
From user-friendly web apps like Salesforce to IT-centered functions such as Windows Remote Desktop Protocol (RDP), today’s workplace tools can be extremely powerful. While a mix of both modern and traditional tools and technologies can help boost employee productivity and operational efficiency, they also introduce a host of new challenges for security and compliance teams in the form of expanded privileged access.
Privilege Is Everywhere
A privileged user is any user who has the capability to change or impact the operational service of a business process. This includes not only system administrators, but also users you may not intuitively consider “privileged.” Privileged access extends to applications, machines and service accounts connecting to other systems, as well as software robots as part of robotic process automation (RPA) workflows.
As enterprises shift more workloads to the cloud, double down on digital transformation initiatives and increasingly automate processes, the number of privileged users and accounts grows and the potential attack surface continues to expand. Each step forward creates new “doors” that must be locked.
Yet, too often, locking many of these “doors” is overlooked by organizations as they forge ahead, often focused on driving business agility. RPA and application credentials are often highly privileged, giving broad access to sensitive data and systems. When these credentials are not properly secured, they can open up the enterprise to unnecessary risk. Unfortunately, attackers understand this, and increasingly target these unprotected entranceways—seeking out powerful, unsecured credentials to accomplish their goals.
So how can you continue to innovate and evolve in this digital landscape—and do it securely? And how do you lock all of these “doors” to stay secure, without slowing down productivity? For many organizations, this can seem like an insurmountable challenge. That’s where native privileged session management comes in.
Benefits of Native Privileged Session Management
When you secure privileged accounts on both the user and system access levels, you limit the ability for an external attacker or malicious insider to use compromised credentials to bypass monitoring solutions and security controls. To do this effectively across on-premises, hybrid and cloud environments, you must identify the right tools that can not only mitigate risk, but also allow employees to keep using the tools they want—and need—to do their jobs.
Privileged session management is a foundational component of any privileged access management (PAM) program—giving organizations the ability to:
- Prevent cyberattacks by isolating end users from sensitive target machines.
- Create accountability and control over privileged session access with policies, workflows and privileged single sign-on capabilities.
- Deliver continuous monitoring and compliance with session recording without leaving a footprint on target machines.
With its advanced privileged session management capabilities, the CyberArk Privileged Access Security Solution provides end users the freedom to work with their favorite native tools and workflows, while simultaneously preventing credential exposure, isolating critical assets, automatically recording sessions and sorting sessions by risk to improve auditor productivity. We recently demonstrated a series of native deployment options, which include:
- Access to all systems and apps from the CyberArk web interface
- Native access for SSH and Windows admins
- Native access for cloud admins and privileged business users
Following are highlights from the demonstration. To explore additional use cases, check out our on-demand webinar: Enable Secure Productivity with Native Session Management.
Workflow 1: CyberArk Privileged Session Manager for Windows
We provide several options for establishing secure session connections for Windows: RDP Files, ActiveX, HTML5 Gateway and native access with the RDP Proxy. Based on user experience preferences, security considerations and industry regulations, organizations can choose which option works best for their environment.
Here’s a brief look at how to establish secure sessions via RDP.
