
An attacker doesn’t need your password anymore. They don’t even need to break your MFA. They just need to get ahold of your session. And once they have it, they are you.
Organizations have focused on securing access for two decades, initially relying on passwords. When passwords proved weak and insufficient, multi-factor authentication (MFA) emerged as the new standard. It was a substantial improvement, adding an extra layer of security to verify users. But, as organizations increasingly rely on digital identities to enable access, protecting authentication alone is no longer enough. Attackers have adapted, shifting their focus beyond login security.
They are no longer just stealing passwords or bypassing MFA. Instead, they are finding ways to sidestep these controls altogether.

Identity: The Last Perimeter?
For years, organizations have built security around protecting a well-defined perimeter. But with cloud adoption, remote work and increasingly sophisticated attacks, the traditional perimeter has disappeared. The network or endpoint is no longer the primary control point—identity is. Once an attacker gains control over a valid identity, they can move undetected through an environment.
So, many now refer to identity as the new security perimeter. But is it?
Rethinking Identity as a Security Perimeter
Security perimeters imply a defined boundary where security measures begin and end. But identity doesn’t work that way. Treating identity as a single-layer security approach is flawed. Looking back, you’ll realize that we (cybersecurity defenders) have made this mistake before for both the network and endpoint controls. Realizing we needed to introduce a post-breach mindset, we added detection and response practices, knowing no single control alone can keep the bad guys away.
Initially, firewalls relied on the concept of in/out and an ‘unbreachable wall,’ but this approach was eventually dismantled. Similarly, traditional antivirus solutions moved beyond the idea of ‘100% prevention’ on the endpoint. Identity security must follow this evolution, transitioning from static, perimeter-based controls to continuous and adaptive defense-in-depth protections.
And… modern attackers have adapted.
Instead of trying to steal credentials, they are hijacking authenticated sessions. Instead of breaking MFA, they are exploiting token-based authentication mechanisms. The goal is simple: act as a legitimate user without triggering any alerts.
In reality, identity expands far beyond a single perimeter—it’s an interconnected web of authentication, authorization and access control that needs continuous protection.
Bypassing Authentication: Attack Tactics in the Wild
Session hijacking is no longer just about stealing cookies from web browsers. As attackers adapt to stronger authentication measures like MFA, they increasingly target session-based authentication mechanisms across various environments, including APIs, machine-to-machine (M2M) communications and OAuth-based access.
Techniques such as MITRE ATT&CK T1539 (Steal Web Session Cookie) and T1528 (Steal Application Access Token) highlight how attackers extract authentication materials to impersonate users. This threat is not just limited to privileged users—it extends to workforce users with elevated privileges accessing high-risk applications or performing critical activities.
Several real-world breaches highlight these evolving techniques:
- Okta breach (2023): Attackers compromised a third-party support system and stole session tokens, allowing them to impersonate users without needing credentials or MFA.
- MGM Resorts attack (2023): Social engineering led to an initial foothold, but persistence came from hijacking authentication mechanisms—likely through stolen session cookies.
- Lapsus$ attacks (2022): This group used techniques like stealing session tokens and social engineering support teams to take over accounts, bypassing MFA protections entirely.
Attack Walkthrough: How an Attacker Hijacks a Session
Understanding how attackers hijack sessions is crucial for enhancing security measures. The following steps outline the typical process an attacker follows to bypass authentication controls, gain unauthorized access and escalate their privileges within a system:
- Initial access: The attacker gains access to a user’s endpoint through phishing, malware or exploiting a vulnerability. They might use an infostealer to grab browser-stored session cookies or deploy malware to extract authentication tokens from memory, using techniques like T1003.001 (OS Credential Dumping: LSASS Memory).
- Session theft: Using tools like Mimikatz or RedLine Stealer, the attacker extracts active session cookies or tokens, effectively capturing the user’s authenticated session.
- Replay attack: The attacker injects the stolen session token into a new session—no password or MFA prompt is required. The attacker now operates as the legitimate user, inheriting their permissions.
- Lateral movement and persistence: The attacker escalates access by pivoting to more critical systems, using the compromised session to generate additional tokens or establish new persistence mechanisms.
