
Identity security and Zero Trust have emerged as critical components in the defense against quickly evolving cyberthreats. Together, the solution and the approach support a default stance of “never trust, always verify,” with every risky action requiring authentication, authorization and audit. In the CyberArk 2023 Identity Security Threat Landscape Report, we found that 74% of organizations have begun the implementation of Zero Trust initiatives, with another 18% planning to do so in the next 12 to 24 months. If you’re reading this blog, you may be on a team driving these strategic initiatives and working with cybersecurity vendors to implement them. And if you haven’t yet considered extending identity security over your desktops and servers, it’s high time you do so. Read on for the why and how.
When working on strategic programs, some investments in cybersecurity, such as multi-factor authentication (MFA) and Single Sign-On (SSO), are widely recognized for reliably delivering relief to the defending teams – and, as such, prioritized. Some are even explicitly called out as examples of required capabilities, such as MFA. Critically, though, these programs remain no more than a set of siloed technologies for far too many Zero Trust implementations as technologies are viewed as belonging to certain domains (for MFA, that would be the IAM domain) instead of a broader angle.
The omissions are the most glaring when you look through a holistic identity-first approach lens, especially considering the first mile of user access and the last mile of information consumption – the endpoint. In fact, according to the Identity Security Threat Landscape Report, 79% of 2300 cybersecurity experts around the globe indicated that Identity Management is the most critical principle for successful Zero Trust initiatives, followed closely by endpoint security device trust (78%).
These stats imply that these capabilities are vastly different. But are they? Should we consider some capabilities of identity management and security as critical contributors to endpoint security?
I certainly think so.
Zero Trust in the Endpoint Department
If your day-to-day job lies in Identity and Access Management (IAM), you should be familiar with many paradigms that fit into and comprise Zero Trust. Those include least privilege, zero standing privilege (ZSP), just-in-time (JIT) access and privilege, continuous authentication and risk assessment. The same logic should apply to endpoints – both workstations and servers. Not for nothing, the principle of least privilege (PoLP) is designated as the cornerstone of Zero Trust. It is an ever-present recommendation of auditors and authorities in the cybersecurity field.
So, if your endpoint security strategy is built around capabilities that scrutinize applications, processes and actions and respond to those deemed malicious, your Zero Trust initiative should get some attention in the endpoint department. After all, isn’t Zero Trust fundamentally about proactive rather than reactive measures?
Now consider the simple diagram below. A very traditional endpoint security setup would include a combination of unified endpoint management (UEM) and endpoint detection and response (EDR). These technologies, while providing a near-complete coverage of an attack kill chain, are very asset or resource-centric, meaning they usually focus on specific files, folders and processes. What should have been there from the very start – the identity context – has been notably missing. Analysts and the industry recognize this and have now expanded detection and response to include protection from identity threats in the form of ITDR.
But what about identity-centric prevention?
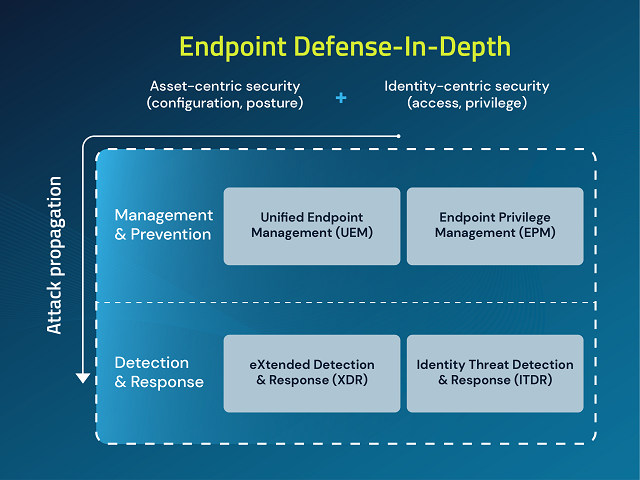
Despite the widespread adoption of various security measures, their effectiveness is ultimately contingent upon their convergence at the endpoint. The endpoint is where identities interact with critical resources and identity security and Zero Trust approaches must converge to provide a comprehensive defense. In today’s environment, characterized by an abundance of new identities, hybrid environments and sophisticated AI-driven threats, security is a question of how seamless your identity security fabric is and how complete the coverage of your assets is.
The Case for Proactive, Identity-centric Endpoint Security
Perhaps surprisingly, if you shift your mentality from the comfortably numb, “It’s not a question of if, but when,” back to attack prevention – and do a good enough job of setting endpoint privilege fundamentals – it may just be the security formula you’re looking for.
If you are a tenured defender, you may be thinking, “We tried that. It didn’t work 20 years ago – why should it work today? There’s a reason we ended up in an EDR-centric endpoint security camp.” All true – we did try, heard back from users, and opted for business agility and moving fast. Around 10 years ago, ransomware changed the game, and, as a result, cybersecurity today is a topic at the board level, and businesses today have to proactively inform the shareholders about security measures they take to prevent cyber incidents. What is also different now is that we finally have the right tools for the job.
