
Meeting regulatory compliance requirements is one of global organizations’ top challenges as they scale cloud deployments and embrace multi-cloud strategies to drive business efficiencies. The burgeoning number of identities within public cloud environments is a major contributor to this massive compliance conundrum. Every single human and machine identity in a cloud environment can be configured with thousands of different permissions to access workloads containing sensitive information — from intellectual property to customer data.
Excessive Permissions Create Cloud Security and Compliance Risks
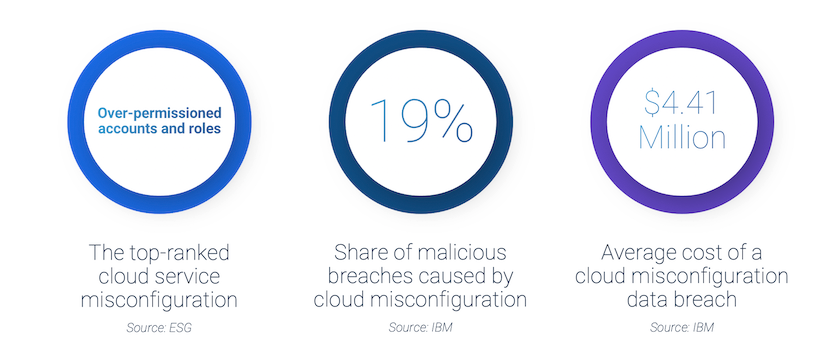
Excessive, unused and misconfigured cloud permissions expose organizations to the risk of a data breach, which costs organizations an average of $3.86 million dollars, according to Ponemon Institute and IBM research. And according to the same research, cloud-specific breaches cost even more at $4.41 million on average. Compliance violations and financial penalties are becoming an even greater part of overall breach cost, thanks to tightening cybersecurity regulations and oversight around the world.
Seven Regulatory Frameworks that Require Least Privilege
An attacker controlling an identity with excessive permissions can steal or reach sensitive information easily, often without detection. Because of this — and regardless of your organization’s industry or geographic location — one thing regulatory bodies, industry frameworks and public cloud service providers all emphasize is the need for least privilege enforcement. Working to continuously ensure that all identities have the minimum permissions necessary to perform their duties is a fundamental best practice for reducing risk exposure and is aligned with a Zero Trust security approach.
Here’s a look at seven select frameworks that require least privilege:
1. SWIFT Customer Security Controls Framework. Financial institutions in the Society of Worldwide Interbank Financial Telecommunication (SWIFT) must routinely comply with Mandatory Security Control #5, “Logical Access Controls.” SWIFT members must self-attest that they “enforce the security principles of need-to-know access, least privilege and segregation of duties for operator accounts.”
2. Payment Card Industry Data Security Standard (PCI DSS). Per PCI DSS Requirement 7, businesses managing cardholder data must “ensure critical data can only be accessed by authorized personnel, systems and processes must be in place to limit access based on need to know and according to job responsibilities.” The regulation continues, “Need to know is when access rights are granted to only the least amount of data and privileges needed to perform a job.”
3. National Institute of Standards and Technology (NIST) Framework for Improving Critical Infrastructure Cybersecurity. NIST states in PR.AC-4: “Access permissions and authorizations [should be] managed, incorporating the principles of least privilege and separation of duties.”
4. American Institute of Certified Public Accountants’ SOC for Cybersecurity. Organizations developing software applications and pursuing SOC I or SOC II certifications must complete attestations of their compliance with AICPA Trust Services Criteria. SOC I or SOC II certification requires “the entity authorizes, modifies, or removes access to data, software, functions, and other protected information assets based on roles, responsibilities, or the system design and changes, giving consideration to the concepts of least privilege and segregation of duties, to meet the entity’s objectives.”
5. Health Insurance Portability and Accountability Act (HIPAA). Key HIPAA components such as the Privacy Rule and Security Rule place firm restrictions on unnecessary access to protected health information (PHI) and limit all access to the “minimum necessary” standard. For example, the HIPAA Privacy Rule states that covered entities “must develop and implement policies and procedures that restrict access and uses of protected health information based on the specific roles of the members of their workforce.”
6. General Data Protection Regulation (GDPR). The European Union’s GDPR Article 25 stipulates businesses must proactively implement “Technical and organizational measures for ensuring that, by default, only personal data which are necessary for each specific purpose… are processed.” In other words, organizations must proactively restrict unnecessary access to personal data to comply with GDPR.
7. California Consumer Privacy Act (CCPA). The CCPA specifies in Section 11 that “Any consumer whose nonencrypted or nonredacted personal information… is subject to an unauthorized access and exfiltration, theft, or disclosure as a result of the business’s violation of the duty to implement and maintain reasonable security procedures and practices… to protect the personal information may institute a civil action…” Under CCPA, penalties are variable and businesses who expose large amounts of consumer data through insufficient access controls could face significant penalties.
A number of security research frameworks, including the MITRE ATT&CK Framework and Cloud Security Alliance Cloud Controls Matrix, echo similar least privilege guidance, as do all of the leading cloud providers.
Despite widespread consensus on the importance of least privilege, effectively managing permissions remains a significant challenge for many organizations due to rampant misconfigurations and common provisioning practices that assign default permissions based on department or role. The result? Many identities have permissions that they do not need or use, creating significant security and compliance risk.
To make cloud permissions management actually manageable, many security and Identity and Access Management (IAM) teams are turning to AI-powered solutions that can automatically detect and clean up misconfigured and unused cloud permissions, while applying least privilege controls consistently across their cloud estates.
In the words of former U.S. Deputy Attorney General Paul McNulty, “If you think compliance is expensive, try non-compliance.” Don’t wait for an audit — or a costly breach — to identify your cloud compliance gaps. Give our SaaS-based CyberArk Cloud Entitlements Manager a 30-day free trial and assessment to analyze and remediate excessive access in your cloud environments — with no infrastructure required. See how you can meet regulatory mandates around least privilege access while safely scaling your business in the cloud.





















