
Around the globe, the rapid, unplanned shift to remote work has tested CISOs’ ability to get employees up and running quickly and demonstrate decisive leadership in the face of uncertainty.
To support workforce productivity and reduce the strain on IT support teams (who are bombarded with calls from employees unaccustomed to remote work), many organizations choose convenience over security out of a perceived necessity.
This is perhaps most evident in the initial lax approach to endpoint security. For example, BYOD use has skyrocketed – regardless of company policy. Further, in many cases, IT and security teams are granting full local admin rights to employee devices, enabling workers to use various programs, download applications and software, connect and install devices and access corporate systems and information with ease.
While local admin rights promote self-sufficiency, they can also introduce serious risk. Employees trying to navigate their day-to-day tasks from home are downloading unsanctioned applications and unlicensed software en masse without security oversight.
And, as remote users tend to use the same device for work and personal use, they could easily (and unknowingly) execute malicious software as they browse online news sites, launch apps for virtual school sessions or download games to pass the time.
Even worse, with powerful local admin rights at their disposal, cyber attackers or remote employees with malicious intent can do anything from modifying system configurations to changing powerful administrative accounts.
Remote Workers’ Endpoint Devices Are Under Attack. Privileged Credentials Are the Target.
Even without local admin rights, employee devices are a prime target. Attackers know that, out of convenience, people often save passwords in their devices’ credential stores (e.g., Chrome, Firefox and Chromium), chat applications (e.g., Pidgin and Skype), email (e.g., Outlook and Gmail) and even system admin tools (e.g., FileZilla, OpenSSH, VNC and WinSCP).
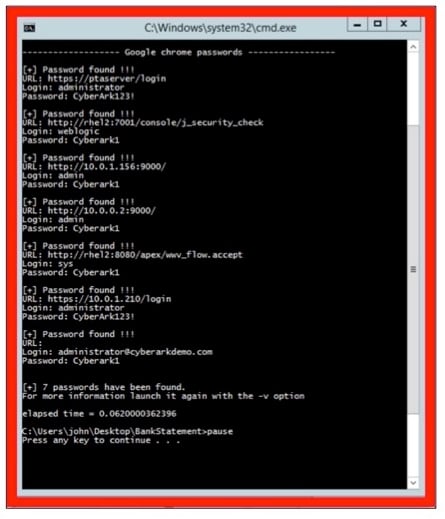
Using credential harvesting malware like LaZagne, attackers can retrieve passwords for personal web accounts and sensitive company assets alike. After harvesting “low-hanging” passwords quickly and with minimal effort, attackers then work to find privileged credentials and escalate access rights. Once the device is compromised, they can leverage the company’s VPN connection to move laterally, continue to escalate privileges, extend to other parts of the corporate network, and gain access to critical assets and information.
Here’s a look at how easily this can happen:
Employee “John” started working from home in March following a shelter in place order. He was given local admin rights on his laptop that allow him to do things like link his home printer to his device without help desk assistance. This also gives him the freedom to conduct personal online activities without connecting to the VPN.
- John logs into his personal email account and opens a message from his bank with his monthly statement. As usual, he clicks “View Statement” and downloads the PDF file.
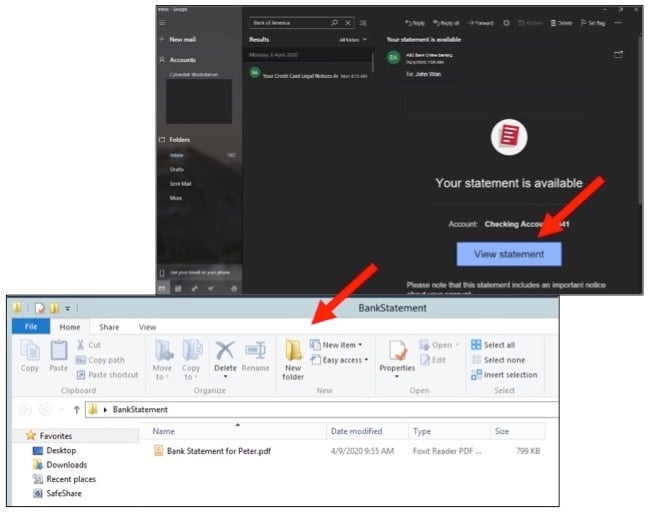
- He tries to open the PDF and is prompted to enter a password. Assuming his bank has amped up security measures during this time of uncertainty, he types in his banking password then clicks on the link to open his statement.

- After clicking the link, John is either directed to a corrupted attachment or an invalid web link. As part of this “drive-by download” attack, John has unintentionally downloaded LaZagne. The malware runs behind the scenes to harvest credentials saved in John’s web browser and applications (including credentials to corporate applications and systems). The malware sends these credentials out to the remote attacker or Command and Control server. Here’s what this looks like via a Windows command prompt. But, remember, John has no idea that this just happened.
