
Many major cybersecurity breaches can be traced back to the tiniest flaw. But as zero-day exploitations continue to make headlines and new vulnerabilities enter the National Vulnerability Database (NVD) almost daily, it’s often hard for security teams to seal the cracks and fix the bugs fast enough (not to mention address hidden issues they don’t even know about).
It’s a lot like owning an old house. Something always seems to be breaking or leaking, and even the most industrious do-it-yourselfer can quickly become overwhelmed by their growing to-do lists. With limited time, resources or know-how, homeowners tend to focus on the “big stuff” — replacing the washing machine that suddenly dies or calling emergency pest services after a mouse skitters across the kitchen floor.
But putting off or ignoring tiny issues, like the ones in this house, can lead to major headaches down the road … and sometimes, much sooner than you’d expect.
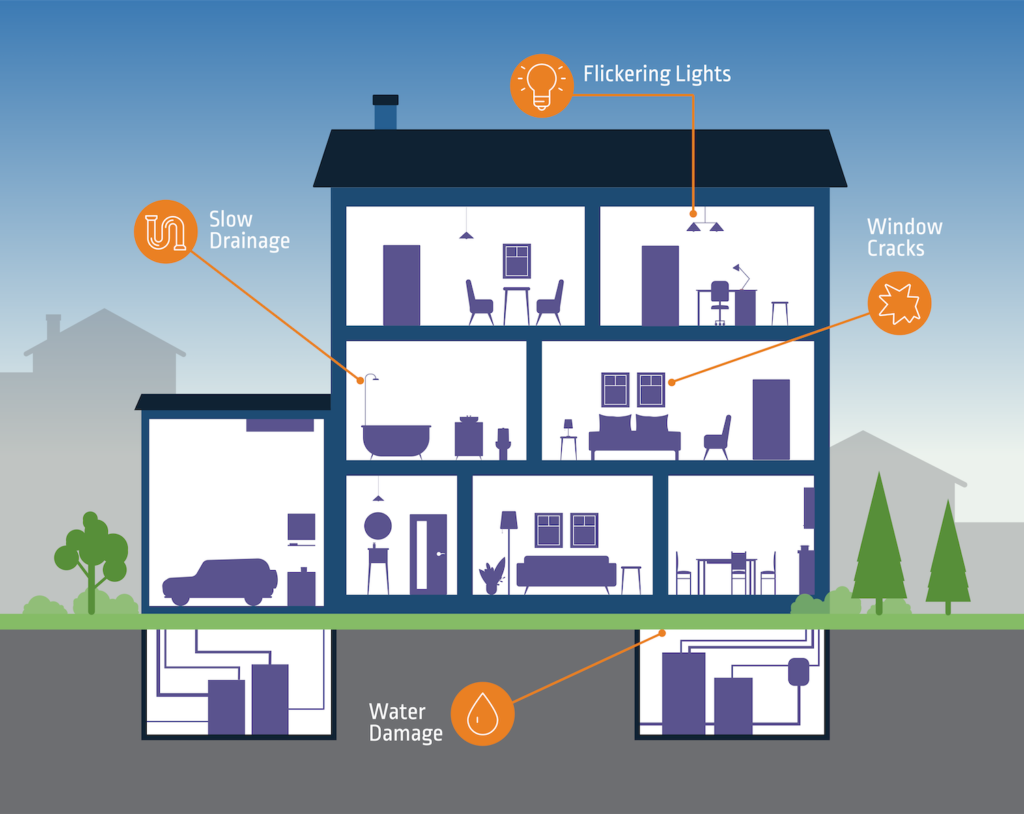
Window Cracks
You think your kids were just playing baseball and accidentally broke a window. Little do you know there’s an invisible structural shift taking place underground that’s creating undue pressure on all your windows and threatening every glass entry point into the house.
Malicious code execution can be a lot like that shift in pressure change. For example, a minor Patch Tuesday update quickly morphed into a critical code execution and privilege escalation vulnerability within the Windows Print Spooler service. Today, there are several known variants of this security issue, collectively known as “PrintNightmare.” Once these vulnerabilities are exploited, the “glass” can break when SYSTEM is obtained.
