![]()
Last week, Twitter suffered a breach that led to the compromise of numerous high-profile accounts, including those of Barak Obama, Joe Biden, Jeff Bezos and Elon Musk. I took the opportunity to speak with Nir Chako, Security Research Team Leader for CyberArk Labs and former Red Teamer, to get his breakdown on the attack.
While investigations are ongoing, Twitter reported it was the victim of a “coordinated social engineering attack.” The company confirmed that threat actors targeted and successfully manipulated a small group of employees and used their credentials to gain unauthorized access to an administrative tool that is “only available to internal support teams.”
According to Chako social engineering attacks like this one are “so effective because they use psychological manipulation to convince a person to take an action or divulge sensitive information that they shouldn’t. In fact, cyber attackers are the ultimate psychologists.”
Using these psychological tricks, the attackers were able to hijack Twitter accounts then post messages to dupe social media users into donating Bitcoin payments to fraudulent causes.
Originally thought to be the work of experienced nation-state attackers, it now appears the social engineering attack was conducted by a relatively unsophisticated group of hackers motivated solely by financial gain. Considering how powerful social media has become, their intentions, and corresponding global impact, could have been far worse.
The Twitter attack highlights the dangers of unsecured privileged access to critical applications, while reminding us how quickly any credential or identity can become privileged under certain conditions. If not properly secured, external attackers and malicious insiders alike can use them to unlock critical assets – currency, intellectual property, sensitive client records and more – causing irreparable harm to your business and reputation.
Social Engineering and the Human Opportunity
According to the 2020 Verizon DBIR, social engineering attacks keep increasing year-over-year. This makes sense since attackers nearly always look for the easiest point of entry. In most cases, social engineering techniques are a sure-fire way to get in the door. Wash. Rinse. Repeat.
In most cases, attackers utilize phishing emails to spoof their victims, developing highly customized messages that drive urgency or create fear. According to the 2020 DBIR, these social attacks arrive by email 96% of the time.
According to Chako, for attackers, “Every human represents an opportunity, no matter how strong their employer’s technological defenses may be. By targeting specific individuals, attackers can carefully study their behaviors, motivations, weaknesses – even their secrets – to build trust and credibility.”
Deconstructing the Twitter Attack
Chako provided me with his deconstruction of how the Twitter attack may have played out, explaining how the attackers successfully manipulated not one but two target victims: Twitter and the public at large. Below you’ll find his complete breakdown of the events.
PHASE 1
- Conduct Reconnaissance. The attackers likely searched social media profiles, like Twitter and LinkedIn, to pinpoint members of Twitter’s internal support team – specifically system admins that likely had access to the internal platform.
- Socially Engineer Twitter Employee(s). Using personal information gleaned from this reconnaissance work, the attackers successfully spoofed or coerced at least one Twitter employee and obtained their credentials.
- Gain Access to Target System. Using these credentials, the attackers were able to either directly access the internal admin platform OR use them to move laterally and escalate privileges until they could access the system. By using legitimate credentials, they were able to operate under the radar without being discovered.
PHASE 2
- Compromise Twitter Accounts. With access to, and control of, the internal platform, the attackers targeted 130 accounts and successfully compromised 45 by changing their associated emails without notifying their owners. If multi-factor authentication (MFA) was in place on an account, the attackers likely disabled this security layer and then issued a password change, which was sent to the new email address.
- Socially Engineer the Twitterverse. With these newly issued passwords in hand, the attackers began posting from the compromised Twitter accounts. This time, they preyed on Twitter users who might see the messages and feel compelled (out of compassion, peer pressure, political leanings, sense of urgency, etc.) to donate Bitcoin – with the influential figure’s promise they would double the amount. Here’s what they posted to Joe Biden’s verified account, for example:
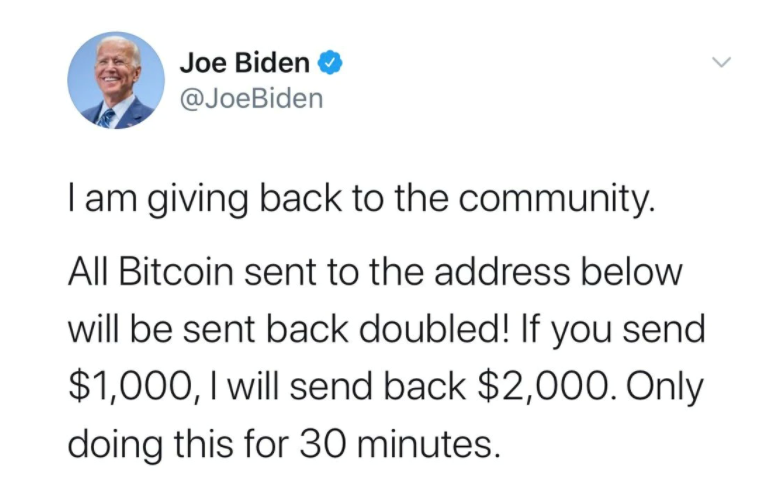
- Cash In. In just three hours, the fraudsters collected $118,000 in what the New York Times called “one of the most brazen online attacks in memory.”
Six Steps for Mitigating Risk of a Social Engineering Attack
Humans will always make mistakes and there’s no way to prevent social engineering attacks 100% of the time. The good news is there are specific steps your organization can take to significantly lower attackers’ success rates.
- Raise Awareness. Ongoing employee education and training on cybersecurity best practices – including how to spot a spoof – is a critical first step. Remember, urgent requests for payment or sensitive information should always raise red flags and require validation.
- Use Strong Passwords. As many employees continue to work from home, strong password policies are more important than ever. Start with the basics: Use strong passwords; don’t use them for multiple accounts; don’t share them and don’t save them in browsers.
- Prioritize Privileged Access Management (PAM). Privileged access is the route to your most critical assets. One of the best proactive ways to reduce risk is to implement strong PAM controls like the principle of least privilege to prevent credential theft, block lateral and vertical movement and stop privilege escalation and abuse. The Twitter attack should have every security leader asking right now: how are we identifying what our most critical systems, data and infrastructure are and who has access? Who is considered a privileged user (this includes business users) and what steps are we taking to manage, monitor and protect that access?
- Create a Conditional Access Policy That Mandates MFA. Based on Microsoft studies, an account is more than 99.9% less likely to be compromised if MFA is in place. Think of it this way: single factor authentication is a single point of failure. With conditional access, if a user wants to access a sensitive resource, then it must first perform MFA to reach it. This approach also helps organizations better balance security and user productivity.
- Use Dual Control Systems. No employee should have full access to sensitive platforms – your organization’s critical infrastructure – without multiple layers of security. Dual control means a duo is responsible for an action. For example, when a user tries to access a sensitive system, a request is created and must be confirmed by a second authorized user. It’s similar to the military’s “two-person concept,” designed to prevent malicious or accidental missile launches.
- Monitor and Respond to Anomalous Activity. By continuously monitoring privileged sessions and tapping analytics tools to automatically identify risky behavior or anomalous activity, your SOC team should be alerted immediately when something goes wrong – so you can respond fast.
The Twitter attack encapsulates the struggle many organizations have today: how to best secure the exploding number of credentials and identities that require privileged access to sensitive systems and data. There’s a critical need for a comprehensive approach to privileged access management that reduces risk, makes security teams’ lives easier by using automation wherever possible and empowers users to do their jobs as efficiently as possible.
Looking for more insights? Check out our Labs Team’s latest threat research and explore top-of-mind security vulnerabilities with our Red Team in this on-demand webinar.























