
The quantum threat isn’t theoretical—it’s operational.
Quantum computing is rapidly shifting from research to reality, forcing chief information security officers (CISOs) to rethink cryptography, risk management and long-term data protection.
In a previous post, I explained the quantum challenge. Recently, we explored why quantum readiness is not optional. Now, it’s time for action.
Preparing for the post-quantum era is critical to future-proofing and maintaining a competitive edge. This blog is a step-by-step guide for CISOs who wish to navigate these challenges and stay ahead of the curve effectively.
Why quantum changes the security game
Quantum computing represents a significant advancement in computational power, leveraging quantum bits (qubits) that can exist in multiple states simultaneously. This unique capability enables quantum computers to execute complex calculations at speeds far exceeding those of classical computers. Most notably, quantum computers have the potential to break many of the current public key algorithms and the protocols that depend on them, such as Transport Layer Security (TLS).
However, this transition is far from simple. It’s a complex, multi-year endeavor that demands substantial investment and sustained executive support. It requires more effort than preparing for Y2K, and failure could have dangerous consequences.
How to start your post-quantum journey
To address the quantum threat, researchers have developed post-quantum cryptographic algorithms designed to be secure even against quantum computing attacks. The National Institute of Standards and Technology (NIST) has finalized several post-quantum encryption standards, which are now available for use. Meanwhile, the European Union Agency for Cybersecurity (ENISA) has provided comprehensive guidance on PQC, outlining the five main algorithm families and recommending hybrid implementations and key mixing strategies to mitigate quantum threats even before full standardization is complete. The hybrid approach is also endorsed by the European Telecommunications Standards Institute (ETSI) and Google, which added support to hybrid schemes in Chrome.
Hybrid post-quantum cryptography (PQC) is widely recommended as a transitional strategy to safeguard data against both classical and quantum threats. This layered approach is explored further in our recent blog, “How to build resilience while padlocks still work.”
The core idea is to combine well-established classical algorithms, like RSA or ECDH, with newer PQC algorithms in a single cryptographic operation. This layered approach ensures that even if one algorithm is compromised, the other maintains the system’s integrity. The rationale behind hybrid schemes is twofold: first, post-quantum algorithms are still relatively new and lack the decades of scrutiny that classical cryptography has undergone. Second, transitioning entire infrastructures to PQC is a complex and risky endeavor. Hybrid deployments allow organizations to adopt PQC gradually while retaining the reliability of existing systems.
Governments are also mandating preparation. The U.S. Quantum Computing Cybersecurity Preparedness Act, signed into law in 2022, directs federal agencies to inventory their cryptographic systems and begin transitioning to quantum-resistant algorithms. This mandate underscores the urgency of the threat and sets a clear example for private-sector leaders: Quantum preparedness is not optional.
To become post-quantum ready, organizations should follow guidance from key cybersecurity authorities, such as the U.S. Department of Homeland Security (DHS), NIST, the National Security Agency (NSA) and Germany’s Federal Office for Information Security (BSI). These guidelines focus on creating a quantum-readiness roadmap.

Cryptographic agility as a guiding principle
Cryptographic agility (or crypto agility) refers to an organization’s ability to swiftly and efficiently adapt its cryptographic systems in response to emerging security threats. Organizations that adopt crypto agility are better equipped to handle unforeseen vulnerabilities and maintain overall cybersecurity resilience.
Agility is crucial for transitioning to post-quantum algorithms. It can help CISOs proactively manage risks and implement quantum-resistant algorithms as soon as they become available. It’s not just a technical necessity—it’s a strategic imperative.
Step 1: Map your cryptographic inventory
Cryptographic components are often deeply embedded in applications, network protocols and third-party integrations. Without a clear picture of all this, you can’t make informed decisions about what needs to be replaced or updated. Those decisions require a comprehensive inventory of cryptographic tools. Unfortunately, most organizations lack one.
