Cloud workload security refers to the practice of protecting applications, services, capabilities run on a cloud resource. Virtual machines, databases, containers and applications are all considered cloud workloads.
Cloud Deployment Models |
|
|---|---|
| Public Cloud | A public multitenant offering like Amazon Web Services (AWS), Microsoft Azure or Google Cloud Platform (GCP) |
| Private Cloud | A cloud environment dedicated to a single business entity (but typically shared by many organizations within that entity) |
| Hybrid Cloud | A combination of on-premises public and private cloud services |
| Multi Cloud | A combination of cloud services; typically includes multiple types of services (compute, storage, etc.) hosted on multiple public and private clouds |
Cloud Service Types |
|
| Infrastructure as a Service (IaaS) | On-demand, underlying compute, storage and networking services |
| Platform as a Service (PaaS) | Cloud-based application development environments and frameworks |
| Software as a Service (SaaS) | On-demand solutions like Salesforce or Office 365 that are delivered as a cloud-based applications with subscription-based licensing models |
Cloud Workloads are Vulnerable to a Variety of Threats
Cloud assets and workloads are susceptible to a wide variety of cybersecurity threats including data breaches, ransomware, DDoS attacks and phishing attacks. Cyber attackers can exploit cloud security vulnerabilities, using stolen credentials or compromised applications to mount attacks, disrupt services or steal sensitive data. Strong cloud security systems and practices are fundamental to maintaining the availability of business-critical applications, safeguarding confidential information and ensuring regulatory compliance.
Cloud Workload Security is a Shared Responsibility between the Cloud Provider and the Customer
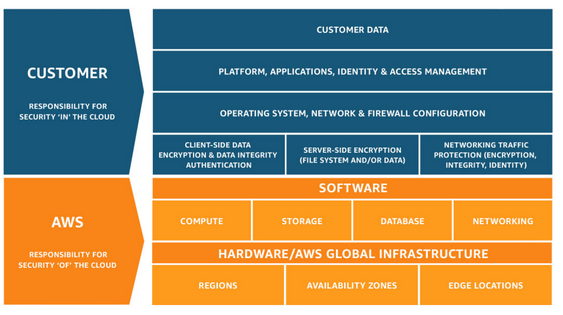
Cloud security practices are similar in many ways to traditional IT and network security practices, but there are some key differences. Unlike with conventional IT security, cloud security is typically governed by a shared responsibility model where the cloud service provider is responsible for managing the security of the underlying infrastructure (e.g. cloud storage services, cloud computing services, cloud networking services) and the customer is responsible for managing the security of everything above the hypervisor (e.g. guest operating systems, users, applications, data). The diagram below depicts the shared responsibility model mandated by AWS.
Security Best Practices for Cloud Customers
Cloud customers must institute a variety of security measures to protect cloud-based applications and data and mitigate security risks. Common cloud security best practices include:
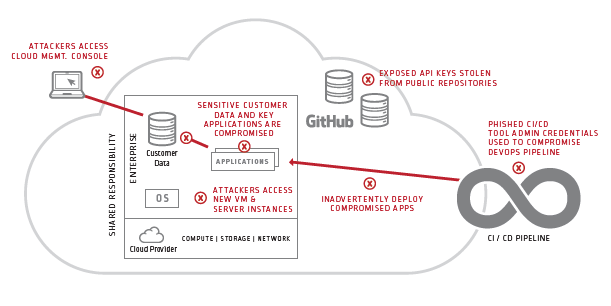
- Securing the cloud management console. All cloud providers provide management consoles for administering accounts, configuring services, troubleshooting problems and monitoring usage and billing. They are a frequent target for cyber attackers. Organizations must tightly control and monitor privileged access to the cloud management console to prevent attacks and data leakage.
- Securing virtual infrastructure. Virtual servers, data stores, containers and other cloud resources are also a common target for cyber attackers. Cyber attackers can try to exploit automated provisioning tools like Puppet, Chef and Ansible to mount attacks and disrupt services. Customers must put strong security systems and practices in place to prevent unauthorized access to cloud automation scripts and provisioning tools.
- Securing API SSH keys. Cloud apps commonly invoke APIs to stop or start servers, instantiate containers or make other environmental changes. API access credentials like SSH keys are often hard-coded into applications, placed in public repositories like GitHub and then targeted by malicious attackers. Organizations must remove embedded SSH keys from applications and ensure that only authorized applications have access to them.
- Securing the DevOps admin consoles and tools. Most DevOps organizations rely on a collection of CI/CD tools to develop and deploy applications in the cloud. Perpetrators often try to exploit DevOps admin consoles and tools to launch attacks or steal data. Customers must strictly control and track access to the tools and admin consoles used at each stage of the application development and delivery pipeline to mitigate risk.
- Securing the DevOps pipeline code. Attackers may also try to exploit cloud application vulnerabilities throughout the DevOps pipeline. Developers often hardcode security credentials into source code stored on shared storage or public code repositories. In the wrong hands, application credentials can be used to steal proprietary information or wreak havoc. Customers must remove secrets from source code and put systems and practices in place to automatically monitor and control access based on policy.
- Securing admin accounts for SaaS applications. Every SaaS offering includes a management console for administering users and services. SaaS admin accounts are a common mark for hackers and cybercriminals. Customers must tightly control and monitor SaaS admin console access privileges to ensure SaaS security and reduce risks.
- Securing Cloud Entitlements: Human and machine identities leverage Cloud IAM Permissions to access infrastructure and services in their organizations environments. In the hands of an attacker, excessive permissions can put sensitive data at risk. Customers should implement least privilege access to follow security best practices from major cloud providers. In certain cases, organizations should also consider dedicated Cloud Infrastructure Entitlements Management (CIEM) solutions.