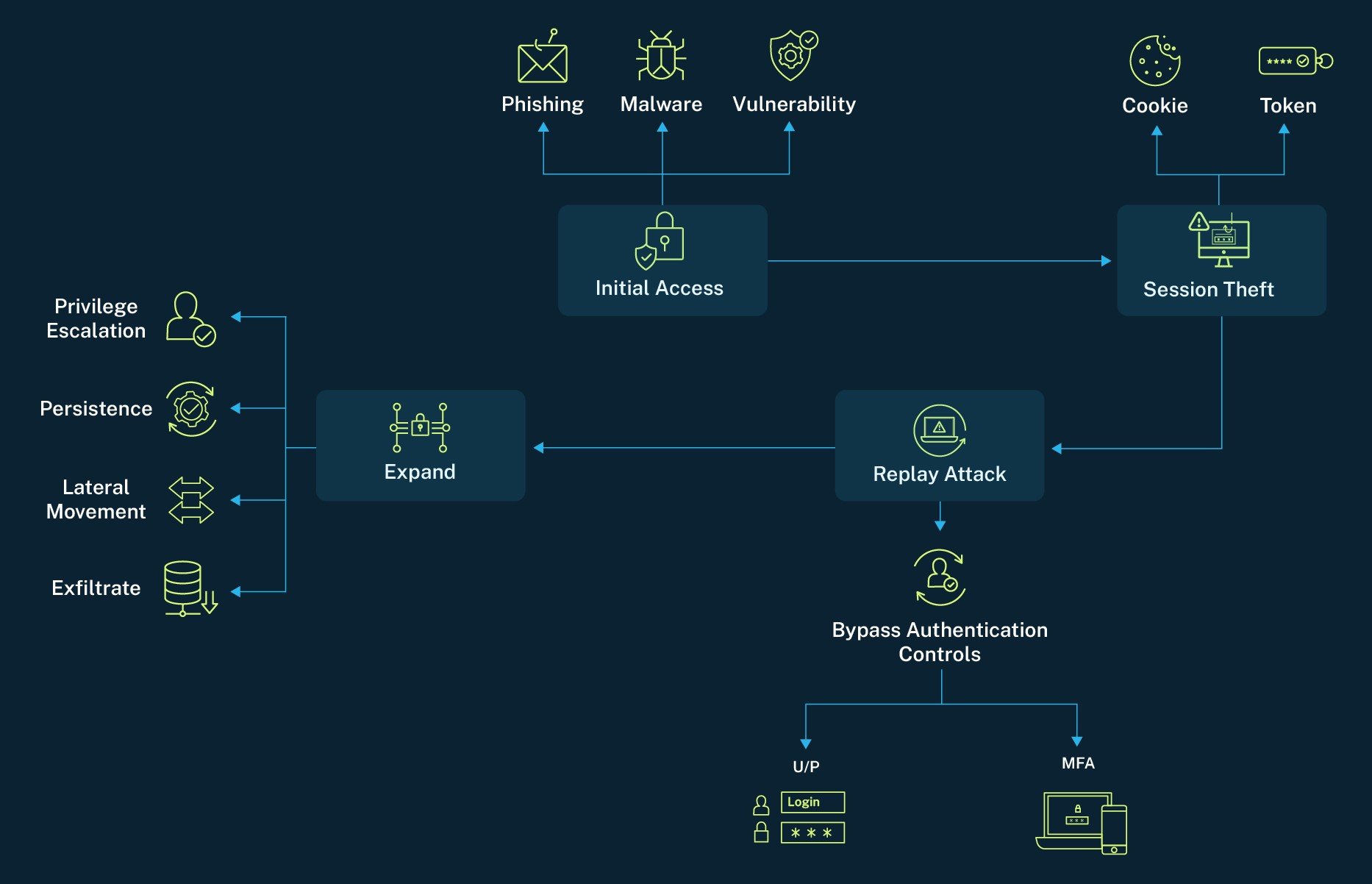
Compromised Session Attack Flow
Session Hijacking and Token Theft: The New Attack Vector
Once authenticated, users receive a session cookie or token that grants them access to applications and services. These tokens are supposed to be secure—but attackers have found ways to steal and reuse them:
- Stealing session cookies: Malware like RedLine Stealer and Raccoon Stealer actively extracts browser session cookies, allowing attackers to bypass login prompts entirely. MITRE ATT&CK T1539 (Steal Web Session Cookie).
- Token theft from memory: Attackers use tools to extract authentication tokens directly from memory, as seen in attacks leveraging infostealer malware mapped to MITRE ATT&CK T1528 (Steal Application Access Token).
- Session fixation and manipulation: Attackers gain access as authenticated users by injecting or replaying session tokens, a method commonly exploited under ATT&CK T1550.004 (Use Alternate Authentication Material: Web Session Cookie).
Why MFA Alone Is Not Enough
MFA is a good technology, yet it alone cannot withstand the evolving tactics and techniques, in this specific case, attacks that bypass MFA altogether.
While MFA strengthens authentication, it does not protect against session hijacking. Attackers who steal valid session tokens can bypass MFA altogether. This vulnerability underscores the need for additional layers of security, such as:
- Session monitoring and anomaly detection: Identifying unusual login patterns, concurrent sessions and location-based risks.
- Short-lived tokens and just-in-time (JIT) access: Reducing exposure by limiting the lifespan of authentication materials.
- Continuous authentication and risk-based access: Adapting security measures dynamically based on user behavior and risk signals.
This approach is necessary for privileged users and workforce users handling high-risk applications or performing sensitive activities. The risk doesn’t stop at admins—any user with elevated access can be a target.
Scaling Session Analysis with AI
Unlike the binary true/false decision at initial authentication or step-up authentication, session analysis is much more complex. Identifying threats means detecting anomalies, behavioral deviations and subtle signals that might indicate compromise.
This complexity is where AI can step in. AI-powered session analysis allows organizations to monitor sessions at scale continuously. A dedicated AI-driven agent can track all sessions, automatically identifying abnormal behaviors and highlighting potentially suspicious activity. Instead of relying on manual investigation for every session, AI helps security teams focus on what truly matters, flagging only those sessions that demand further inspection, reducing noise and improving response times.
Protection Beyond Authentication
MFA is critical, but it’s not enough. Attackers are no longer breaking in; they’re logging in—by taking over valid sessions. Organizations need to rethink identity security beyond just authentication.
Key steps to help improve security:
- Continuous authentication: Monitor session behavior in real time, not just at login.
- Adaptive session controls: Detect anomalies—like access from an unusual device or location—and force reauthentication or session termination.
- Token protection: Secure and rotate authentication tokens to prevent reuse outside their intended scope.
- Zero Trust mindset: Assume compromise and verify every action, not just the initial login.
You’ve done the work to secure logins, but what happens after that? If you don’t protect active sessions, you leave the door wide open.
To learn more about how CyberArk can help secure against pre- and post-authentication threats and the need to secure beyond the login, check out our eBook, “Beyond the Login: Modern Identity Security for the Workforce.”
Maor Franco is a director of product marketing at CyberArk.























