
Identity Threat Detection and Response (ITDR) is one of many aspects of an effective identity security program. Yet despite what some detection and response-focused vendors may argue, ITDR is not a silver-bullet solution to prevent identity-centric attacks. Such a thing doesn’t exist.
In fact, modern data breaches, industry analyst perspectives and compliance requirements make it crystal clear that organizations need more than ITDR to build an identity security program.
Today’s Attack Methods Circumvent ITDR Solutions
Major recent breaches highlight the value of proactive identity risk reduction. New identity-centric attack methods that bypass ITDR and other reactive controls are emerging. Agents on endpoints collect data for many ITDR systems, but without them, the systems cannot detect or respond to activity.
Take, for example, the September 2023 MGM breach. The Scattered Spider ransomware group behind the attack relied on stolen credentials but did not follow traditional methods of deploying malware on employee endpoints. Instead, the attackers used generative AI to voice phish (or ‘vish’) employees and help desk teams to provide their credentials and reset multi-factor authentication (MFA) settings.
Even with ITDR agents deployed on all endpoints, Scattered Spider could have still gained access. The attack specifically circumvented the endpoint, relying on social engineering in a medium (phone calls) where detection-focused security tools would not have visibility or context.
The same was the case with the October 2023 Okta Breach, where attackers first compromised the personal laptop of an Okta employee, knowing it was likely outside the estate covered by ITDR and other detection-focused technology. The attackers then found and used credentials for a corporate privileged service account in the password manager of the employee’s personal account.
This breach also illustrates the need for ITDR as part of the identity fabric. On the employee’s home laptop, the attackers found credentials for a privileged service account in the employee’s personal password manager. With a mature, integrated program spanning PAM and ITDR, the organization could not only have prevented the employee from seeing (and saving) the service account credentials but also detected anomalous or unauthorized use of the credentials and terminated the session.
To defend against modern attack methods, organizations need both proactive and reactive controls.
ITDR, Identity Security and Zero Trust
Take, for example, the core mantra of the Zero Trust philosophy – “Never Trust, Always Verify.” Organizations that rely on ITDR alone set themselves up to fail in both regards. ITDR can neither proactively reduce the attack surface (never trust) nor authenticate user connections (always verify).
Agent-based ITDR solutions also cannot often detect behavior beyond an identity’s endpoint – such as in web browser sessions to SaaS apps or a CLI session to an elastic cloud workload. Essentially, ITDR systems require integrations by default to detect or respond to attacks.
However – ITDR can help progress Zero Trust initiatives as part of a broader identity fabric. Through integration with privileged access management (PAM) and identity governance and administration (IGA) disciplines, ITDR adds a layer of defense-in-depth control to help organizations adopt the ‘assume breach’ mindset. ITDR also adds value to access management systems, authenticating end users in alignment with Zero Trust principles, helping organizations detect anomalous or risky activity – and denying access. ITDR capabilities from PAM solutions can also help detect privilege misuse, credential theft, and attempts to bypass PAM controls and workflows – without any agents.
In effect, ITDR can add value to Zero Trust initiatives through tight integration with existing identity security investments.
Analyst Perspectives: ITDR and the Identity Fabric
Industry analysts have long agreed on the need to secure identities with both proactive and reactive controls. In particular, many analysts cite the imperative for an interconnected identity fabric architecture that blends modular technologies to consistently enforce risk-aware, adaptive and resilient access controls – for both human and machine identities.
Operational efficiency is an essential element of the identity fabric concept. Analysts emphasize security teams should reduce complexity by focusing on IAM disciplines, not tools, and aiming to improve the composability of those disciplines. Mature ITDR disciplines can help realize this concept via data exchange with other disciplines like access management, PAM and IGA.
Of note, leading analysts emphasize identity fabrics are not synonymous with any single vendor’s suite of products; instead, the concept describes a proposed architecture of people, processes and technologies from different vendors that collectively provide defense-in-depth protection for all human and machine identities.
Compliance and Cyber Insurance Perspectives
Auditors and cyber insurers also offer clear recommendations to proactively reduce the identity attack surface. For example, compliance with frameworks like PCI DSS and AICPA SOC II requires adherence to proactive requirements like restricting access to sensitive systems and authenticating all connections.
