
You recognize the importance of defense-in-depth and use multiple layers of security to protect your organization’s most important data and assets. But, like many organizations, you could be overlooking a critical step in containing cyber attacks early in their lifecycle by failing to remove local administrator rights.
The Foundation of Effective Endpoint Security
Users with local admin rights have the power to do virtually anything they want on their workstations. They can download applications, use any program, modify system configurations and even access and change powerful administrative accounts. No matter how strong your perimeter security may be – even with DLP, antivirus and other security products – a user with local admin rights can easily supersede these defenses (either unintentionally or maliciously) and install anything from unlicensed software to unsanctioned applications and dangerous malware. Similarly, these powerful admin rights can be used by attackers to steal additional credentials, elevate privileges and move laterally through the network.
Identifying where local admin rights exist, and removing those rights, is a critical first step toward strong endpoint protection. Yet, CyberArk research shows that 87 percent of organizations have yet to do so, which suggests that employee demands for flexibility and productivity are largely trumping security hygiene best practices.
The Privileged Pathway: Endpoint Attack Simulation
We recently held a webinar to shine a light on these endpoint security risks and explore common attack methods. Following are steps in an example attack scenario to illustrate the power of local administrator rights. To view the full simulation, tune in on demand.
- Phishing Attack to Land on a Workstation
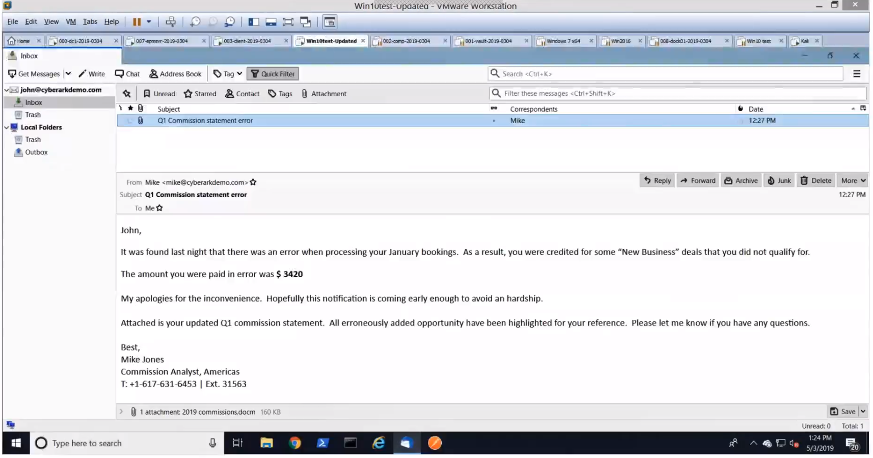
Attackers have myriad ways to launch their attacks – from crafty phishing attempts via emails to drive-by downloads to physical USB insertions. In this particular example, we showed how criminals often do their “homework” by reverse-engineering social media sites to gain information about their potential victims. Here, the attacker scoured LinkedIn, crafted a convincing email on commission reports and sent it to a number of sales people within an organization.
- Stealthy Command and Control Communication
It’s not long before an unsuspecting sales person reads a seemingly legitimate email, opens the attachment and enables macros to read its contents. With this, the attacker can launch an agent (a program that maintains a connection between the attacker’s device and the compromised host) that communicates back to their command and control. In this instance, the attacker uses Powershell Empire, a post-exploitation framework for computers and servers running Microsoft Windows or Windows server operating systems.
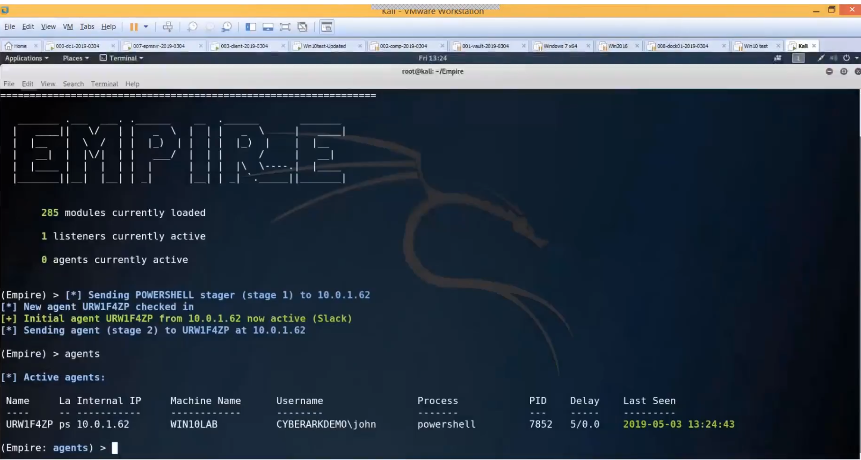
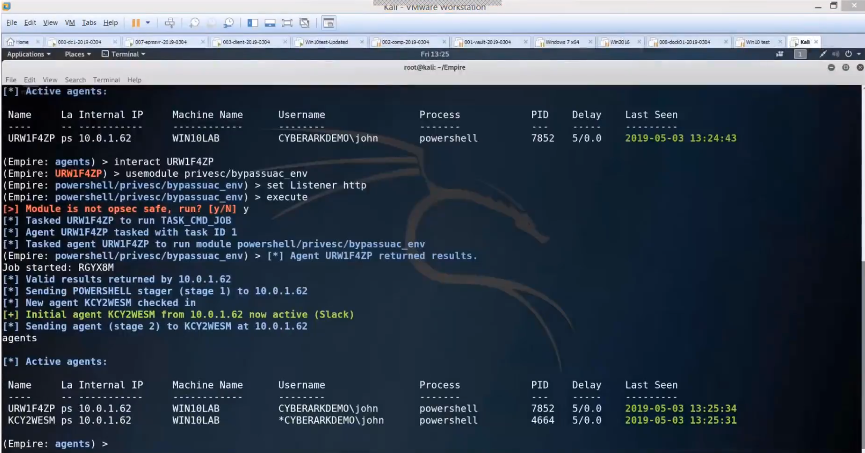
