
If one thing’s for certain, it’s that public cloud adoption is not going away or slowing down. Today, 94 percent of global organizations use cloud services. Sixty-one percent of public cloud users leverage Amazon Web Services (AWS,) 52 percent use Azure and 19 percent use Google Cloud – and these numbers are climbing fast. Fueled by top-down digital transformation initiatives and bottom-up pushes to streamline development processes, even heavily regulated organizations like financial services and healthcare are accelerating their adoption cycles.
Frequently, these cloud initiatives are well underway before security gets involved. But, cloud architecture and DevOps teams often lack the expertise to adequately address the risks associated with privileged access, and they often do not make security a priority given their mandate to bring new digital services to market quickly. That’s why it’s critical for security teams to collaborate in integrating security before poor practices become entrenched. (We cover this in-depth in the CISO View: Protecting Privileged Access in DevOps and Cloud Environments).
We recently hosted a webinar on best practices for securing commercial software-as-a-service (SaaS) applications, cloud infrastructure, and custom apps deployed in the cloud, which we illustrated through a series of real-world CyberArk customer use cases. Following are highlights. Tune in to the on-demand webinar for full technical details and an informative Q&A.
The Power of Privilege in the Cloud
While organizations’ infrastructures are increasingly becoming cloud-based, some things remain the same. Attackers still seek the path of least resistance and privileged access management (PAM) is still vital to securing the attack path.
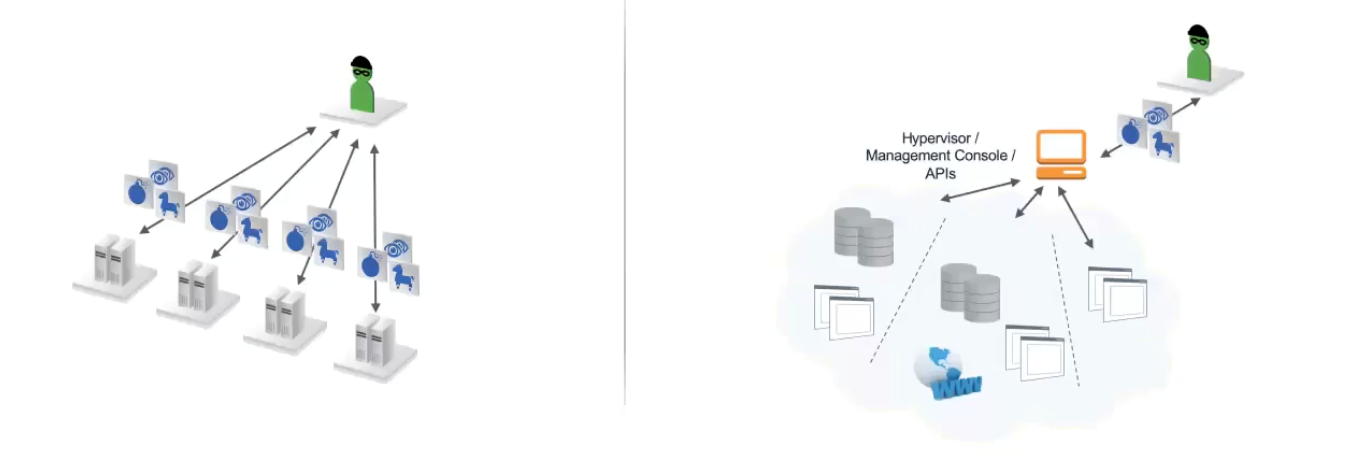
The Original Way: On-Premises Cyber Attack
During a traditional on-premises breach, a cyber attacker looks for ways to compromise a user, which often starts with an attack on the endpoint. For instance, an attacker could start with phishing (who doesn’t love a great cat video?!) to get their hands on privileged credentials. Once the stolen privileged credentials are in hand, they could move laterally through the network, escalating privileges and work their way up to then owning a domain.
The New Way: Cloud Cyber Attack
In modern cloud environments, an attacker can save a number of steps by compromising one privileged user and then leverage this access to compromise, for example, a cloud management console. By hijacking these types of privileged credentials, attackers can shut down the cloud environment.
While it’s impossible to say whether the cloud is more or less secure than on-premises, misconfigurations across these open, more centralized environments can ripple in an exponential way that you don’t see in traditional deployments. So, securing privilege in the cloud has become an enterprise imperative.