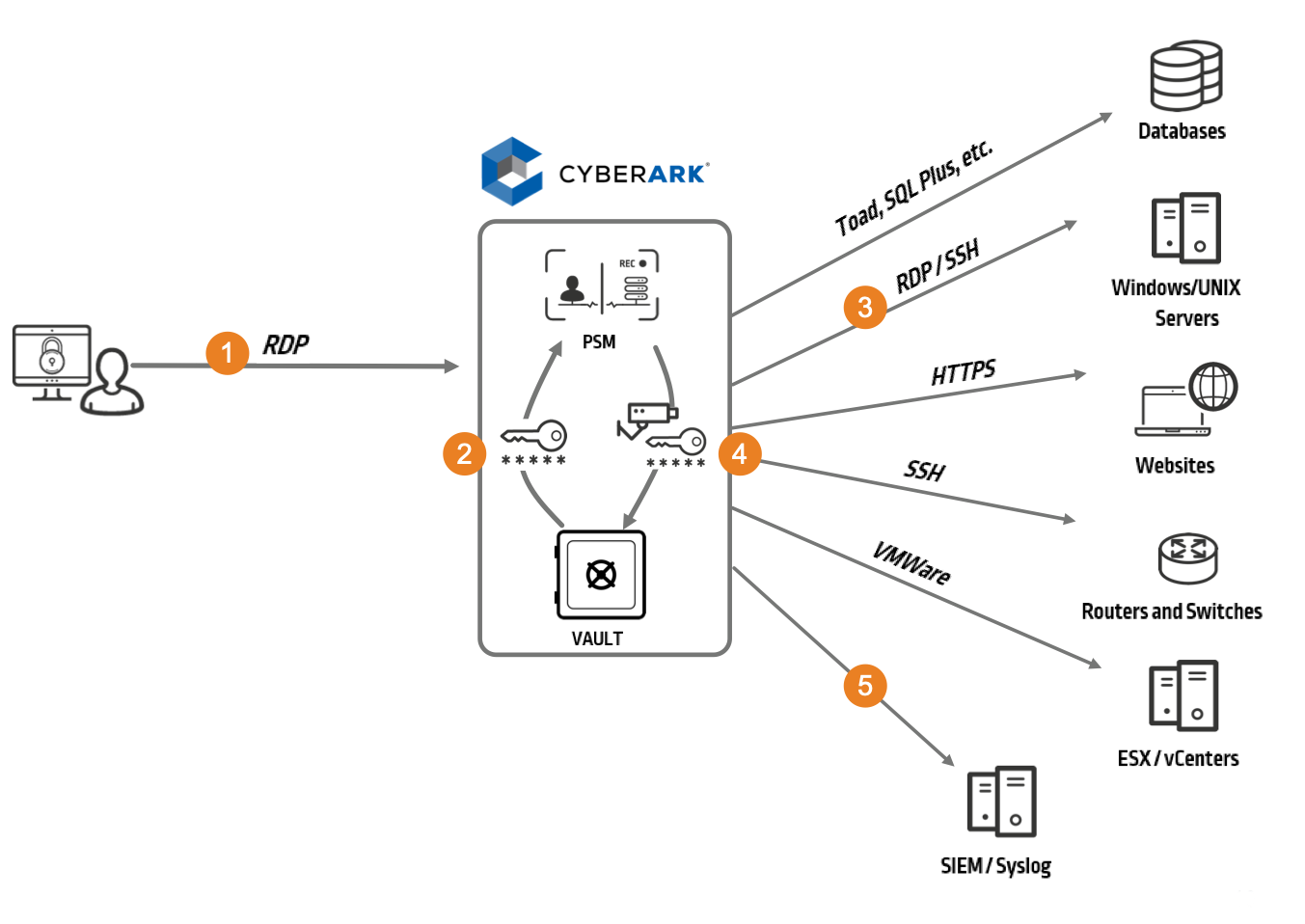
Figure 1: CyberArk Privileged Session Manager for Windows
Workflow 2: CyberArk Privileged Session Manager for SSH
CyberArk Privileged Session Manager for SSH enables organizations to secure, control, monitor and audit privileged access to things like network devices. It integrates with Microsoft Active Directory (AD) to provision users transparently on UNIX and Linux systems, streamline user management and reduce administrative overhead—without interrupting user workflow.
Privileged Session Manager for SSH can also restrict unauthorized commands executed by a privileged user on a network device or any SSH-based target system.
Similar to traditional Privileged Session Manager, this solution separates end users from target machines and initiates privileged sessions without divulging passwords or keys. Privileged Session Manager for SSH can also display a broad overview of all activity performed on every privileged account. All activities are fully monitored to help support strict auditing standards. Finally, the solution enables organizations to identify high-risk privileged sessions in real time, automatically suspend or terminate these sessions and initiate automatic credential rotation.
Here’s how it works.