Start by systematically identifying and cataloging all uses of cryptography in your environment. This inventory should include:
- Protocols (e.g., TLS, SSH, IPsec)
- Libraries (e.g., OpenSSL, BouncyCastle, Windows CryptoAPI)
- Certificates and keys (e.g., X.509 certificates, private keys, signing keys)
- Applications (both in-house and vendor-supplied software)
- Devices (e.g., hardware security modules, smart cards, embedded systems)
You’ll need to check the algorithms used, the key lengths configured, where the keys are stored and how they’re managed (including key lifespan and rotation policy).
Many cryptographic functions rely on third-party products and services. That introduces a critical dependency as your security is partially tied to your vendors’ roadmaps.
Identify the vendors you rely on for cryptographic operations (e.g., cloud providers and identity platforms). Request and review their PQC roadmaps, including timelines and the algorithms they plan to support. Most importantly, establish ongoing communication with them to receive updates as their cryptographic offerings evolve. If a vendor lacks a clear PQC strategy, consider ways to mitigate that risk.
Step 2: Conduct a risk assessment
With your cryptographic inventory in hand, the next step is to assess the risks tied to your current cryptographic implementations.
The assessment is vital for two main reasons:
- Prioritization of cryptographic updates. Once you understand the risks, you can prioritize your actions based on severity. Focus first on protecting your most sensitive data.
- Understanding harvest now, decrypt later (HNDL) risks: In the HNDL scenario, we assume that attackers may already have copies of your encrypted data and can decrypt it once powerful quantum computers become available. Updating your cryptography won’t reverse this, so it’s essential to understand the potential implications of such a data leak. Learn more about HNDL in “This message will self-decrypt in 5 years.“
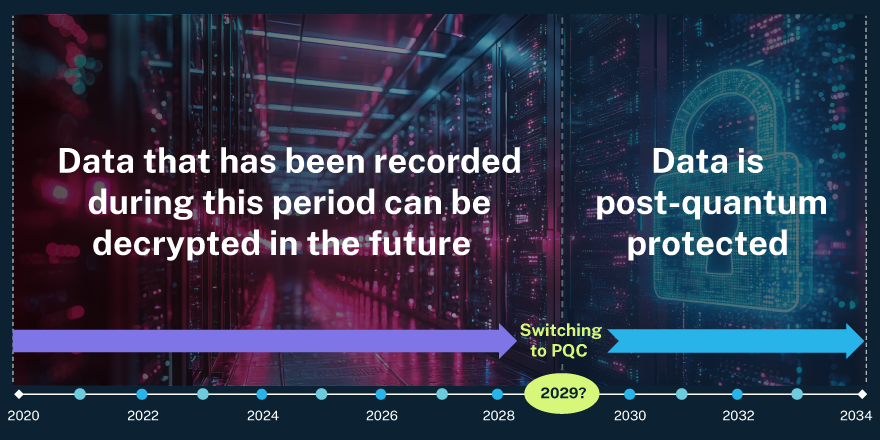
A comprehensive risk assessment should guide your transition strategy, ensuring that you address the most pressing vulnerabilities first. It should evaluate the sensitivity of data, the potential impact of a breach, and the likelihood of future decryption.
Step 3: Plan and execute your post-quantum cryptography transition plan
Once you’ve inventoried your cryptographic assets and assessed the associated risks, the next step is to evaluate and select appropriate PQC algorithms. This means understanding each algorithm’s strengths, limitations and performance characteristics and selecting those that best align with your organization’s operational needs, compliance requirements, and risk profile.
Go beyond theoretical security. Assess real-world implications, including:
- Performance impact. Many PQC algorithms require larger key sizes and more compute resources. Measure latency, bandwidth, and processing overhead—especially for constrained devices, real-time applications and high-throughput systems.
- Cost considerations. Larger compute, memory, and network requirements may lead to infrastructure upgrades, higher cloud costs or application refactoring. Conduct cost modeling early to identify areas where PQC adoption might drive significant expense.
- Integration complexity. Evaluate how well candidate algorithms integrate with your existing systems, libraries, protocols, and vendors. Some systems will need deep code changes or third-party updates to support PQC.