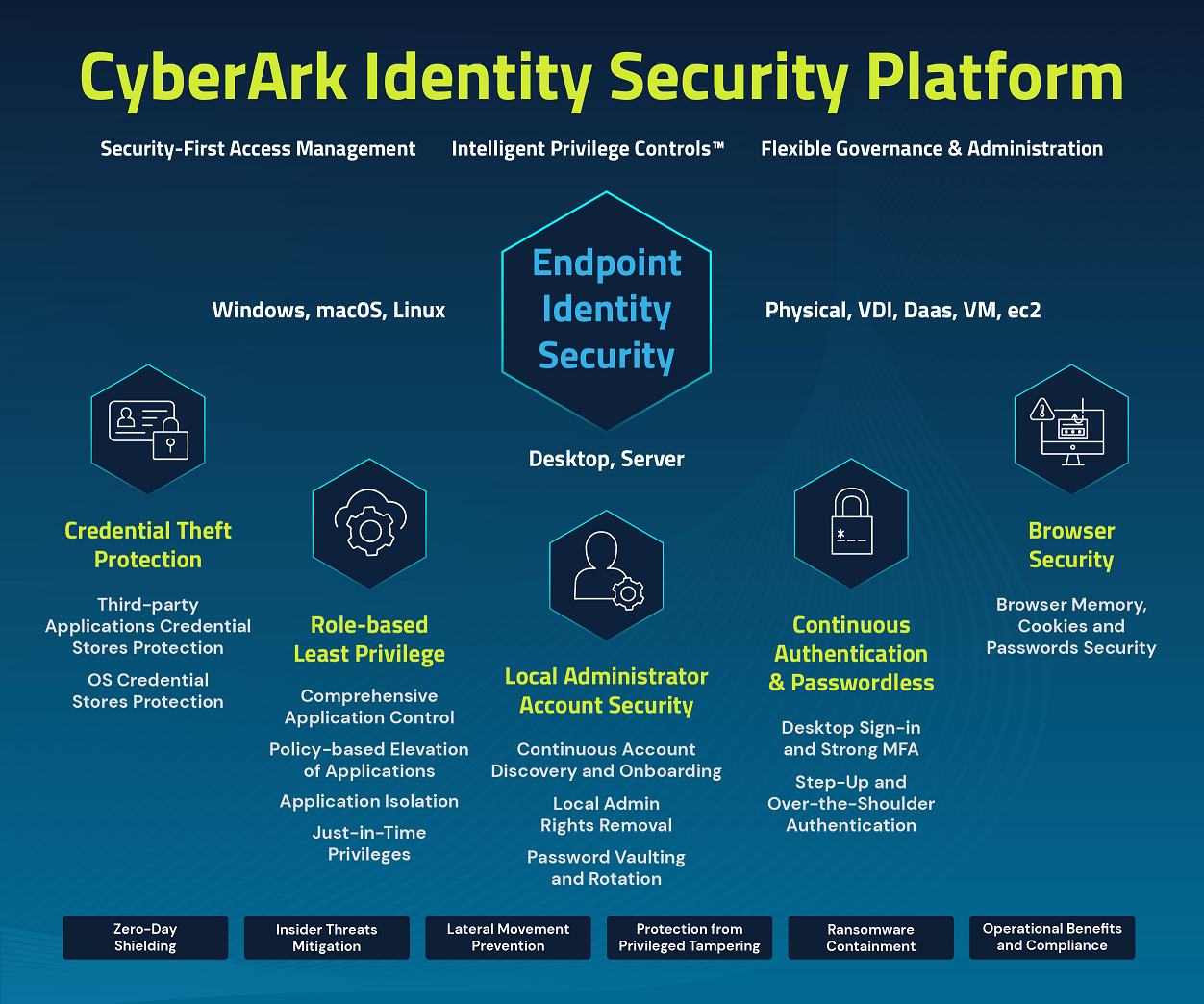
Identity – the new (and the last standing) security perimeter – must be woven into anything happening within our infrastructure. It should be continuous and reliable. As part of identity security, this job is performed by an endpoint identity security agent that provides the ability to discover and secure privileged accounts on the endpoints, secure user authentication mechanisms, provide passwordless and strong authentication injection points into user workflows, harden other security agents and browsers and play a critical identity bridging role to ensure a single point of authority over identities throughout the organization.
Couple this with common endpoint privilege management (EPM) that helps discover and remove local admin rights, provide automated and transparent elevation for applications and isolate risky applications from accessing certain resources, enforce role-specific least privilege, defend credentials and security tokens, and add additional ransomware protection – and you have an excellent foundational layer of defense.
Having completed this loop and extended the identity security over your workstations and servers, you’ve ensured that your endpoint security plays into your Zero Trust initiative. Getting this identity-centric prevention right will help your organization do four critical things:
- Extend identity security and Zero Trust to your workstations and servers
- Decrease the endpoint attack surface and prevent zero-day attacks
- Reduce IT security and operational costs with endpoint privilege controls
- Demonstrate compliance and meet audit requirements on the endpoint
Additionally, this layer of security can improve user productivity and experience for all employees.
In short, if you extend identity security over your desktops and servers, your users, administrators, SOC analysts and shareholders will appreciate it.
Andrey Pozhogin is a senior product marketing manager at CyberArk.























