
2022 ransomware attack learnings can inform 2023 cybersecurity strategies, helping organizations combat threats and reduce risk with greater confidence.
The CyberArk 2022 Identity Security Threat Landscape Report shows the ransomware attack vector continues to be a cybercrime hot spot, but the scale is staggering: 73% of global IT security decision-makers reported at least one ransomware attack on their organization in the last 12 months. Nearly 100% claim to have a defense-in-depth strategy in place to combat ransomware, which is encouraging. But since there’s always room for improvement, I dug into the data to understand what made some organizations more attractive to ransomware actors than others, and what is (and isn’t) working when it comes to ransomware prevention.
But first, a quick 2022 ransomware recap …
Ransomware was more prolific than ever in 2022, fueled by ransomware-as-a-service (RaaS) groups like ALPHV (BlackCat) and Black Basta, as well as the return of the infamous REvil organization.
The number of ransomware-based breaches grew by 41%, with attacks taking 49 days longer than average to identify and contain, according to IBM’s 2022 Cost of a Data Breach report. The same report found that destructive ransomware attacks increased by more than USD $430,000 in cost for victim organizations.
This sustained ransomware activity put increased pressure on supply chains, disrupted operations and caused reputational damage. Many organizations opted to pay ransoms despite widespread guidance against the practice. However, major incidents throughout 2022 underscored the fact that giving in to ransomware demands further perpetuates attacks.

All the while, organizations ramped up digital and IT initiatives (continuing the tectonic shift called digital transformation), creating a massive surge in digital identities and expanding the attack surface. It only takes one compromised human or machine identity to launch an attack, and our data shows ransomware actors took full advantage of this by targeting companies of all sizes and sectors.
A ransomware attack analysis: Organizations in the crosshairs share six commonalities
Though ransomware attacks didn’t discriminate based on organizational size or sector, a deeper dive into the CyberArk 2022 Identity Security Threat Landscape Report reveals several notable differences between organizations targeted by ransomware attacks and those not targeted in the last 12 months:
1. Overly generous access provisioning. In targeted organizations, 56% of workforce users had access to sensitive corporate data, compared to only 39% in organizations not targeted. Seventy-five percent of targeted organizations granted non-human accounts/bots access to sensitive data; this percentage drops to 50% in organizations not targeted by ransomware attacks.
Organizations need more effective strategies to manage sensitive access and enforce least privilege to align with the Zero Trust “trust nothing, verify everything” philosophy.

2. Behind-the-curve cybersecurity investments. Eighty-two percent of security leaders in targeted organizations said their company prioritized business operations over robust cybersecurity in the last 12 months (70% of security leaders in non-targeted organizations agreed). Additionally, these security leaders were 13% more likely to say their recent cybersecurity decisions contributed to new areas of vulnerability.
Cybersecurity can’t take a back seat to digital investments because, ultimately, positive business and customer outcomes hinge on both.
3. More churn-related risk. Seventy-four percent of security leaders at targeted organizations agreed the accelerated rate of employee churn and termination caused security issues, compared to 52% of security leaders at non-targeted organizations.
When someone leaves an organization, their access must be deleted immediately and automatically, not left to periodic reviews.