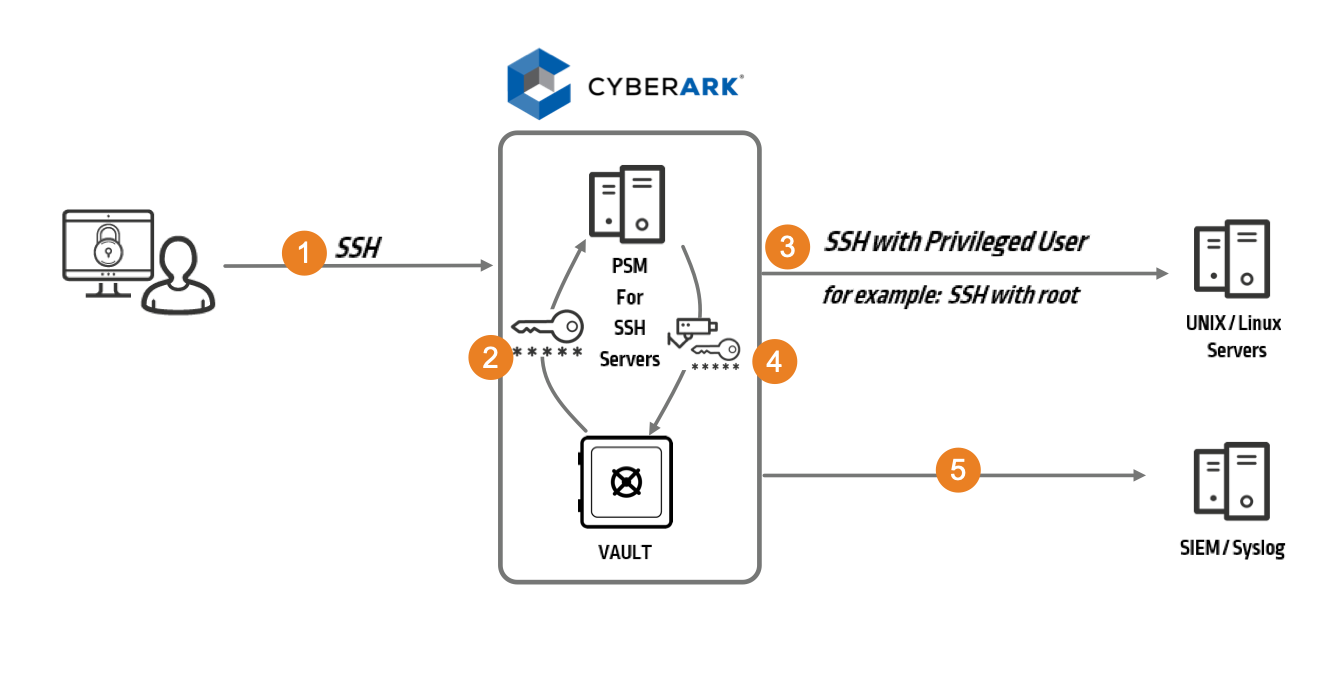
Figure 2: CyberArk Privileged Session Manager for SSH
Workflow 3: CyberArk Privileged Session Manager for Web
CyberArk Privileged Session Manager for Web provides true native, secure access to all major cloud platforms and web applications.
Organizations can trace user actions by creating a record of activity on cloud console administrative accounts, business critical applications like Salesforce and DevOps tools like OpenShift. Actions are traced directly back to individual authorized users to ensure accountability. This also helps identify weak areas of security and rogue employees that may be performing malicious activities. As with all CyberArk Privileged Session Manager use cases, organizations can assign risk scores to cloud console sessions and automatically alert security operations teams on high-risk activities.
The CyberArk solution supports all major cloud consoles and, with our Universal Connector Generator, organizations can easily create a web connector to support other platforms and custom—or proprietary—applications.
Let’s look at the workflow.