Recent reports indicate ransomware attackers are riding the PrintNightmare wave, taking advantage of unpatched networks to compromise and decrypt files and demand ransom payments.
Flickering Lights
Your lights just flickered suddenly. But you shrug it off, figuring you just haven’t changed the bulbs in a while. What’s actually happening is far more serious: Your home’s wiring is inadequate, and you’ll soon be facing a hefty bill from your electrician.
These flickering lights are akin to HiveNightmare, also known as SeriousSAM, a local privilege elevation vulnerability that allows an attacker to access critical secrets from the shadow copy of the Windows registry. While you may just see “flickering lights,” from time to time, small stealthy changes are happening in your fuse box — which can eventually lead to an overload or meltdown.
An attacker who successfully exploited this zero-day vulnerability could “run arbitrary code with SYSTEM privileges” and then “install programs; view, change or delete data; or create new accounts with full user rights,” according to Microsoft. The company warns that it’s not enough to simply patch systems; instead, all file shadow copies must be deleted as well.
Slow Drainage
What you think is just a pesky shower clog is really a major issue across your entire main sewer line. Yet you pour in some drain cleaner and get back to your day.
It’s like the unknown vulnerability within Kaseya’s IT management software that was first exploited to ignite the far-reaching REvil ransomware supply chain attacks. Attackers reportedly compromised Kaseya’s Virtual System Administrator (VSA) solution, which is used to remotely monitor and manage endpoints and servers. With control over SaaS and on-premises Kaseya VSA servers — along with other MSP-managed on-premises servers — the threat actors pushed a phony software update containing the ransomware to ultimately infect at least 1,500 MSP businesses and their downstream customers.
Water Damage
You notice something that looks like water damage in your basement, but the area is completely dry. You can’t seem to find the source of the leak. What you don’t realize is that a termite colony has been thriving under your floorboards, behind your walls and in your basement … for several years.
Cloud Hopper, a multi-year cyber invasion that targeted the world’s largest technology and cloud service providers and their customers, began by compromising one single endpoint. For one victim organization, the attack cycle continued for at least five years as attackers leveraged automation and privileges of trusted services to distribute malware and worm deeper into systems — without raising red flags.
Protect Your House with Defense-In-Depth Starting at the Endpoint
Maintaining a safe and secure property is an ongoing labor of love and as any seasoned homeowner understands, it requires a whole toolbox and reliable network of experts to help with the heavy lifting.
The same goes for cybersecurity: Protecting your organization is an ongoing effort, not a box to check off, and the most effective approach involves multiple tools working together. Comprehensive endpoint security strategies often comprise endpoint detection and response (EDR), next-generation anti-virus (NGAV), Privileged Access Management, and application and operating system patching tools and best practices.
Cyber attackers look for tiny cracks — often on the endpoint — to penetrate your IT estate and gain an initial foothold. From there, they cleverly perform reconnaissance and avoid detection to either steal data, take down critical applications and infrastructure — or pursue whatever their end game is. What can start small as a somewhat insignificant security event can result in a major breach that brings the business to its knees. These endpoint-originated attacks can disrupt your business, damage your company’s reputation and lead to steep regulatory fines. Yet just like homeowners who put off seemingly “minor” issues, many organizations underestimate their endpoint security risks, leaving the door wide open for attackers. By maximizing your endpoint security posture with a layered security approach, your organization can reduce risk and uncertainty and protect your digital “house.
Interested in learning more? Defense-in-depth solutions such as CyberArk Endpoint Privilege Manager enforce privilege escalation and credential theft controls that help prevent attackers from gaining administrative access in your environment and getting their hands on your most valuable assets. Meanwhile, end-users can get temporary, on-demand access to the privileged resources they need without overburdening the IT help desk. This can also help protect against zero-day exploits and ransomware by restricting or blocking suspicious applications. And if an endpoint device hasn’t been adequately patched against a vulnerability like PrintNightmare, policies are dynamically implemented to stop the vulnerable software from executing. Learn more about CyberArk Endpoint Privilege Manager or request a free trial today.