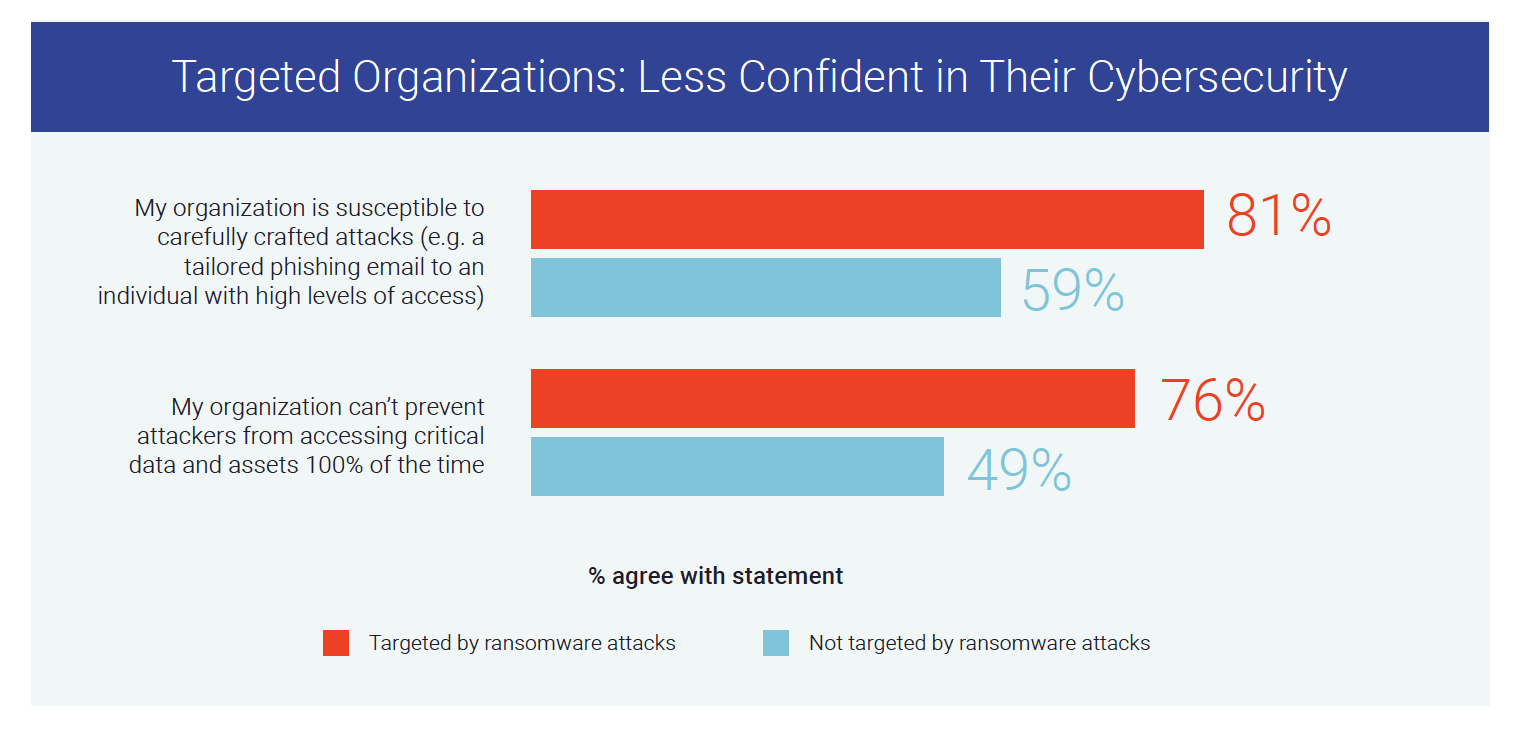
4. Less cybersecurity confidence. Organizations that experienced ransomware attacks displayed less confidence about their cybersecurity overall. Security leaders were 22% more likely to say their organization was susceptible to carefully crafted attacks, such as phishing, and 27% more likely to say their organization cannot prevent attackers from accessing critical data and assets 100% of the time, compared to leaders at non-targeted organizations.
There’s no silver bullet for ransomware, but with an assume breach mindset, a strong defense-in-depth approach and an identity focus, organizations can confidently drive greater cyber resilience.
5. Irregular breach reporting. Both targeted (92%) and non-targeted (91%) organizations paid nearly the same amount of attention to revisiting their cybersecurity strategy and incident response planning. But that similarity ends when it comes to reporting on breaches. It’s alarming to see nearly three-quarters (71%) of targeted organizations (versus 39% of non-targeted) said they do not report successful data breaches to stakeholders, which places organizations at greater risk for non-compliance fines and penalties.
Prioritize transparent reporting and communication. Review cyber incident response strategies and playbooks rigorously and involve stakeholders in improving them.