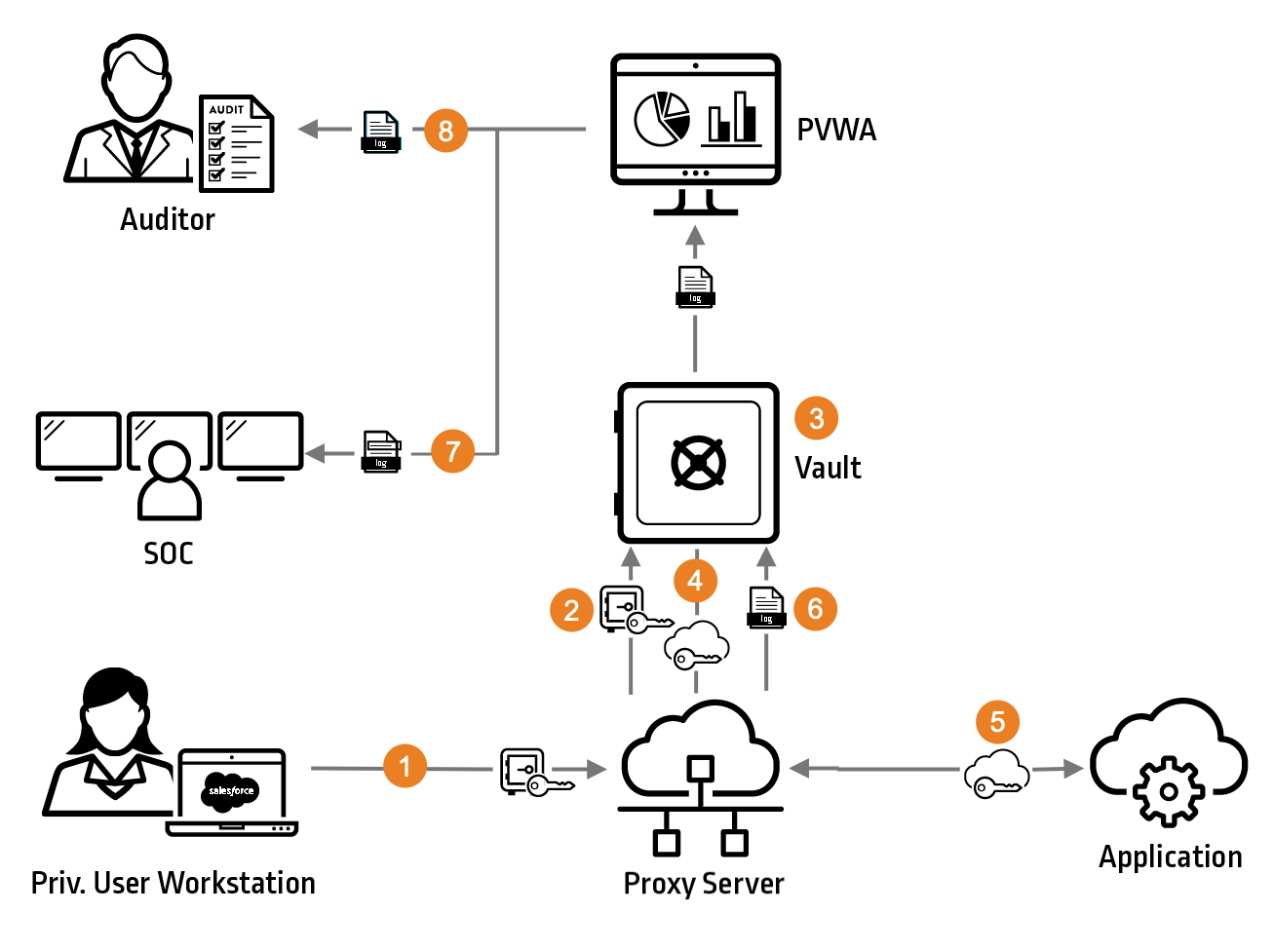
Figure 3: CyberArk Privileged Session Manager for Web
With CyberArk, you can implement secure, native access to Windows, UNIX and Linux, cloud, SaaS and web applications, social media and more. Learn more about unifying risk-based session review, mitigation and audit across hybrid environments while maximizing user productivity in our on-demand webinar or by requesting a demo.























