
Eighty-seven percent of IT decision-makers1 say their organizations are implementing DevOps, yet achieving DevSecOps excellence isn’t easy, especially as machine identities and secrets continue to pile up across development pipelines and application portfolios. While there isn’t one specific standard for evaluating DevSecOps maturity, most teams would agree that both speed and security are critical metrics — and that the two are at constant odds.
As organizations continue to move to the cloud and evolve hybrid architectures, here are nine reasons why developers need a simplified approach to secrets management to keep moving fast while giving security teams a streamlined way to enforce policies.
1. “Elite” DevOps organizations — or the highest-performing teams — routinely deploy on demand and perform multiple deployments per day.2 For instance, Amazon engineers reportedly deploy code every 11.7 seconds, on average.3
2. Compared to low-performing teams, elite DevOps teams have 973x more code deployments, and a 6570x faster lead time from commit to deploy.4 To put it simply, they focus on fast.
3. CI/CD pipeline automation enables these DevOps teams to build and deploy applications at unprecedented speed and scale. It also creates new machine identities and application secrets — credentials, SSH keys, certificates, API keys — in massive quantities. Today, machine identities outnumber human identities 45:1.5
4. In half of organizations,6 the task of securing application secrets is left up to developers, who often emphasize speed and collaboration over proper security practices as they work under increasing pressure and tight timeframes.
5. In fact, 36% of developers say meeting deadlines7 is the primary reason their coding still possesses vulnerabilities. Yet cybersecurity debt in the form of unsecured secrets in code can compound rapidly with every release.
6. Security teams face an extremely difficult balancing act of enabling development velocity while consistently enforcing fundamental cybersecurity policies, such as least privilege, across the organization: 80% admit that developers have more privileges than they need.8
7. Many organizations rely on the native secrets management capabilities in their cloud and DevOps tools to simplify development and operations. But when secrets are stored and managed differently across various teams and projects — which 87% of organizations say is the case9 — “secrets sprawl” can cause conflict with centralized security goals, create opportunities for cyber attackers and have a dangerous ripple effect down the software supply chain.
8. Seventy-one percent of organizations suffered a successful software supply chain-related attack that resulted in data loss or asset compromise in the last 12 months.10
9. Shifting left by finding a more secure, consistent way to access secrets doesn’t just enhance overall cybersecurity posture — it can also unlock new levels of efficiency. Streamlining and automating secrets management processes, such as onboarding applications and rotating secrets, can accelerate cloud migration efforts by unblocking development, keeping existing workflows intact and making it easier for developers to code securely from the start. It’s by integrating security practices throughout the development process that top-performing DevOps teams are 1.6 times more likely to meet or exceed their organizational goals.11
As you build out your comprehensive Identity Security program, securing machine identities and application secrets everywhere they exist is critical to reducing security vulnerabilities, minimizing the attack surface and streamlining operations. But it can’t slow down development teams or delay automation initiatives. After all, speed is the currency of business.
With the right centralized secrets management approach, you won’t have to choose between speed and security as you work toward DevSecOps maturity — you’ll get the best of both worlds.
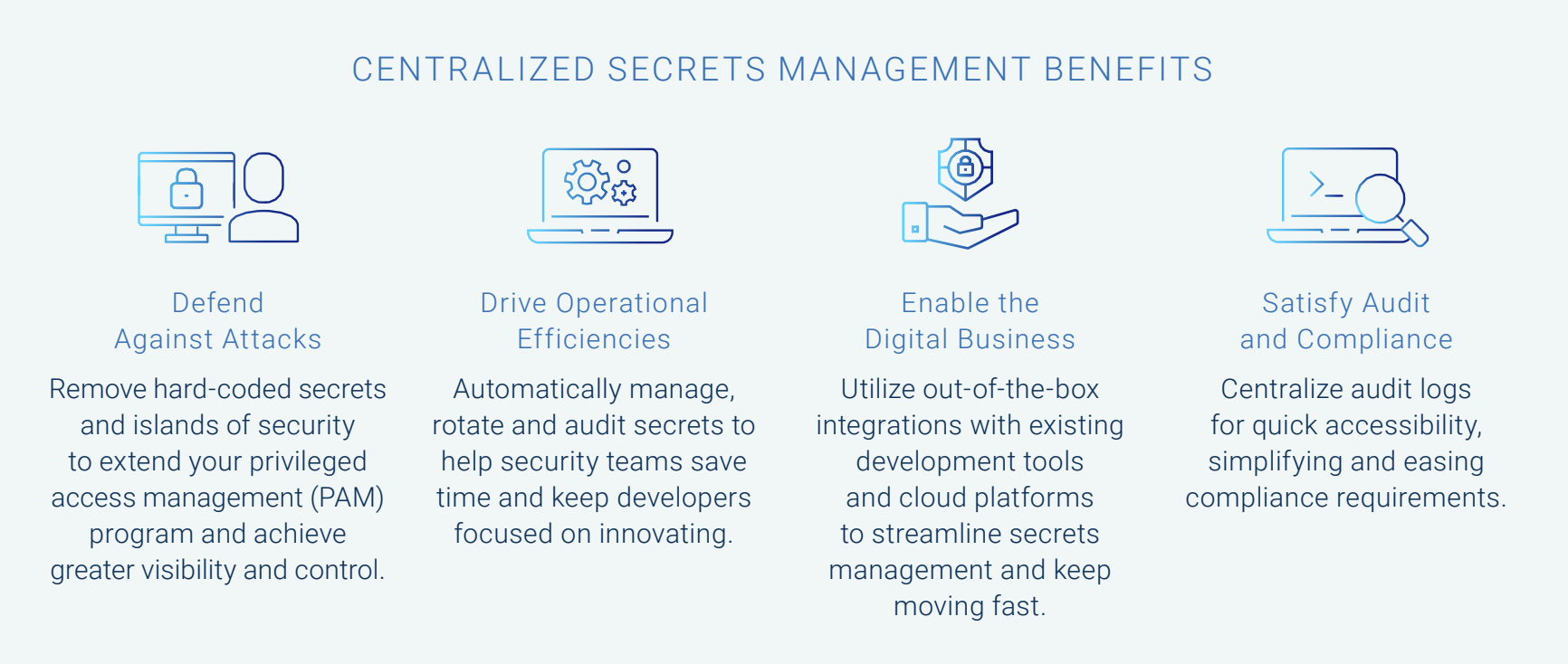
With CyberArk, you can strengthen security across the DevOps pipeline and add value to enable your digital business. Our recently launched Secrets Hub, a SaaS solution that is part of the CyberArk Identity Security Platform, delivers effective secrets management in hybrid environments, fulfills developer preferences for choice and gives security teams a way to retain centralized control and enforce unified policies over secrets using existing processes and infrastructure.
SOURCES
1: Puppet 2021 State of DevOps Report
2,4,11: Accelerate State of DevOps 2021 Survey
3: Tech Beacon, “10 Companies Killing it at DevOps”
5,6,8,9,10: CyberArk 2022 Identity Security Threat Landscape Report
7: HelpNetSecurity, “86% of Developers Don’t Prioritize Application Security”






















