More and more organizations are getting on board with infrastructure as a service and the hybrid cloud and it looks like that trend is only accelerating this year. As hybrid cloud environments become more prevalent, it’s time to look back at the evolution of cloud computing – and, more importantly, how to secure these dynamic environments.
In the early 2000s, Amazon, an e-commerce company going through rapid growth, needed its IT environment to be capable of handling the seasonal and massive fluctuating demands on its IT resources. For most e-commerce companies, consumer demand typically spikes in November and December. Amazon took it upon itself to create a solution to address its dynamic demand and resource needs; that solution was Amazon Web Services (AWS).
Following its launch in 2006, AWS outpaced Amazon’s operating income and tripled in revenue over the next two years. Thus, the public cloud computing market was born. Following Amazon, Google launched the Google App Engine in 2008 – which became Google Cloud Platform in 2008 – and Microsoft Azure launched in 2010.
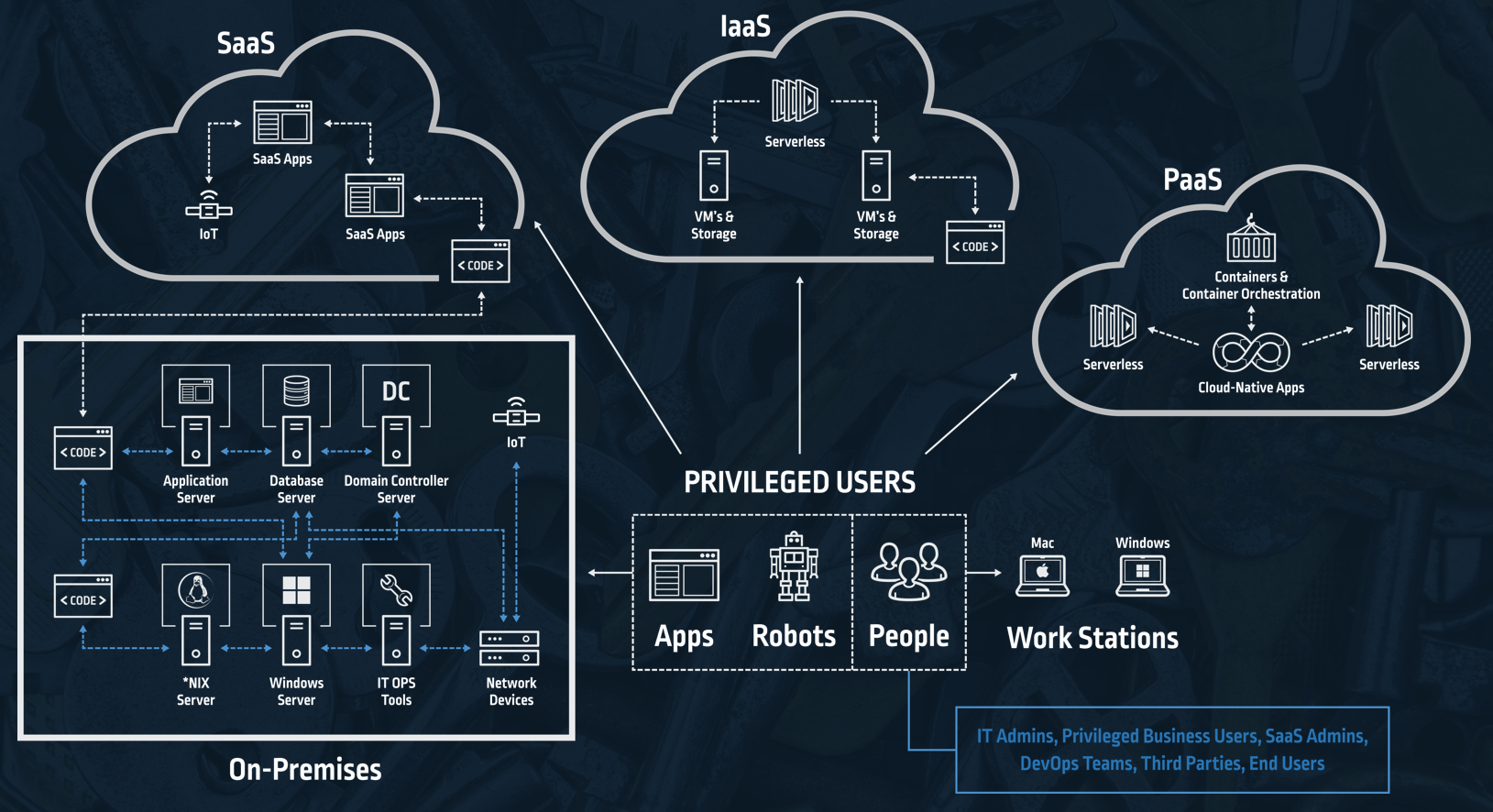
Oftentimes independent groups or business units within an organization choose different public cloud providers to meet their particular requirements including the need for flexibility to support multiple business lines and geographies. Consequently, organizations use services hosted across multiple public cloud, private cloud and on-premises infrastructure, resulting in hybrid environments.
According to the RightScale 2019 State of the Cloud Report, over half of respondents – 54% — have a hybrid cloud strategy. Furthermore, organizations leverage almost five clouds on average. Beyond this, companies leverage Software as a Service (SaaS) applications and Platform as a Service offerings all of which need to be accessed by multiple types of privileged users, expanding the landscape that needs to be secured and increasing the pressure on security teams.
Security in public clouds is a shared responsibility between the public cloud vendor and the organization. Cloud vendors are committed to the security of the cloud infrastructure, including the compute, storage and networking resources, as well as the physical infrastructure. However, the application owner is responsible for protecting the applications, data, OS and other enterprise infrastructure, as well as other assets running in the cloud. Application owners can’t afford to forget that the security of these elements in the cloud is in their hands.
To protect the cloud environment, start by ensuring that the right users – and only the right users can access only the applications, the cloud infrastructures, the cloud platforms and only when they need them. The same is true for hybrid cloud environments – except that those same security measures that keep the cloud safe need to work for both and on-premises environments without slowing anyone down.
When it comes to securing hybrid environments, enforcing the same privileged access security polices across the entire organization, regardless of the infrastructure environment, platform or SaaS application, enhances adoption by easing security policy management. In other words, the same privileged access management (PAM) policies and just-in-time access need to be equally enforced throughout every public, private and on-premises environment for every privileged user. CyberArk delivers solutions that enforce consistent enterprise-wide security policies across cloud and hybrid environments.
Want to learn more about how to secure the cloud journey? Learn how CyberArk protects cloud workloads or watch a webinar on best practices for securing cloud based applications and infrastructure.