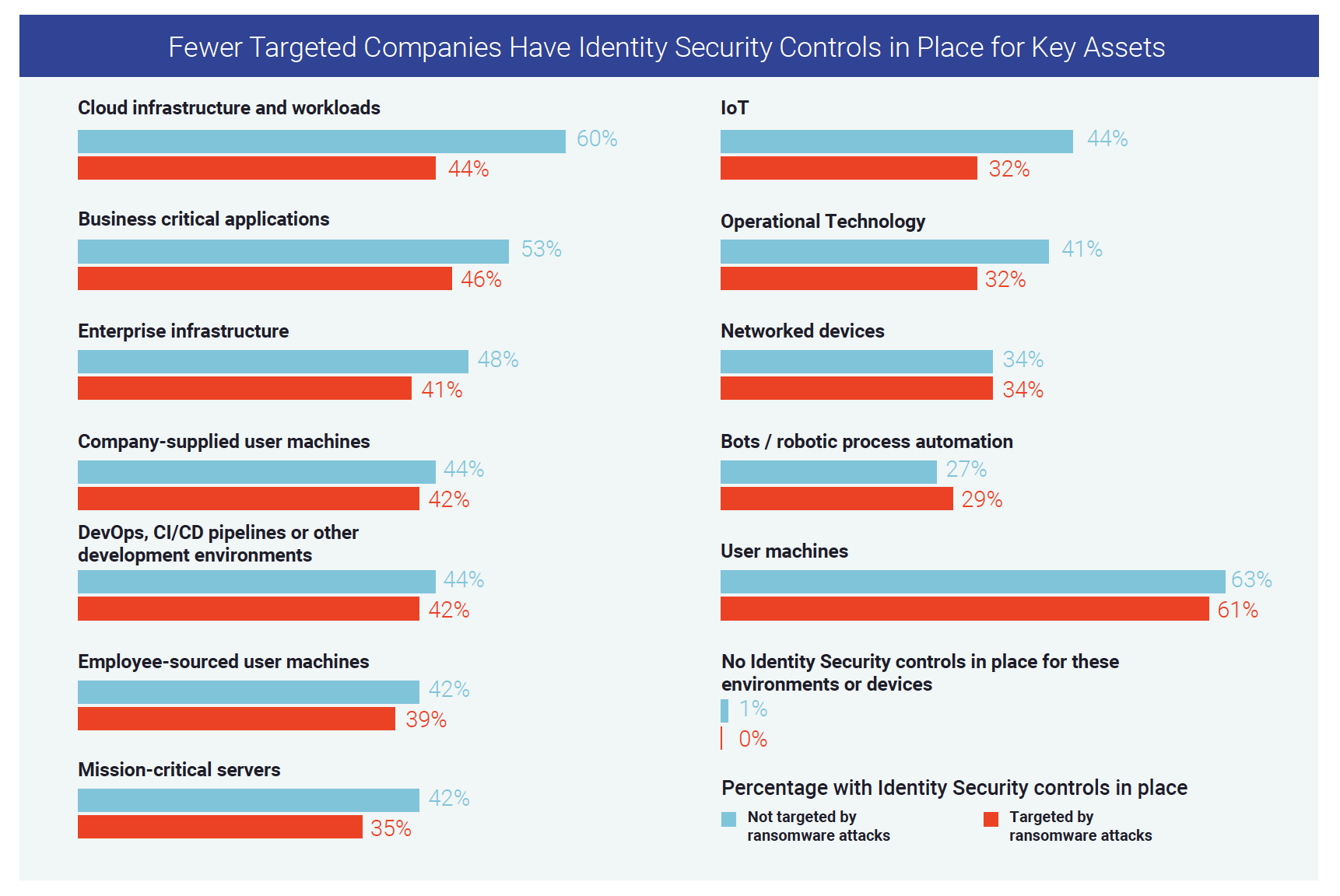
6. Inadequate Identity Security controls to protect cloud assets. Significantly fewer targeted organizations (44%) had Identity Security controls in place to protect cloud infrastructures and workloads compared to non-targeted organizations (60%). This is despite more than half of respondents indicating their organization had accelerated cloud migration over the past year.
Don’t wait until your organization is drowning in cybersecurity debt to address cloud workload security and hold up your end of the Shared Responsibility Model. A proactive, automated approach today can help you avoid major issues tomorrow.
