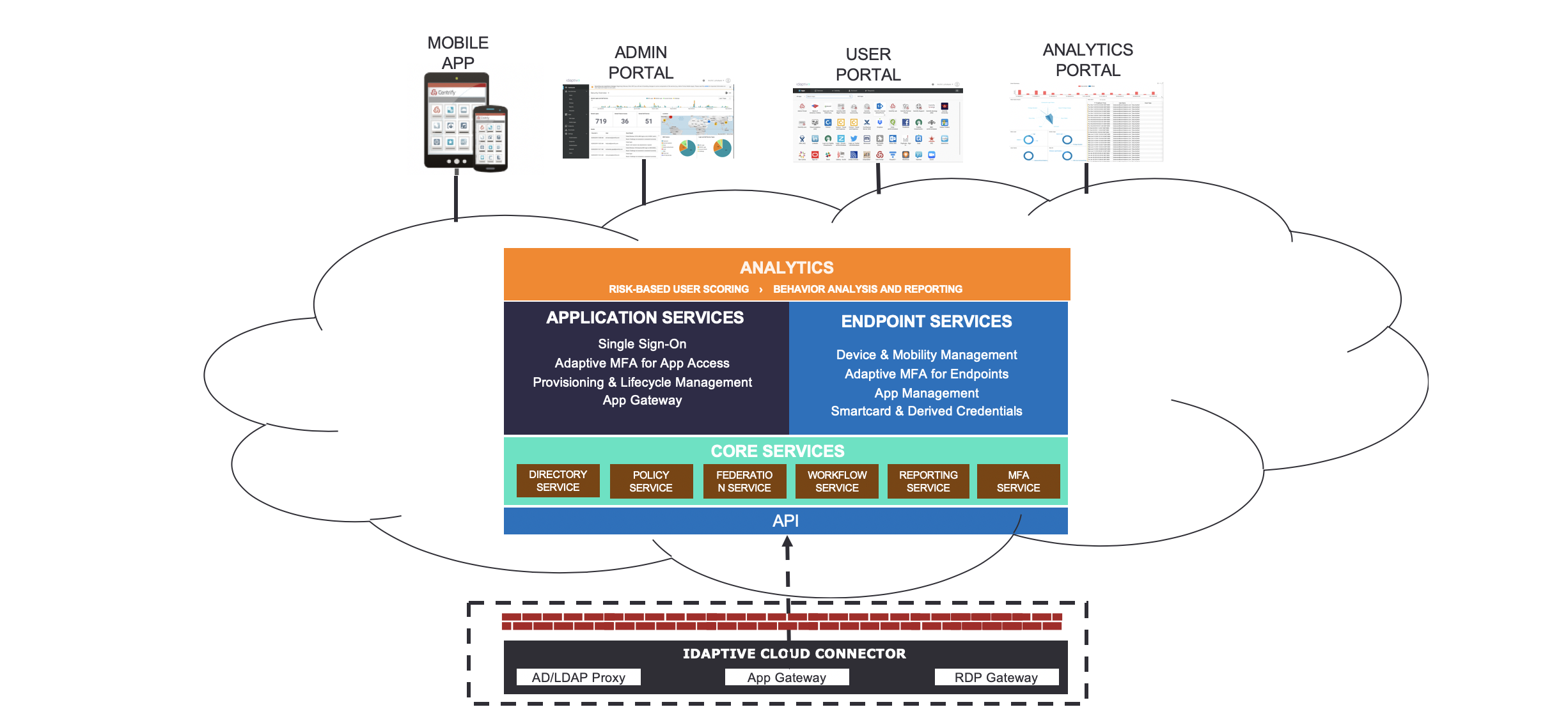
Fueled by advances in technology and widely-recognized business benefits, many organizations today are actively moving to cloud-based applications, platform services and infrastructure as a service. This trend, coupled with an explosion in mobile computing, means that IT must increasingly enable access of these applications, services and infrastructure anytime, anywhere. There are also new complexities related to digital transformation projects across the enterprise, which often involve building new web presences, online business models, applications for employees, partners and consumers. In turn, these paradigm shifts are encouraging CEOs, CIOs and IT organizations to rethink their traditional approaches to many foundational services within the organization.
One such foundational service is the enterprise directory – the single source of truth for all identity information related to individuals (employees, contractors, partners, consumers), endpoints (mobile devices, workstations and laptops) and even infrastructure (servers, network devices, etc.). Traditionally, most organizations have invested in building out a legacy enterprise directory framework based on an on-premise Microsoft ActiveDirectory (AD) or other directories based on Lightweight Directory Access Protocol (LDAP). While these frameworks served organizations well in the on-premises world, they fall short of enabling an organization to truly embrace the cloud and mobile world.
Designing, deploying and managing this legacy enterprise directory framework comes with extensive requirements to invest in people, processes, technologies and infrastructure. This in turn creates significant opportunity cost to any enterprise looking to extend their competitive advantage through new and forward-looking technology investments. These legacy frameworks also are limited in their authentication and authorization capabilities, especially in the new cloud world. Cloud applications and services increasingly leverage new protocols such as SAML, OpenID Connect, OAuth 2.0, as opposed to using traditional mechanisms like Integrated Web Authentication (IWA) using Kerberos or NTLM. These services are also limited in their ability to support the modern BYOD (Bring Your Own Device) and BYOI (Bring Your Own Identity) where individuals are consuming the organization’s services using their own devices and using their own identities from platforms that may include Facebook, Twitter, LinkedIn and others, in addition to federated services. Similarly, managing and securing access to cloud IaaS like AWS, GCP and Azure too can be a challenge with these legacy frameworks.
Designed precisely with this paradigm shift in mind, Idaptive’s Next-Generation Cloud Directory addresses many of the challenges detailed above. A highly scalable, performant and turnkey cloud service, the Idaptive Cloud Directory can scale up to tens of millions of users and devices, enabling organizations to deliver web-scale digital experiences to their consumers, employees, contractors and partners. The Directory supports comprehensive User and Device Management and Role Based Access Control through a Policy-Based framework that applications and devices can leverage to drive superior access security and demonstrate compliance. The Cloud Directory, along with the Idaptive Next-Gen Access Platform, also enables authentication via new protocols like SAML, OpenID Connect. OAuth 2.0, etc. while supporting legacy protocols like IWA.
CyberArk Idaptive’s market leading Adaptive Multi-Factor Authentication service is deeply integrated with the Cloud Directory, enabling organizations to implement stronger authentication assurance and risk-based access to applications and devices. Lastly, Idaptive’s Identity Lifecycle Management services, built to leverage the Cloud Directory, enable seamless provisioning from and to the Cloud Directory into Line of Business applications like Box or HR systems like Workday and BambooHR. And with an API interface that enables all interaction with the directory to be done via APIs, and an enterprise grade Secure Token Service integrated with the Directory, the directory enables not just IT admins, but also developers to integrate their applications with it.
The Cloud Directory will also soon deliver a brand-new paradigm called Brokered Authentication. Using Brokered Authentication, the Cloud Directory can serve as a virtual directory, allowing users to login to applications, endpoints and services using their existing enterprise credentials (AD or LDAP), enabling a seamless transition from an existing legacy directory to the Idaptive Cloud Directory.
If you’re looking to try the Idaptive Next-Gen Cloud Directory and accelerate your cloud and mobile first initiatives, sign up for our free trial here.