Pervasive local admin rights, distracted or unaware remote employees and unprotected credentials have created the perfect storm for endpoint attacks. In recent weeks, researchers have recorded a spike in threats tied to the current global situation—from “CoronaVirus” ransomware distributed alongside the “KPot” infostealer, to “Emotet” malware disguised as infection-prevention tip emails, to an APT group spreading a custom remote access trojan (RAT) that takes screenshots of the device, develops a list of files and directories and downloads files – and more.
Enforcing Least Privilege, Credential Theft Protection and App Control Across Remote Workstations
We’re entering the next phase of what many believe will be a permanent shift in the way people work – a new normal. Enhanced situational awareness will quickly advance to risk mitigation within a matter of weeks. Critical steps in this “action” phase will be removing local admin rights and enforcing the principle of least privilege (PoLP) – that a user should only have the minimum level of access they need to do their job – to contain malware, ransomware and other threats on the endpoint.
This is why solutions like CyberArk Endpoint Privilege Manager are so crucial to an overall privileged access management (PAM) strategy. Organizations must strike the right balance between security, end user and help desk productivity. By adding a critical protection layer to strengthen existing endpoint security tools like DLP and antivirus/NGAV, CyberArk enables companies to block and contain attacks early in their lifecycle and help prevent data breaches.
Let’s take a look at the above drive-by download attack example again – but this time with CyberArk Endpoint Privilege Manager deployed.
- With CyberArk, John must login to his device as a standard business user – without access to local admin rights. He then follows steps 1 and 2 above. CyberArk’s credential theft protection capability blocks unauthorized applications and processes from accessing the device’s software credential stores. This prevents the LaZagne malware from harvesting any credentials. Since John is a standard user, if his credential does fall into the wrong hands, it will be virtually useless for gaining access into the enterprise.
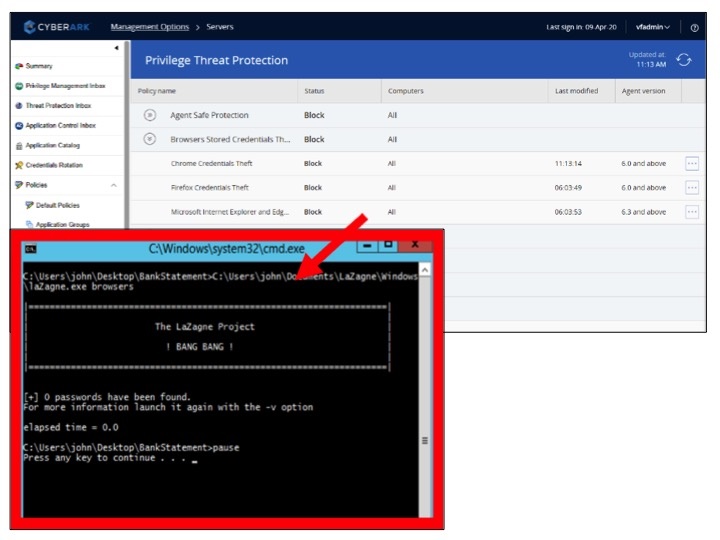
- When John tries to download an unknown application – for work or for personal use –on his device, CyberArk allows the application to run in a secure ‘restricted mode,’ preventing it from accessing corporate resources, sensitive data or the internet. CyberArk EPM can quickly calculate the application’s risk level and, if it’s categorized as “malicious,” a policy can be created to block it from running.
- During John’s remote work stint, security teams can easily enforce least privilege. There are two ways that to achieve this. One method is to leverage CyberArk Endpoint Privileged Manager privilege escalation functionality to elevate the authorized activities and applications based on policies. This covers 80% of the users’ day to day requirement. Endpoint Privileged Manager also offers an ad hoc mechanism which provides more flexibility with just-in-time access and elevation. By adding users to a “privilege group” for a limited time, security can provide an audit trail on the endpoint throughout the temporary period and revoke and terminate access at the end—or before if necessary. This is particularly useful today as organizations redeploy workers to focus on evolving business priorities and need a way to automatically provision and de-provision privileged credentials as responsibilities shift.
Forward-looking CISOs are mapping out their phased approach to risk reduction – not only for the coming crucial weeks, but also the months and years ahead. As we settle into this new normal, employee devices will play an even greater role in conducting business – and introducing new security challenges. In fact, the distributed patchwork of desktop computers, laptops, smartphones and tablets has become our lifeline to the outside world. Now, more than ever, it’s imperative to protect these devices and the access they provide.
Want to learn more about CyberArk Endpoint Privileged Manager? Get started with a free trial. Want to learn more about securing workstations and remote access? Visit CyberArk’s risk distancing resource page.






