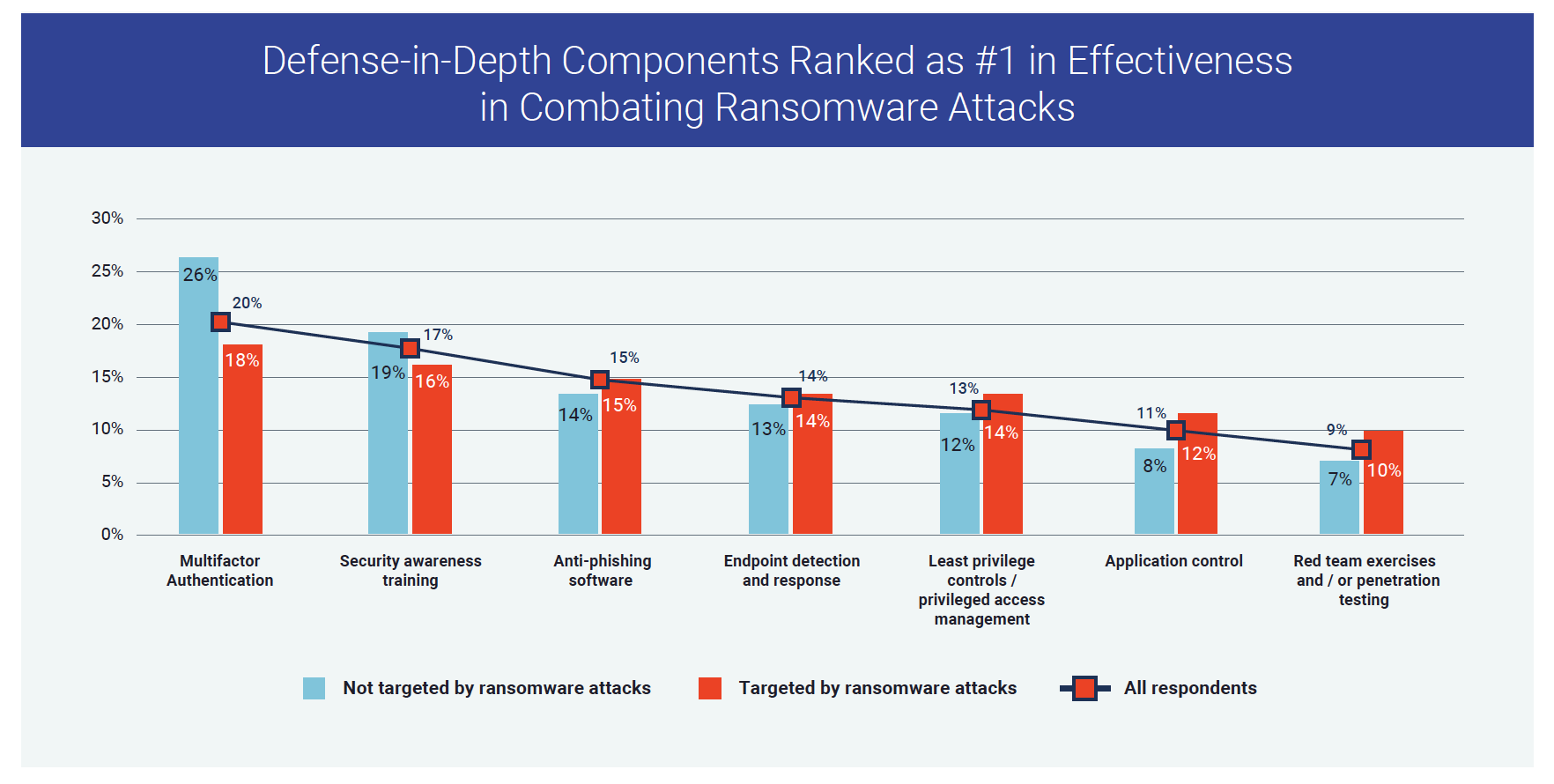
Interestingly, nearly 100% of both targeted and non-targeted groups said they had a defense-in-depth strategy in place, using multiple layers of security to reduce vulnerabilities, contain threats and mitigate risk. Yet there wasn’t broad consensus on the most effective defense-in-depth components, as shown below. What stood out to me is that slightly more targeted organizations view least privilege controls, application control and red teaming as most effective. This suggests security teams recognize (perhaps with the benefit of hindsight) that threat actors will seek out ways to circumvent MFA and other existing security controls, and are placing stronger emphasis on ways to minimize the blast radius of attacks.
These varied perspectives also remind us that ransomware defense isn’t just about technology. Even the most advanced detection tools can’t stop every piece of ransomware from running, every single time. Overall system hardening, systematic attack surface reduction, a consistent approach to asset security and fundamental (also called “basic” by security practitioners) security best practices, such as local admin rights removal, can dramatically improve an organization’s ability withstand a ransomware attack. Everyone and everything — people, processes and technology — play roles in effective (and realistic) ransomware prevention strategies that focus on stopping inevitable attacks before they cause harm.
As we move forward in 2023, consider how Identity Security countermeasures can help your organization improve ransomware readiness and reduce risk exposure. To delve deeper, read our full report findings — including respondents’ top five ransomware protection takeaways — in “Ransomware Attacks: What Can We Learn From Them?” And as a contributing partner of the EUROPOL European Cybercrime Centre’s NoMoreRansom Project, we also recommend browsing these ransomware FAQs, mitigation steps and free decryption tools.





