Selecting the right algorithms requires balancing cryptographic strength with operational feasibility, long-term maintainability, and total cost of ownership.
Once selected, develop a comprehensive transition plan with detailed roadmaps and timelines for updating systems, applications, and infrastructure. Prioritize the most critical assets that protect sensitive data or underpin essential services and sequence updates to minimize disruption.
Before rolling out PQC at scale, testing and validating its effectiveness is essential. Run simulations, conduct performance benchmarking, and perform security testing (including penetration testing) to ensure the new algorithms meet your requirements. Consider collaborating with experts and using industry testbeds to uncover implementation pitfalls early.
Go beyond algorithm replacement: Secure secrets and certificates
Simply replacing cryptographic algorithms isn’t enough. If an attacker has already exfiltrated your encrypted secrets, they may be able to decrypt them once quantum capabilities become available. Re-encryption and rotation must be part of your migration.
However, re-encryption can be incredibly challenging in legacy systems where secrets are hard-coded or tightly bound to app logic. Changing them could break functionality.
That’s why secrets rotation should be automated now. Automation reduces reliance on manual updates, lowers operational risk, and ensures that captured secrets are obsolete by the time a quantum adversary could exploit them. These practices can help prepare for a quantum future and enhance overall security posture in traditional threat environments.
Secrets rotation is particularly critical in the context of digital certificates. As certificate lifespans shrink, driven by compliance mandates and security best practices, manual certificate management becomes unsustainable. CISOs must champion the automation of certificate lifecycle management—including issuance, renewal, rotation, revocation, and auditing.
To further reduce risk, organizations should shift away from long-lived credentials and toward short-lived, just-in-time (JIT) access, such as ephemeral tokens, single-use API keys, or dynamically generated session credentials. These secrets can help minimize the attack surface and render intercepted credentials effectively useless within minutes or even seconds.
This approach aligns with a zero standing privileges (ZSP) model, where no user or system has permanent access. Instead, privileges are granted only when needed and revoked immediately after use. Implementing ZSP reduces the blast radius of any breach and ensures that your organization’s exposure remains minimal, even in the face of advanced threats.
9 must-do actions for post-quantum readiness
The quantum era is no longer a distant future. Here are the nine actions to help you prepare:
- Start now, not later. Quantum threats may seem years away, but risks such as HNDL are already present. Preparation takes time, and regulators are starting to require it.
- Inventory everything. You can’t protect what you don’t know. A comprehensive cryptographic inventory is the first and most critical step toward quantum readiness.
- Prioritize based on risk. Not all cryptographic assets are equal. Focus on high-value, long-lifespan data and systems first.
- Follow trusted guidance. Use frameworks and roadmaps from NIST, DHS, NSA, and BSI. Consult experts throughout this process.
- Find the right PQC algorithms. Not all PQC algorithms are created equal. They vary in speed, resource usage, and integration effort. Choose what fits your security goals—and your operational and business constraints—not just what looks good on paper.
- Automate certificate and secrets management. Manual management is no longer viable. Automate issuance, renewal, and rotation to help prevent outages, reduce the operational risk of stale or compromised credentials, and future-proof your infrastructure as PQC algorithms evolve.
- Embrace JIT and ZSP. Move away from long-lived, static credentials. Use ephemeral, short-lived tokens and adopt ZSP to limit access by default.
- Build for cryptographic agility. Don’t get stuck with one algorithm. Build systems that can adapt and respond quickly to evolving threats and new standards.
- Engage your vendors. Your security is only as strong as your weakest vendor. Collaborate with suppliers and partners to ensure their post-quantum cryptographic strategies align with yours.
The post-quantum transition is complex, but it is manageable. With a proactive mindset, a structured approach and executive support, CISOs can help position their organizations for a safer transition into the quantum future.
Dr. Erez Waisbard is a principal technology researcher at CyberArk.






















