
One unmanaged machine identity—whether a TLS certificate, SSH key, code signing certificate, or API secret—that’s all it takes to crash your website, halt transactions, and leave customers complaining about you in the comments.
No one is immune. In fact, 83 percent of organizations have experienced a certificate-related outage in the past 24 months. Even tech giants recently made headlines after expired renewals triggered hours of downtime and millions in lost revenue.
The problem is that every new application, API, connected workload, or automated process an organization spins up creates a machine identity—a TLS certificate, SSH key, code signing cert, or secret. Multiply that across hybrid and multicloud environments, and suddenly your security teams must manage tens of thousands of them.
Left unmanaged, machine identity sprawl becomes a silent disruptor that doesn’t just threaten uptime. It puts digital trust, compliance, and your reputation at risk.

Why machine identity sprawl is exploding (and why it matters)
How did we get here? Without machine identities, systems break down. Machine identities enable other machines—applications, AI agents, servers, bots, and IoT devices—to connect securely and exchange data.
However, the explosion of digital ecosystems makes the management of these identities more complicated and creates a storm that CISOs can’t ignore:
More volume. Tens of thousands—even millions—of identities (TLS certificates, SSH keys, code signing certificates, cloud access keys, and API secrets) are now proliferating unseen across apps, APIs, servers, and workloads, outnumbering humans 82:1. The rapid adoption of AI agents compounds the challenge, as each autonomous process requires its own keys, tokens, and certificates to interact with other systems.
Faster turnover. The lifespan of digital credentials is shrinking. Thanks to new security mandates and browser rules, TLS certificates that once lasted several years now need re-issuing as often as every few weeks. Ninety-four percent of security leaders are worried their organizations aren’t ready for shorter certificate lifespans—a gap attackers are eager to exploit.
More complexity. From key formats to cryptographic standards to post-quantum cryptography (PQC), tracking it all manually across cloud-native, hybrid, or multi-cloud environments is impossible for most organizations.
Machine identity sprawl becomes a business continuity risk with reputational, operational, and compliance fallout.
How poor visibility leads to outages and compliance risk
Most organizations don’t know how many machine identities they have—or where they live.
Without central visibility, security teams inherit overlapping responsibilities and no clear ownership, allowing keys and secrets to remain unrotated or misconfigured and certificates to expire silently. That is, until they break something critical.
Repeated outages caused by expired certificates erode trust with customers, boards, and partners. And teams that could drive strategic projects, innovation, and digital expansion are instead sidelined to work around the clock in firefighting mode.
For CISOs, this becomes a very bad operational headache. Real-world fallout from expired certificates is brutal—and expensive:
- Revenue loss. One expired certificate can take down APIs, digital services, or websites, costing millions per hour. A forgotten cloud access token can also trigger outages or service interruptions.
- Regulatory risk. When stale, untracked or misconfigured certificates expose sensitive data, organizations risk violating GDPR, HIPAA, and the Payment Card Industry Data Security Standard (PCI DSS), among other regulations.
- Reputational damage. Every digital disruption is a test of trust. When “secure” systems suffer persistent outages or compliance slip-ups, clients can (and do) migrate to the competitor.
- Security exposure. Attackers target unmanaged identities as entry points for lateral movement and ransomware. Forgotten SSH keys are especially dangerous because they don’t expire and can silently provide persistent access until discovered.
As certificate lifespans shrink and organizations rely on a growing mix of SSH keys, secrets, and code signing certs, failing to get ahead of these management challenges will only magnify outages, compliance exposure, and security risk.
A practical approach to tame sprawl and build resilience
First, organizations must establish clear policies and organization-wide standards for deploying and managing credentials. Define ownership, set up approval workflows, and track activity to ensure accountability, compliance and rapid response in the event of changes or incidents.
Next: Move toward automation. As certificate lifespans shorten and environments grow more complex, manually tracking thousands of machine identities in spreadsheets is a losing game. Automation is the only scalable way to stay ahead—and automated platforms now exist to inventory, manage, and renew identities of all types across all environments.
Here’s a quick breakdown of how automated certificate lifecycle management eliminates blind spots and helps security teams focus on higher-value security initiatives.