The NIST Cybersecurity Framework is particularly clear in its guidance, specifying five core elements: Identify, protect, detect, respond and recover. Access control is the very first category of controls in NIST’s ‘protect’ phase, and NIST views proactive access control as foundational. The framework provides clear guidance to ensure:
- “PR.AC-1: Identities and credentials are managed for authorized devices and users”
- “PR.AC-3: Remote access is managed”
- “PR.AC-4: Access permissions are managed, incorporating the principles of least privilege and separation of duties”
Cyber insurance underwriters, who have direct ‘skin in the game’ when keeping clients secure, also recognize that phishing, ransomware and software supply chain attacks all rely on compromised identities and credentials. Not surprisingly, underwriters look for proof an organization is both proactively and reactively reducing the risk of identity compromise.
Examples of common cyber insurance requirements include:
- Taking endpoint security past endpoint detection and response (EDR/XDR) by proactively removing local admin credentials from employee workstations and servers.
- Enforcing MFA to verify use of administrative privileges.
- Securely managing and rotating credentials for highly privileged accounts and machine identities like service accounts.
- Isolating usage of privileged accounts to prevent lateral movement.
- Extending privileged access management controls to third-party vendors.
Beware of Wolves in Sheep’s Clothing: ITDR Vendor Claims to Watch Out For
Some ITDR vendors continue to market their capabilities as superior to PAM, access management and IGA, despite the consensus recommendation for both proactive and reactive identity security controls.
In particular, certain ITDR-focused vendors have communicated that PAM solutions are insufficient – even releasing misleading claims, like the ones illustrated in the “ITDR Vendor Claim” column in the chart below (yes, they are actual vendor claims, which we’ve reworded, in an effort not to directly call out the vendor). For clarity, we’ve includedan analysis of where each discipline adds value to an identity security program in the right column (“Identity Security Reality”).
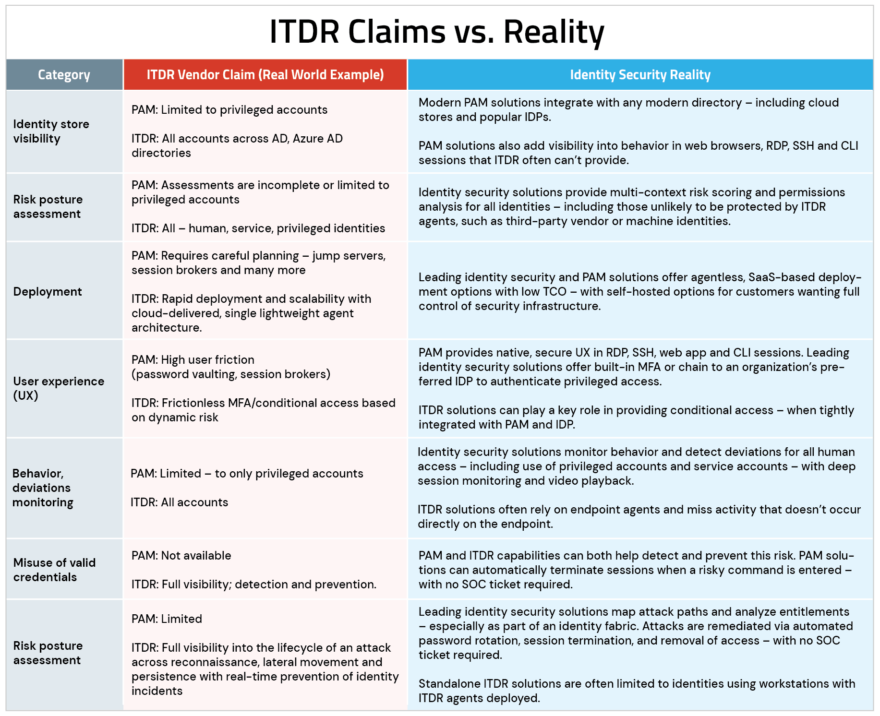
CyberArk believes security is a team game, which is why we aren’t singling out the vendor behind the claims in the table’s left column. But you should evaluate baseless claims that any one vendor can ‘do it all’ with caution. Understand that to truly reduce risk, your identity security program needs both proactive and reactive controls.
TL;DR: You Need More Than ITDR to Secure Your Organization’s Identities
ITDR does not replace widely recommended security disciplines like access management, PAM and IGA. Rather, ITDR can add value and help make Zero Trust a reality through tight integration with these disciplines in an identity fabric model.
Want to learn more about the connection between identity security and Zero Trust? Check out our whitepaper on Guiding Your Leadership Team Through the Zero Trust Mindset.
Sam Flaster is a director of product marketing at CyberArk.