This agent is running as a standard user, so the attacker’s next step is to try to locate and steal administrator rights. By entering just three simple command sets, the attacker is able to locate those local admin rights and generate a new agent by using them. The attacker now has full control over the user’s machine – as both a standard user and as an admin. With full admin controls, the attacker can easily see which security tools are in place (e.g. antivirus and DLP) and begin turning them off to avoid detection.
- Ongoing Reconnaissance
Information gathering happens during the attacker’s initial target research and throughout the attack lifecycle. Once attackers have control of a machine, they can ramp up their investigation and use local admin rights to build persistence by creating scheduled tasks, modifying registry values or launching new services. This way, any time the machine reboots, the agent will as well, making it very easy for the attacker to make their way around the system.
- Privilege Escalation and Lateral Movement
Once the attacker lands on a workstation, they look to steal passwords to move laterally until they find privileged credentials that enable powerful access to target systems and assets. By stealing and utilizing legitimate credentials, attackers can persist on the network for an average of 78 days without being detected. This gives attackers ample time to seek out target systems and carry out their mission.
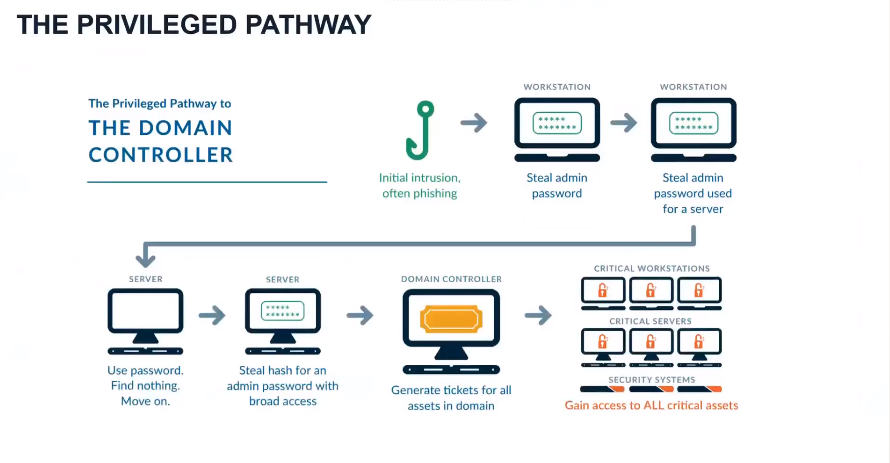
Credential Theft Plays a Major Part in Nearly All Targeted Attacks
While removing local admin rights greatly reduces the potential attack surface – it’s not the end of the story. Many credential theft attacks can be fully executed from a single user’s workstation by leveraging credentials stored on the device – from passwords for corporate social media accounts to administrative credentials stored in IT applications and remote access tools. These credential theft attacks have four (disturbing) things in common:
- They do not require admin rights to compromise credentials
- They are very easy to execute and well documented
- They are based on exploiting passwords stored in popular password storage locations such as DPAPI, Google Chrome, Filezilla and WinSCP
- There are numerous methods and effective tools available to attackers, such as the LaZagne Project
Advanced protection beyond the foundational admin rights removal step is needed to effectively detect and block attempted theft of Windows credentials and those stored by popular web browsers.
CyberArk Endpoint Privilege Manager helps organizations reduce risk by eliminating unnecessary local admin privileges, blocking credential theft attempts, auditing malicious behavior and strengthening the security of privileged accounts. Used in tandem with existing endpoint security tools, the CyberArk solution can dramatically strengthen protection and detection capabilities, without impacting business operations and productivity.
To learn more about CyberArk Endpoint Privilege Manager, download our solution brief and be sure to attend the full webinar, Spotlight on Administrator Rights and Privileged Credential Theft.























