prioritizing privileged access management as a part of a comprehensive Identity Security program can help “ensure that resources are deployed first to issues that matter most,” strengthening cyber resilience across the care continuum to improve outcomes for all.