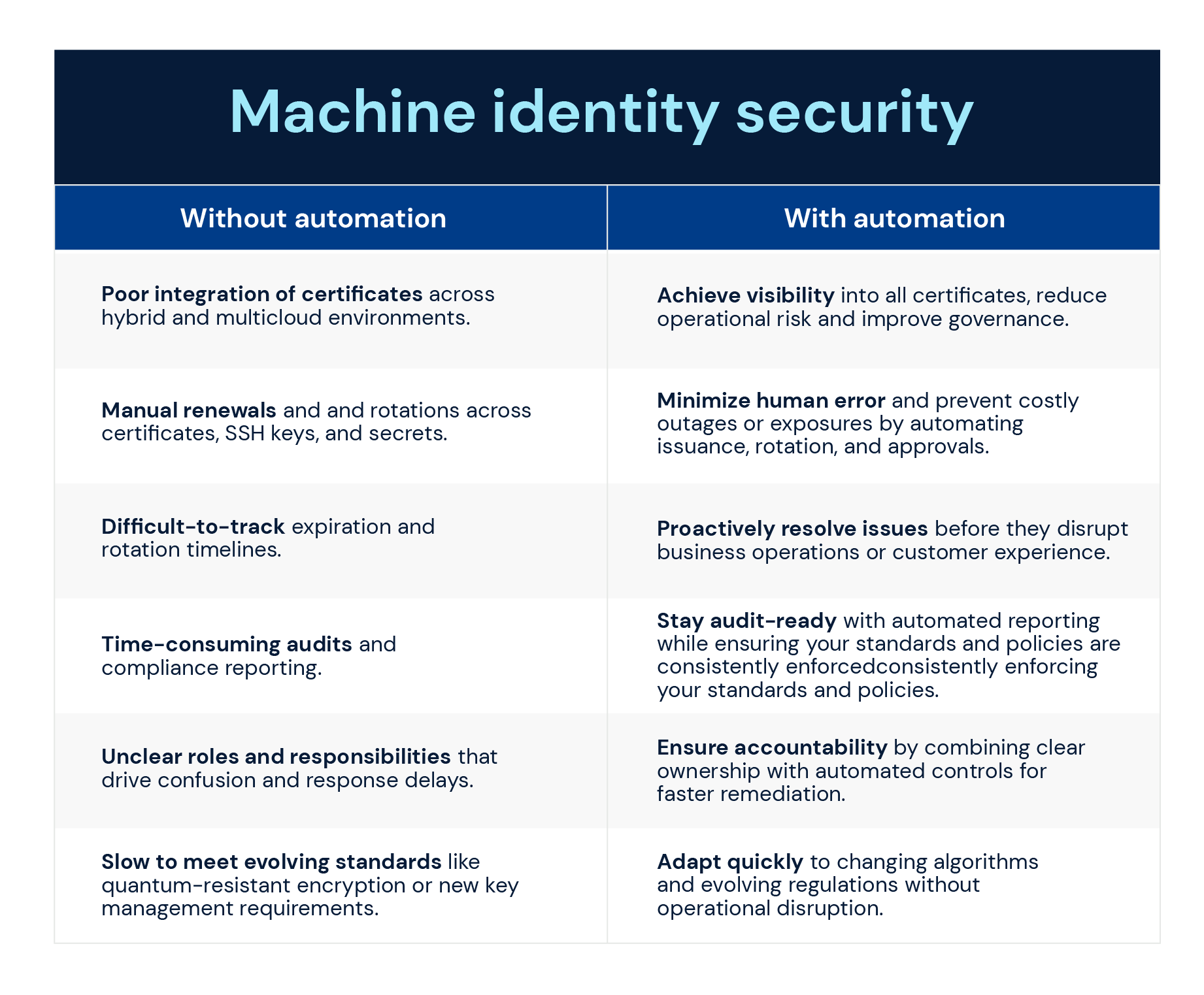
Turning certificate risk into a security and compliance advantage
What was once a back-office IT issue is now a board-level priority. Machine identity security directly impacts resilience, trust, and growth.
With proactive management, identities shift from a vulnerability to a competitive advantage. Organizations embracing automation and clear policies may reduce the likelihood of outages, improve compliance posture, and be better positioned to unlock new opportunities confidently.
The message is clear: Don’t let invisible complexity disrupt your future. Automated, policy-driven machine identity management—covering certificates, SSH keys, code signing certs, and secrets—with strong governance can help safeguard revenue and support greater resilience in the face of future challenges.
Florin Lazurca is a product marketing director at CyberArk.