Identifying Quick Wins for Extending Privileged Access Management into the Cloud: Three Real-World CyberArk Use Cases
Use Case 1: Securing Root and Privileged Access into Cloud Management Consoles
The Situation: A global financial services institution’s cloud team deployed to AWS and Azure six months ahead of any security oversight. By the time the security team received the request to secure the new environment, workflows had already been established, making it difficult to change anything. The good news, however, was that the cloud architecture team had placed multi-factor authentication (MFA) in front of their AWS and Azure root accounts, an important security best practice.
In this multi-cloud AWS and Azure environment, every single admin member on the cloud team had their own AWS identity and access management (IAM) accounts, with mapped roles for administrative access. This translated to large number of both roles and accounts that they needed to manage. For Microsoft Azure, they were using Azure AD Connect to integrate with their on-premises Active Directory. Non-human application access into the cloud was not being managed at all.
The Challenge: The biggest challenge the security team faced was securing the cloud root accounts for AWS and Azure. In on-premises environments, securing these accounts with CyberArk would involve MFA, password rotation and enforcement. But, in cloud environments, MFA is already present and rotation happens using the UI. So, the security team initially considered two choices for automatic rotation:
- Use CyberArk to control and monitor access to the root account, then enable manual rotation policies and external MFA.
- Manage and rotate passwords within CyberArk and add customizations when the cloud provider updates the UI.
The Solution: While both of the above approaches work, this organization chose a more pragmatic approach. They used CyberArk Privileged Access Security Solution to vault their root accounts (20 total) and leveraged CyberArk as a point of access and audit control. Then they used the CyberArk solution to isolate and monitor user connections and evaluate risk. By vaulting the root account, using the native cloud MFA and implementing monthly manual rotation, the security team freed up valuable time to focus on implementing additional controls around privileged roles.
Use Case 2: Extending Password Vaulting and Rotation to Integrated Automation and Security Tools
The Situation: Application credentials typically outnumber human accounts, so controlling, managing and auditing non-human privileged access for these applications is no small feat. Two of our telecommunications customers – one a global enterprise, the other a regional provider – took a similar approach to securing the application credentials of their cloud-native apps.
Both of these organizations leveraged native secret stores provided by their cloud, DevOps and Robotic Process Automation (RPA) vendors. This led to a heavily fragmented approach and “islands of security.” When the security team was asked to help secure these applications, the main questions were: Where exactly do these secrets live, and who is responsible for rotating them?
The good news is that both organizations were already using the CyberArk solution for their J2EE application servers. Additionally, they were using hash authentication, a powerful form of application authentication that validates whether or not an application has changed based on the hash of the entire stack or certain classes within the stack.
Challenge: Both organizations were seeking centralization, but the development teams – laser focused on high velocity, code sharing, ad-hoc tooling and full-on automation – were not interested. The new cloud security project didn’t just have to solve the problem, but most importantly, the security team had to get the developers on board.
Solution: When you have so many applications, focus becomes paramount. These organizations prioritized removing application secrets for RPA for Phase 1. This step had the advantage of cross-team visibility, adoption and the ability to achieve quick wins – useful for demonstrating benefits to developers. From there, they began the process of migrating to a shared services security model, with the end goal being that non-security teams would provide internal financing for cybersecurity projects. This had the added effect of creating cross-functional teams. By establishing cross-functional teams, they brought DevOps and security teams into alignment and fostered collaboration for stronger overall security.
Use Case 3: Scaling CyberArk Deployments in the Cloud
Situation: Brand loyalty used to be huge for cloud. This has shifted, and today, multi-cloud environments are the name of the game. One technology provider we worked with had a tri-cloud environment comprising AWS, Azure and a private cloud. Cloud usage had skyrocketed in a short period of time, leading to a huge number of accounts and instance sprawl.
Challenge: The company was onboarding the credentials for new EC2 instances and Azure VMs to CyberArk using a manual and time-consuming process. In fact, each person requesting an instance had to fill out a written form. Automation was critical – and this need was compounded by the fact that their on-premises assets were soon going away. The team turned their focus towards streamlining this process significantly.
Solution: The company leveraged the CyberArk REST API to onboard new cloud artifacts and trigger rotation and began using the same API to perform de-provisioning. As part of their privileged access management journey, they are currently evaluating additional automation and intelligence, including the auto-onboarding AWS Lambda function and the CyberArk solution’s ability to detect and onboard newly created shadow access keys and IAM accounts.
Interested in learning more about how CyberArk can help you secure cloud-based applications and cloud-based infrastructure and move your digital business forward fearlessly? Check out the full on-demand webinar.























